10 Best Wiz Competitors and Alternatives for Cloud Security in 2026
Sorry, there were no results found for “”
Sorry, there were no results found for “”
Sorry, there were no results found for “”

Is Wiz giving you solid visibility but falling short on real-time remediation, host-level telemetry, or network traffic analysis?
Safe to say, you’re not the only one noticing the gaps.
As cloud environments become increasingly complex, security teams require tools that identify risks and help mitigate them.
This blog post breaks down some of the best Wiz competitors that fill in those missing pieces. Stick around till the end to see how ClickUp (yes, the productivity platform!) supports efficient cloud security collaboration. 🔐
When exploring the top alternatives to Wiz, start by identifying the specific gaps in your cybersecurity project management. The right solution will directly address those gaps and strengthen your overall security strategy. Here are some features to look out for:
🧠 Fun Fact: In 2013, AWS signed a $600 million deal with the CIA, setting the stage for secure cloud adoption in the public sector. It was the beginning of the now-booming GovCloud ecosystem.
Here’s a table comparing all Wiz competitors and alternatives. 📊
| Tool | Best for | Best features | Pricing* |
| Palo Alto Prisma Cloud | End-to-end cloud security and DevSecOps for mid-market to enterprise organizations | Cloud Security Posture Management (CSPM), Cloud Workload Protection (CWPP), Cloud Infrastructure Entitlement Management (CIEM), AI-powered risk prioritization | Custom pricing |
| Lacework | Polygraph behavioral anomaly detection and full-stack visibility for mid-market to enterprise organizations | Behavior-based anomaly detection, risk prioritization, automated compliance checks | Custom pricing |
| Orca Security | Agentless vulnerability management for small to mid-sized businesses with multi-cloud environments | Context-rich prioritization, attack path visualization, SideScanning technology | Custom pricing |
| Tenable | Broad vulnerability management across cloud and on-premise environments for enterprises | CSPM, unified vulnerability scanning, Infrastructure as Code (IaC) security | Custom pricing |
| Aqua Security Software | Cloud-native full-lifecycle security for small- to medium-sized IT teams and DevOps teams with container security needs | Container and Kubernetes runtime protection, serverless workloads, CI/CD pipeline integration | Custom pricing |
| Microsoft Defender for Cloud | Security management for mid-sized companies on Microsoft-based cloud environments | Native CSPM and CWP with centralized alerts, built-in regulatory standards and reporting, Azure integration | Custom pricing |
| Qualys | Agent-based and agentless security scanning for enterprises and large developer teams | Hybrid asset protection (cloud + legacy), centralized reporting, CSPM for multi-cloud | Custom pricing |
| Check Point | Integrated security and posture management for mid-market companies and enterprises | CSPM, cloud-native threat prevention, serverless security, third-party API support | Custom pricing |
| Sysdig | Kubernetes-heavy DevSecOps operations for small to mid-market companies | Incident forensics with eBPF, real-time threat detection, vulnerability prioritization | Custom pricing |
| Snyk | Dev-first security for code, containers, and IaC for large developer teams and enterprises | Shift-left security, developer-first workflows, CI/CD integration, | Free plan available; Paid plans start at $25/month |
Now, let’s dive deeper into the best Wiz competitors. 👇
Our editorial team follows a transparent, research-backed, and vendor-neutral process, so you can trust that our recommendations are based on real product value.
Here’s a detailed rundown of how we review software at ClickUp.
Prisma Cloud in Palo Alto Networks is a comprehensive Cloud-Native Application Protection Platform (CNAPP) designed to protect applications throughout their lifecycle, from code to cloud.
Using a combination of machine learning, advanced analytics, and Precision AI, it continuously scans infrastructure, application code, and workloads to detect misconfigurations, policy violations, and active threats.
It also integrates with Palo Alto’s broader security ecosystem, including Cortex XDR and WildFire, making building a unified security strategy easier.
Here’s what a G2 review had to say about this Wiz competitor:
What I like best about Prisma Access is its ability to provide consistent, cloud-delivered security across all users, regardless of location. The integration with other Palo Alto Networks tools like Cortex and Panorama makes it easier to manage and monitor security posture from a centralized dashboard.
🔍 Did You Know? In the early 1990s, websites were mostly HTTP. It wasn’t until 1994 that Netscape introduced HTTPS to encrypt browser traffic, prompting the earliest conversations around web security.
Lacework FortiCNAPP helps teams connect cloud risk signals with real-time threat detection, whether analyzing misconfigurations or determining how to securely store client information. It creates a seamless view of vulnerabilities, misconfigurations, and active threats across your entire cloud environment.
With native support across AWS, Azure, and Google Cloud, the platform continuously analyzes activity to surface early signs of ransomware, cryptojacking, and compromised credentials.
📮 ClickUp Insight: 74% of employees use two or more tools just to find the information they need—while jumping between emails, chat, notes, project management tools, and documentation. This constant context-switching wastes time and slows down productivity. As the everything app for work, ClickUp unifies all your work—email, chat, docs, tasks, and notes—into a single, searchable workspace, so everything is exactly where you need it.
Orca Security gives teams deep visibility into every layer of their cloud environment without the overhead of installing agents. It automatically correlates risks, such as misconfigurations, exposed APIs, identity issues, and vulnerabilities, to surface the most critical threats.
This tool combines real-time telemetry, professional communication, advanced risk prioritization, and broad compliance support into a single interface.
Its focus on ‘toxic combinations’ helps teams prioritize the 1% of alerts that truly matter, cutting through the noise often associated with cloud security tools.
A user shared this review on Capterra:
Orca is an agentless approach to VMS. This means there is 0 user impact or performance degradation. Your Operations team does not have to manage agent roll out, it also does not need to manage upgrades/downtime. […] The product is fairly new and a lot of these enhancements are being worked on.
🧠 Fun Fact: The concept of ‘zero trust’ came from Forrester analyst John Kindervag, who suggested organizations should never trust any network by default. It took over a decade (and some painful breaches) for the idea to go mainstream.
Tenable brings a consolidated approach to securing hybrid and multi-cloud environments through its flagship exposure management platform, Tenable One. Instead of treating vulnerabilities, misconfigurations, and identity issues as isolated problems, Tenable connects the dots to provide a prioritized view of risks across your entire attack surface.
It supports FedRAMP-authorized solutions, making it a trusted choice for government and highly regulated environments. The tool also features capabilities such as just-in-time (JIT) access, autonomous patching, and AI-layered analytics.
Aqua Security helps secure modern applications across their entire lifecycle, from development and deployment to runtime. Its real-time controls and shift-left scanning empower security teams to catch vulnerabilities early and respond quickly to active threats without slowing down agile development pipelines.
This Wiz alternative uses a combination of agentless and agent-based methods to provide flexibility in deployment and coverage. It enables the unification of code, infrastructure, and workload security across hybrid and multi-cloud environments.
Here’s a quick snippet from a real user:
It’s ease of deployment, nice UI, CI/CD integration options available, good dashboard and one of the key features for us would be Kubernetes security feature which is not there in a lot of other commercial tools. But the licensing model is probably in line with Aquasec’s long term plan and they should also consider some short term/low volume pricing models for clients who want to try container security before deciding for a long term full fledged solution.
🧠 Fun Fact: Though the concept existed before, Google CEO Eric Schmidt used the phrase ‘cloud computing’ at a 2006 conference. It took off from there (and so did the security concerns).
Microsoft Defender for Cloud combines security posture management, workload protection, and DevSecOps capabilities.
Through Microsoft Defender Extended Detection and Response (XDR), organizations can connect insights from cloud infrastructure with alerts from endpoints and user identities, building a broader threat picture.
Its Secure Score feature gives organizations a clear metric to track and improve their overall security posture over time. You can also model potential attack paths with Cloud Security Explorer and implement governance rules across business units.
🔍 Did You Know? One of the earliest DevSecOps wins came from Netflix’s open-source tools. Netflix released Security Monkey and Stethoscope back in the 2010s, pioneering the idea of building security into CI/CD pipelines and influencing the future of automated CSPM tools and Wiz competitors.
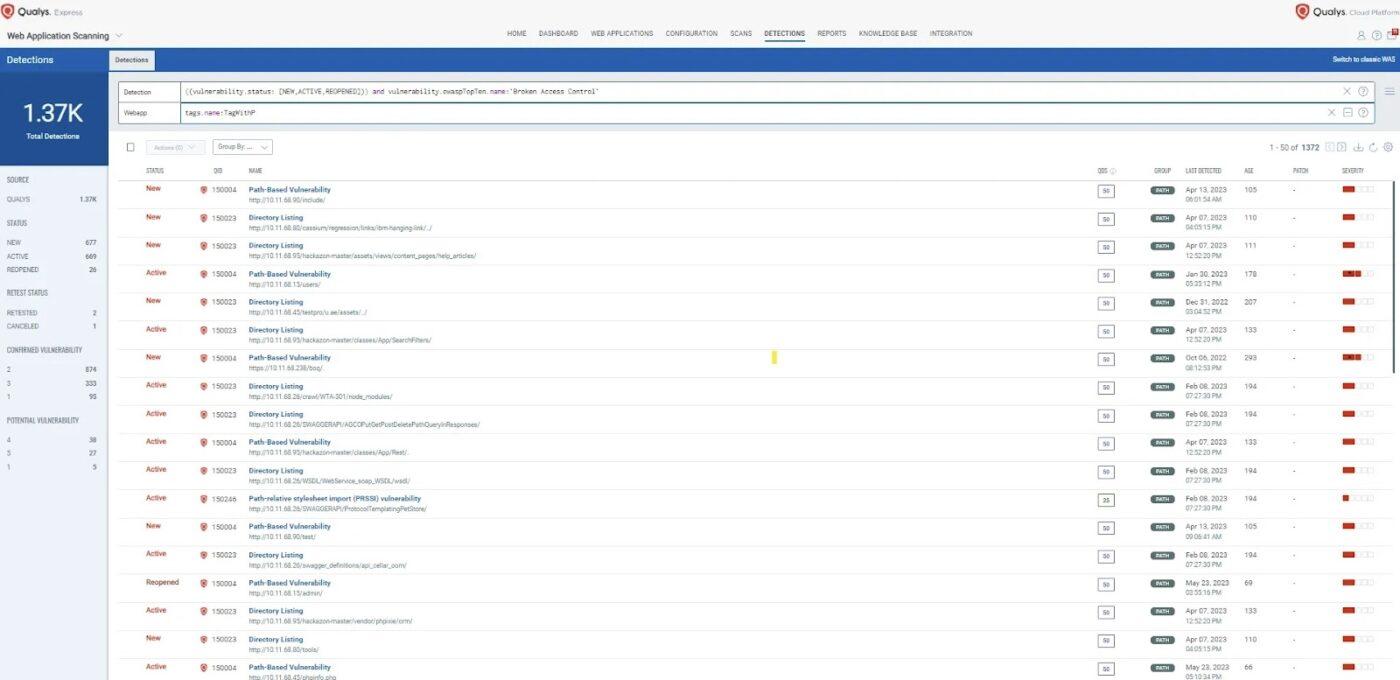
Qualys delivers a unified approach to cybersecurity with its Enterprise TruRisk™ Platform, combining asset visibility, vulnerability management, compliance, and remediation into one seamless system. The Wiz competitor offers high-speed telemetry and intelligent correlation across billions of data points.
The platform utilizes lightweight Cloud Agents and agentless scanners to provide comprehensive visibility and security assessment of cloud workloads, containers, and infrastructure. With the introduction of Qualys TotalCloud, its CNAPP and TotalAppSec for application risk, Qualys extends protection across the whole stack.
The platform supports IaC security, Kubernetes runtime protection, and even LLM safety for GenAI deployments.
One Capterra review puts it this way:
Overall, the product is user-friendly with robust vulnerability scanning and has a large library of software updates. Along with training videos and support.
Check Point’s flagship Quantum Security Gateways and CloudGuard solutions are designed to provide deep protection across networks, workloads, and remote access points.
For endpoint protection, Harmony Endpoint delivers EPP (Endpoint Protection Platform), EDR (Endpoint Detection and Response), and XDR (Extended Detection and Response) in a single lightweight client, offering comprehensive visibility and control from the edge to the cloud.
It allows teams to apply consistent security policies and protect against sophisticated cyberattacks across their entire cloud footprint, from infrastructure to applications.
Sysdig is a cloud-native application protection platform designed for teams that prioritize real-time detection, contextual risk insights, and deep runtime visibility, while enforcing robust data security measures.
Its multi-cloud support and managed Prometheus monitoring help it deliver end-to-end visibility across your infrastructure without context switching.
By combining security, compliance, and performance monitoring, Sysdig helps teams understand the full context of an incident. Its key differentiator is the ability to prioritize vulnerabilities based on whether the vulnerable package is actually in use at runtime, allowing teams to focus their remediation efforts
A G2 review summed it up like this:
Sysdig detected and alerted us to the testing within a few moments, and the competitor took hours. That was when we knew Sysdig would be the better option for us. On top of being able to rapidly detect, alert, triage, and investigate cloud and host threats, we have a slew of additional features that improve our security posture overall.
🧠 Fun Fact: According to IBM’s Cost of a Data Breach Report 2024, organizations that extensively implemented security AI and automation saved an average of $2.2 million in breach-related costs compared to those that did not.
via Snyk
Snyk is a developer-focused security platform with a modern approach to application security that fits seamlessly into fast-paced, cloud-native development workflows.
It stands out with its AI-powered security platform that detects and remediates vulnerabilities across the entire software development lifecycle. The Wiz alternative’s core engine, DeepCode AI, drives smart, explainable remediation and helps teams stay ahead of potential risks introduced by GenAI tools and open source libraries.
🔍 Did You Know? In 2019, a misconfigured firewall in Capital One’s AWS setup let a former AWS employee access over 100 million customer records. The root cause? A server-side request forgery (SSRF) vulnerability, something Wiz competitors specifically flag now.
Identifying risks with Wiz competitors is just the first step. The bigger challenge lies in what comes after: organizing the response, assigning tasks to the right teams, and tracking progress.
That’s where ClickUp steps in, not as a security scanner, but as a command center for orchestrating everything that happens after the scan. At its core is the ClickUp Project Management Software, which offers a centralized platform for planning remediation efforts, monitoring progress, managing documentation, and communicating in real time.
For IT and security teams operating at scale, ClickUp’s IT and PMO Solution enables PMO teams to standardize service request intake, automate SLA-driven escalations, and provide visibility into resource utilization across portfolios with enterprise-grade controls.
Let’s look at how ClickUp complements Wiz competitors throughout the operational lifecycle. 🔄
Once issues are flagged, they need to be brought into an actionable workflow.
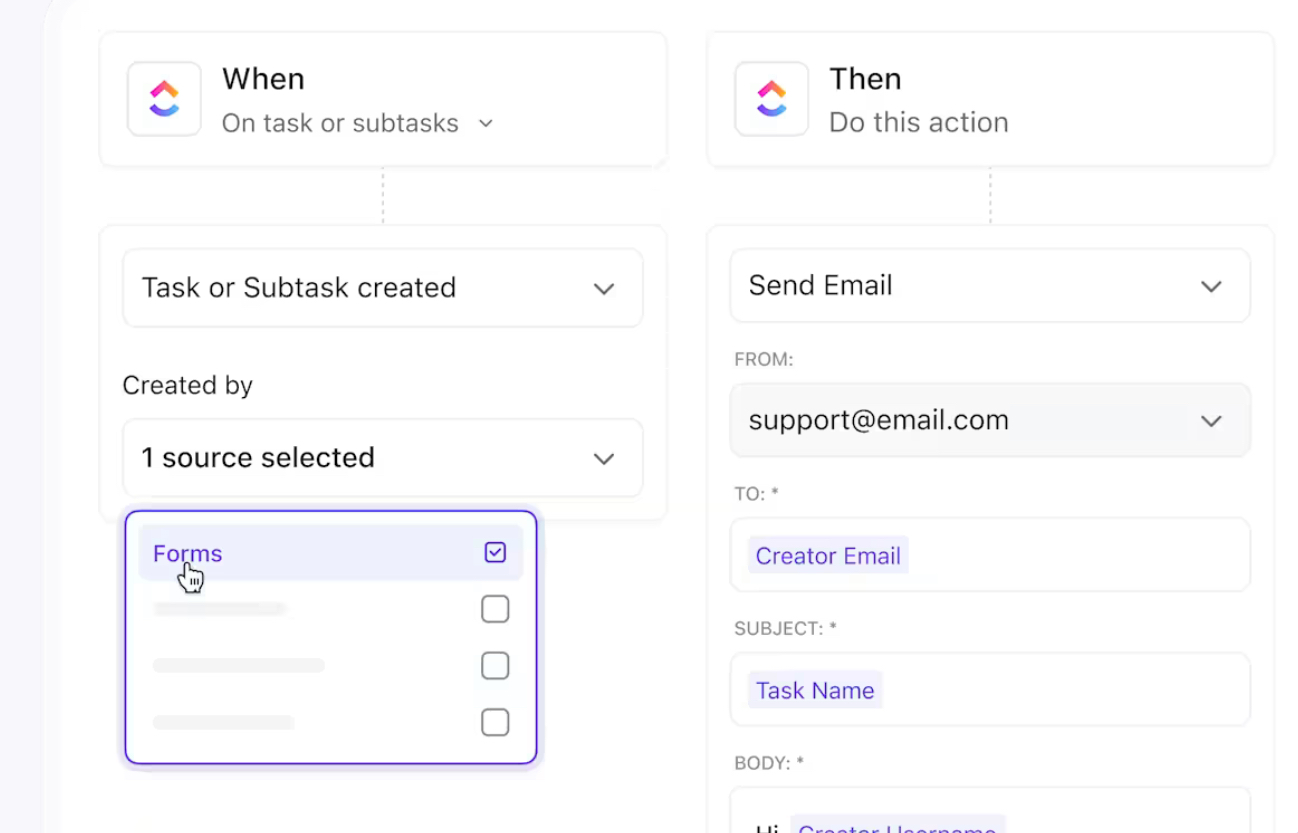
ClickUp Forms makes each vulnerability actionable by turning it into a task in ClickUp Tasks, complete with details about severity, affected systems, and target dates. This ensures consistent metadata capture for tracking and prioritization.
Once issues are in the pipeline, ClickUp Multiple Assignees and ClickUp Custom Fields make it easy to assign, organize, and track remediation from start to finish.
📌 Example: The security team fills out a form to submit an issue, automatically creating a task in ClickUp with predefined Custom Fields like ‘Network’ or ‘Compliance’. Even better? Both the network engineer and the compliance officer can be assigned to work on the task at once.
ClickUp Automations adds another layer of efficiency. Tasks can be auto-assigned based on severity, escalated if idle, or moved through workflows without manual handoffs using ClickUp’s intuitive if‑then builder.
A few workflow automation examples include:

📌 Example: When a critical vulnerability is detected, an automation can instantly assign the task to the security lead based on its severity, apply the correct priority, and set a due date. If the task remains unresolved after 48 hours, it can automatically escalate to the CISO.
When remediation starts, updates can fly in from every direction.
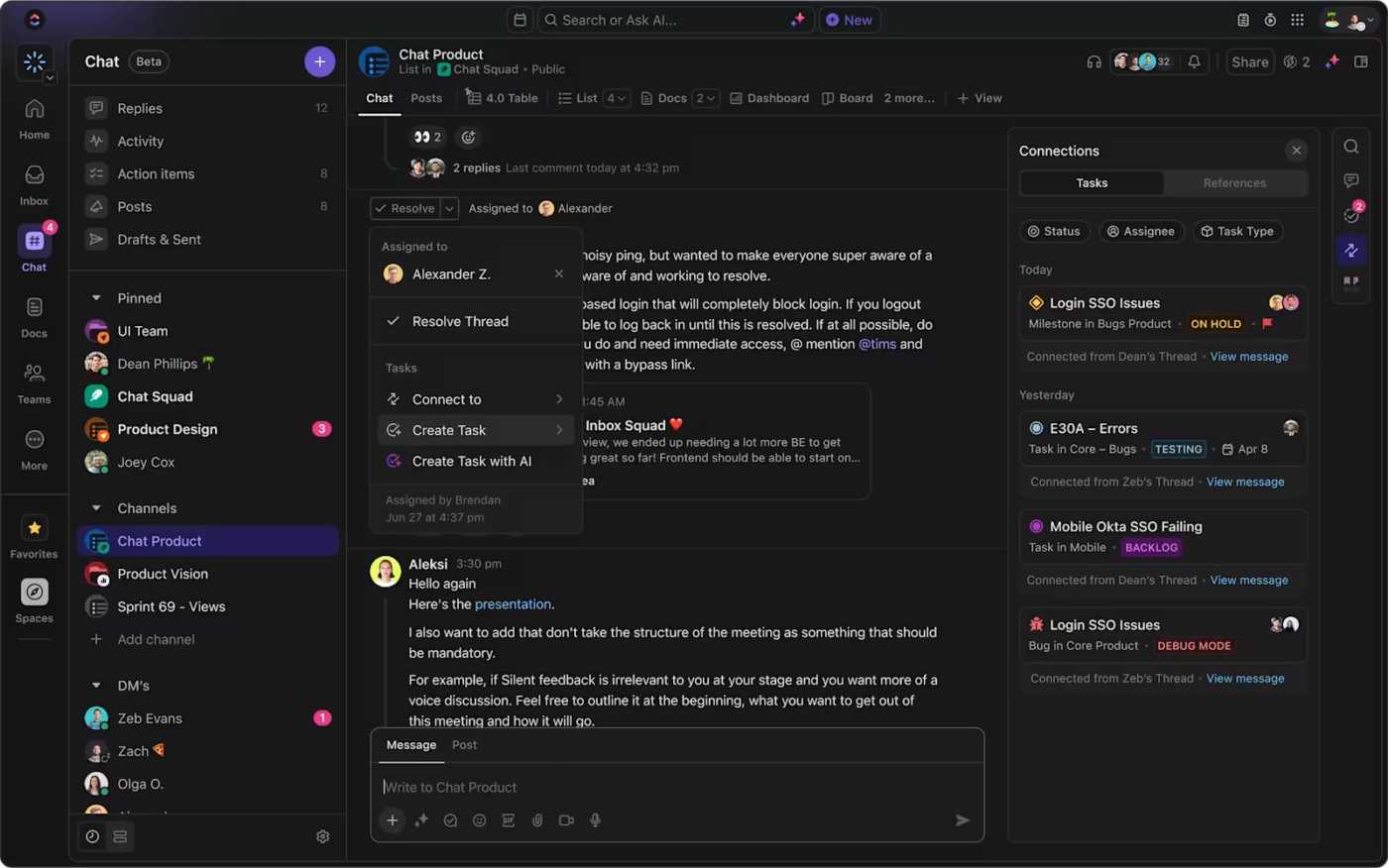
ClickUp Chat keeps those conversations right where the work happens—alongside tasks, docs, and timelines. Conversations can be converted into Tasks with a click, tagged appropriately, and maintained in full context to keep audit logs intact.
📌 Example: Let’s say a high-risk vulnerability is flagged and a fix is in progress. The security lead drops a quick update in the project chat, tags the engineer, and links the task directly in the message.
If the fix requires follow-up, that message can be converted into a new task instantly, carrying over the assignee, deadline, and any files shared in the secure collaboration tool.
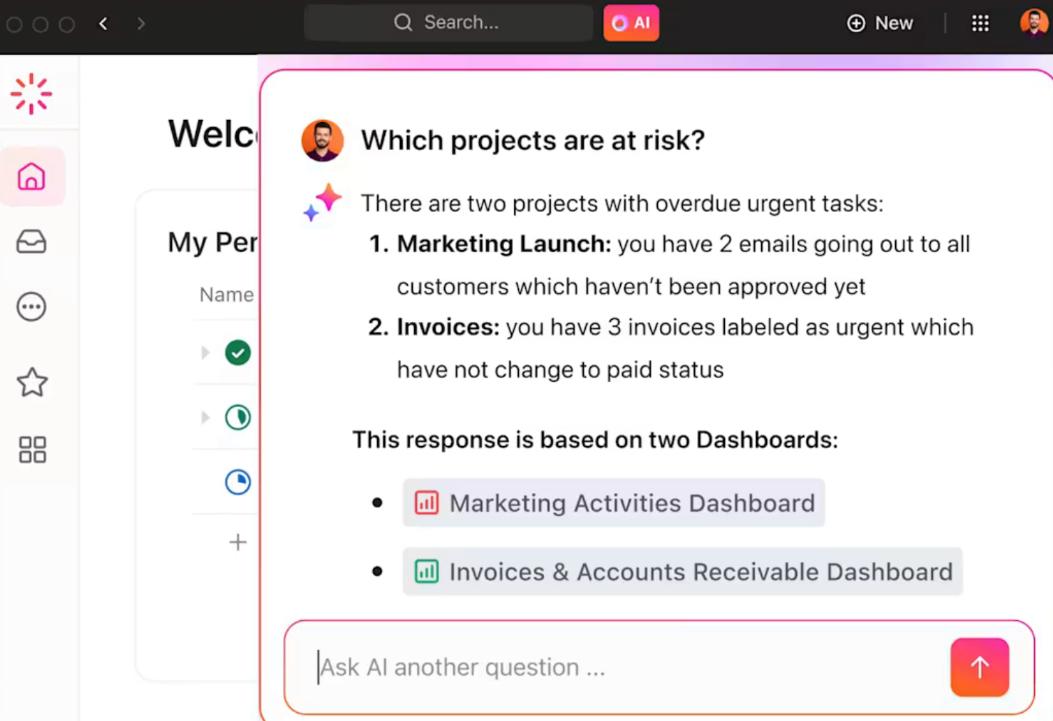
ClickUp Brain, your AI-powered assistant, uses ongoing task activity, comments, docs, and chat history to deliver actionable insights. It helps by:
This G2 review really says it all:
What I like best about ClickUp is its customization and flexibility. Whether it’s creating tailored workflows for different teams (like marketing and web development), using custom fields to track specific project details, or automating repetitive tasks, ClickUp allows me to adapt it to our exact needs. It helps keep everything in one place, making project management and communication seamless across teams. Plus, the integrations and automations save us so much time, allowing us to focus on what truly matters.
📮 ClickUp Insight: 30% of workers believe automation could save them 1-2 hours per week, while 19% estimate it could unlock 3–5 hours for deep, focused work.
Even those small time savings add up: just two hours reclaimed weekly equals over 100 hours annually—time that could be dedicated to creativity, strategic thinking, or personal growth.💯
With ClickUp’s AI Agents and ClickUp Brain, you can automate workflows, generate project updates, and transform your meeting notes into actionable next steps—all within the same platform. No need for extra tools or integrations—ClickUp brings everything you need to automate and optimize your workday in one place.
💫 Real Results: RevPartners slashed 50% of their SaaS costs by consolidating three tools into ClickUp—getting a unified platform with more features, tighter collaboration, and a single source of truth that’s easier to manage and scale.
Whether you’re looking for stronger runtime protection, more actionable threat intel, or better compliance support, the Wiz competitors we explored each offer a distinct edge.
But here’s the bigger picture: comprehensive cloud security doesn’t live in isolation. You need a reliable solution to keep teams aligned, activities visible, and data accessible. That’s where ClickUp stands out.
As the everything app for work, it helps security teams align projects, processes, and people in one place. From managing remediation workflows and audits to automating tasks and leveraging AI through ClickUp Brain, it’s built to bring order to even the most complex environments.
Why wait? Sign up to ClickUp for free today!
© 2026 ClickUp