Compliance with security frameworks, such as System and Organization Controls 2 (SOC 2), acts as a protective shield for sensitive data. Cybersecurity threats get more sophisticated by the day, and proper security measures are the best way to guard against them.
This is not only an ethical obligation to customers but a critical business obligation. A data breach can lead to loss of confidential information and loss of trust among customers. In some areas, there are even legal requirements to secure data according to a specific framework’s standards.
Today’s tech stacks deal with large amounts of data from many disparate sources. Keeping track of everything, and doing so in a way that keeps you compliant, can be a Herculean task. Thankfully, there are software products on the market that can automate many of these tasks and make keeping on top of data compliance a much more achievable goal.
In this article, we’ll talk about the best products for securing your data to the SOC 2 standard. Some of these tools also support other data security standards you may need to follow as well!
What is SOC 2 Compliance?
SOC 2 is a framework that defines criteria for managing customer data according to five trust service principles. Those principles are security, availability, processing integrity, confidentiality, and privacy.
SOC 2 compliance is necessary for any businesses that store customer data in the cloud. It ensures the security and integrity of information. Achieving and maintaining SOC 2 compliance demonstrates to customers and stakeholders that an organization has robust security controls in place to protect their data.
What Should You Look for in SOC 2 Compliance Software?
As you look for SOC 2 compliance tools for your company, your priority will be simplifying the time-consuming audit process in a way that fits well with your existing workflow and culture. But there are other important features to look for, such as:
- Automated evidence collection: By reducing manual evidence gathering, the software will save you time and streamline audits
- Risk assessment tools: Regular risk assessments are one of the most important aspects of cybersecurity, so a thorough set of tools for this is helpful
- Vendor management: Third-party vendors can be a source of security vulnerabilities. The software you choose should help you evaluate vendor security
- Security training modules: Training is the first step to a solid security foundation, whether this is initial employee onboarding or ongoing security training
- Automated monitoring: Automation reduces the need for manual work and ensures continuous compliance by giving a 24/7 view of your compliance
- Custom controls: The ability to tailor controls to your specific business needs will help ensure the software grows along with your business
- Integration with tech stack: Ensuring your compliance software works with the other tools in your stack allows you to pull in data from multiple sources
- Fast audit capabilities: Good SOC 2 compliance tools enable faster audits by efficiently handling evidence requests and reducing back and forth with auditors
The 7 Best SOC 2 Compliance Software to Use
Choosing the right SOC 2 compliance software can give your business a head-start for developing a successful compliance program that follows evolving standards. To help you find the right security and compliance software for your company, we’ve assembled this list of the top options on the market.
1. Drata
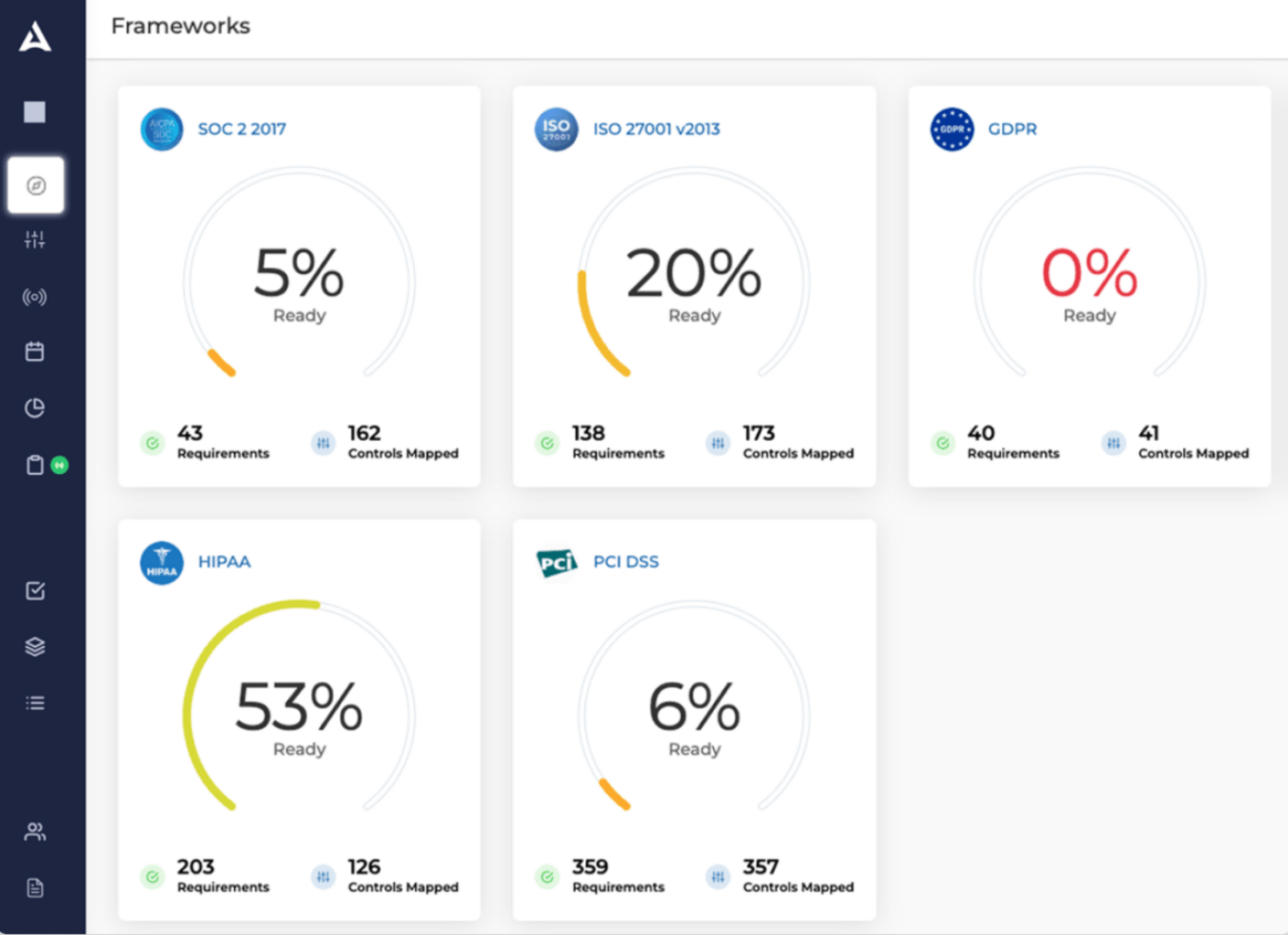
Drata automates compliance for businesses, making it easier for them to achieve and maintain SOC 2 compliance. This platform puts a strong focus on its ability to automatically collect evidence from a company’s tech stack.
This is a time-consuming process for many organizations. Automating it speeds up the compliance process while also ensuring that the collected evidence is accurate and up to date. For fast-growing companies, this is a must-have, as it allows them to demonstrate to their customers how seriously they take security and compliance without requiring a significant amount of manual effort.
Drata best features
- Automates evidence collection and testing with expertly designed compliance automation tools
- Manages SOC 2 and other frameworks, such as ISO 27001, HIPAA, GDPR, and more, through a centralized location
- Ensures ongoing compliance and increased data security through continuous monitoring
- Offers customization options that adapt to your needs as your company scales, including framework and control customization
- Provides you with the help you need quickly with Drata’s team of security and compliance experts
- Integrates with other software to further automate evidence collection and maintain compliance
Drata limitations
- Some users feel the price point is high for businesses with simple needs
- Some customers look for better collaboration tools
Drata pricing
- Contact sales for pricing
Drata ratings and reviews
- G2: 4.9/5 (500+ reviews)
- Capterra: 5/5 (1 review)
Check out these Drata alternatives!
2. JupiterOne
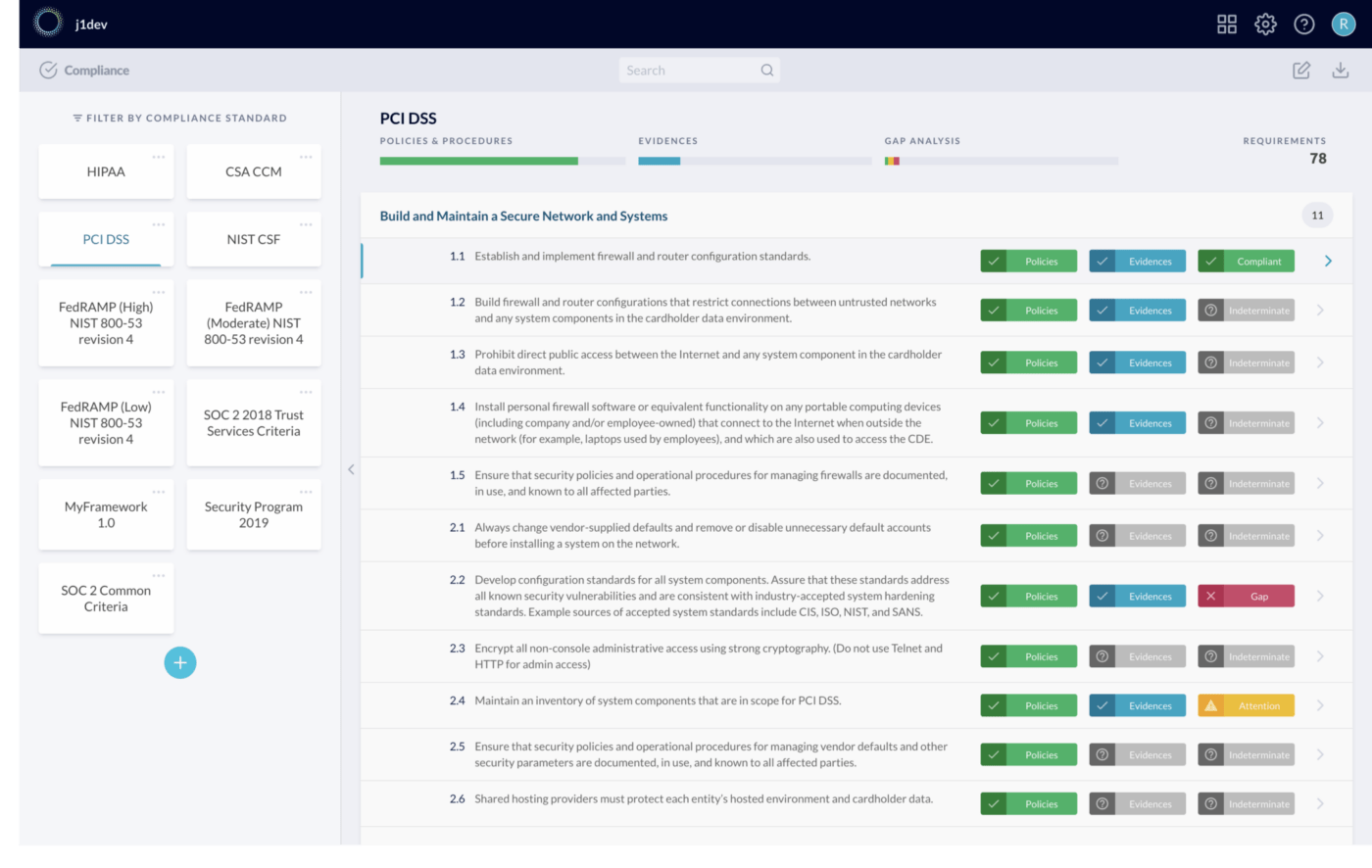
This software also takes a holistic approach to building a security program. By integrating with the entire tech stack of a business, JupiterOne offers better risk management.
These integrations allow the software to automatically collect evidence for compliance audits. This takes the hassle out of compliance management and provides peace of mind. The software also features vendor management tools to help mitigate the risks associated with bringing in third-party vendors.
JupiterOne best features
- Automatically discovers and tracks all assets across various data sources, providing a single location for compliance data
- Provides a powerful search through the JupiterOne Query Language to enable faster search and analysis of compliance information
- Makes relationships between assets easily identifiable with graph-based visualization
- Allows for granular segmentation of security data through the use of customizable and comprehensive tagging
- Promotes a continuous compliance posture by mapping assets to a security standard and allowing for customization of standards and mappings
- Allows users to create dashboards to report on security posture and set up alerts for various security events
JupiterOne limitations
- Users found the initial learning curve a bit steep
- Some customers expressed a desire for more integration options
JupiterOne pricing
- Free Forever for one user
- Base: from $1,000/month for unlimited users
- Plus: from $1,250/month for unlimited users
- Enterprise: from $1,600/month for unlimited users
JupiterOne ratings and reviews
- G2: 4.9/5 (5 reviews)
- Capterra: 5/5 (5 reviews)
3. Vanta
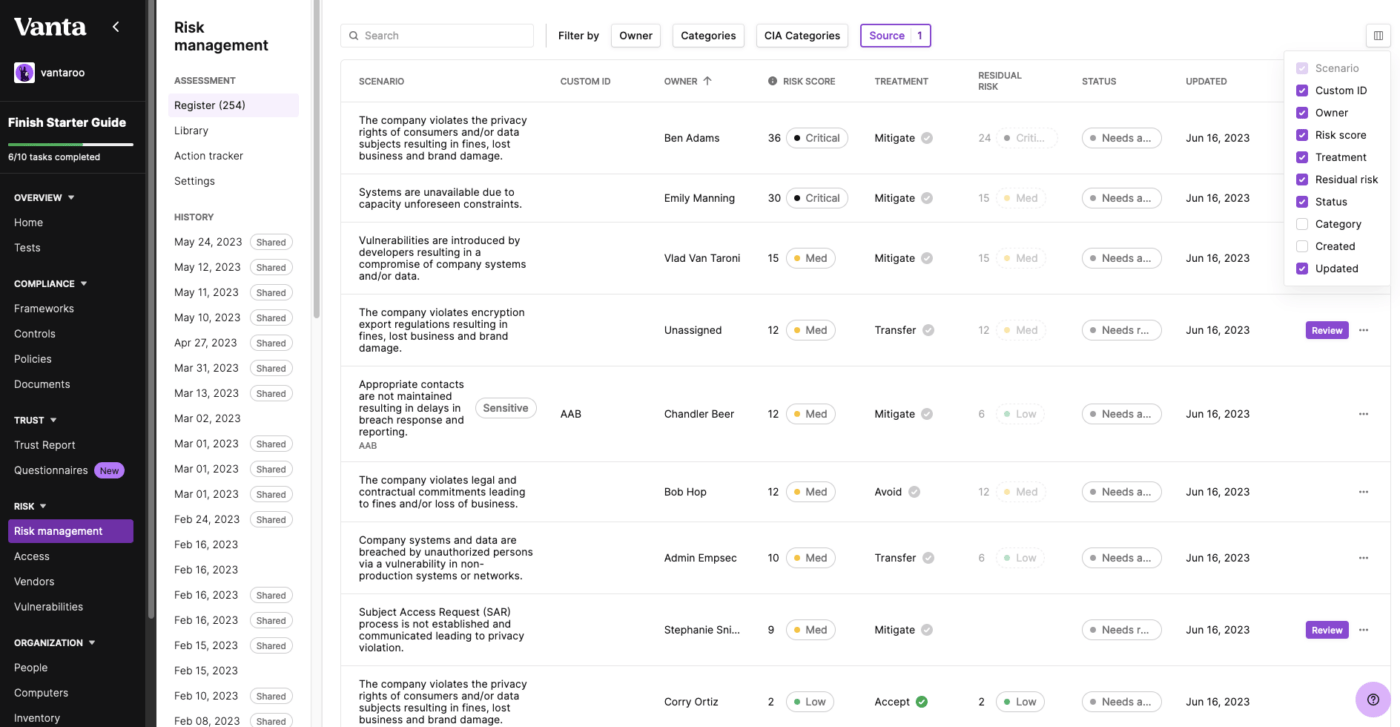
This product simplifies the compliance process for companies with automated compliance solutions. Vanta helps businesses prepare for compliance audits for SOC 2 compliance or one of the other popular security frameworks.
The software produces readiness assessments that allow companies to understand their current position and proactive ways to improve. Staying on top of the risk assessments allows businesses to better prepare for any potential audits.
Vanta best features
- Offers hourly tests to monitor the state of your security posture and provides alerts for any discrepancies
- Includes pre-built integrations and an API for creating custom connections that allow for a holistic view of data compliance
- Streamlines the audit process, simplifying auditor selection and enabling the completion of audits right from within the platform
- Automates up to 90% of the work necessary for multiple frameworks, ensuring efficient compliance and risk management
- Allows for the creation of custom frameworks for specific controls and policies
- Enables businesses to proactively share details about their security and compliance program to build trust with stakeholders
Vanta limitations
- The price is a bit higher than some people would like
- It takes a while to get up to speed with all the options
Vanta pricing
- Contact sales for pricing
Vanta ratings and reviews
- G2: 4.6/5 (700+ reviews)
- Capterra: 4.9/5 (16 reviews)
Check out these Vanta alternatives!
4. Thoropass
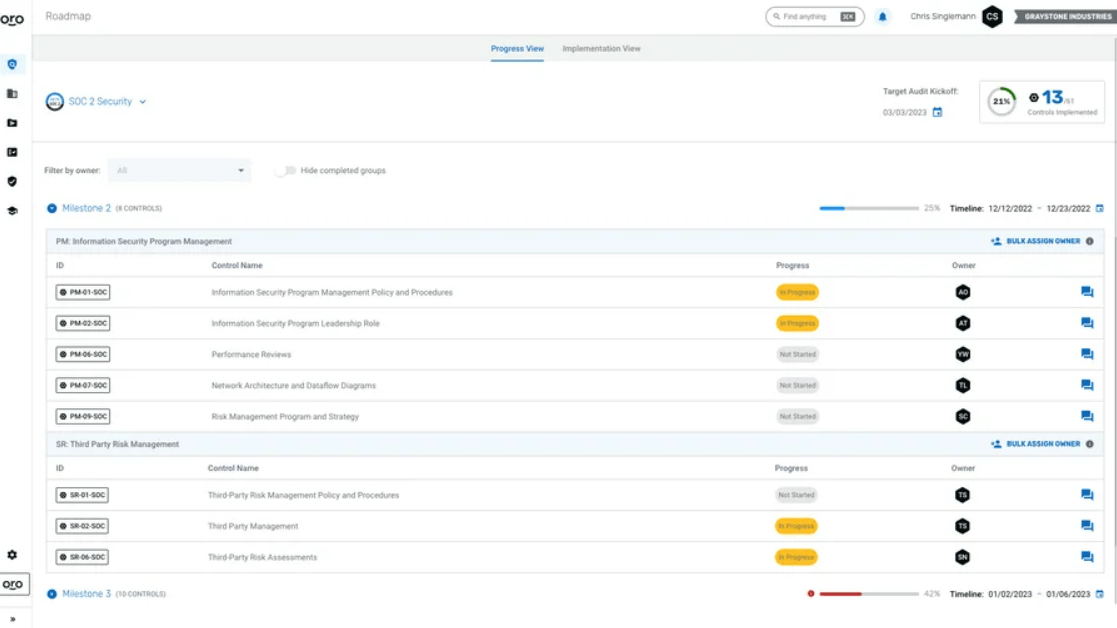
This SOC2 compliance software places a strong emphasis on access management. Thoropass ensures that only authorized individuals have access to sensitive systems and data. For example, you can monitor and revoke access for former employees, ensuring that business data remains secure after employees leave.
Of course, Thoropass provides a host of other features as well (enough to handle all of your compliance needs). The extensive set of integrations ensures a complete picture of your security posture.
Thoropass best features
- Offers compliance solutions specific to individual challenges, so businesses get the right compliance support everywhere on the compliance journey
- Supports multiple frameworks, including SOC 2, ISO 27001, PCI DSS, HITRUST, HIPAA, and GDPR, all on a single platform
- Delivers a hassle-free audit experience by managing 100% of the audit within the platform and providing a 67% faster time-to-audit on average
- Integrates with other software to collect data and evidence that’s important to the compliance process
- Provides in-house experts ready to offer timely support and future-proof strategies for long-term compliance needs
Thoropass limitations
- Some users want more automation options
- The interface can be cumbersome in some areas
Thoropass pricing
- Contact sales for pricing
Thoropass ratings and reviews
- G2: 4.7/5 (200+ reviews)
5. Secureframe
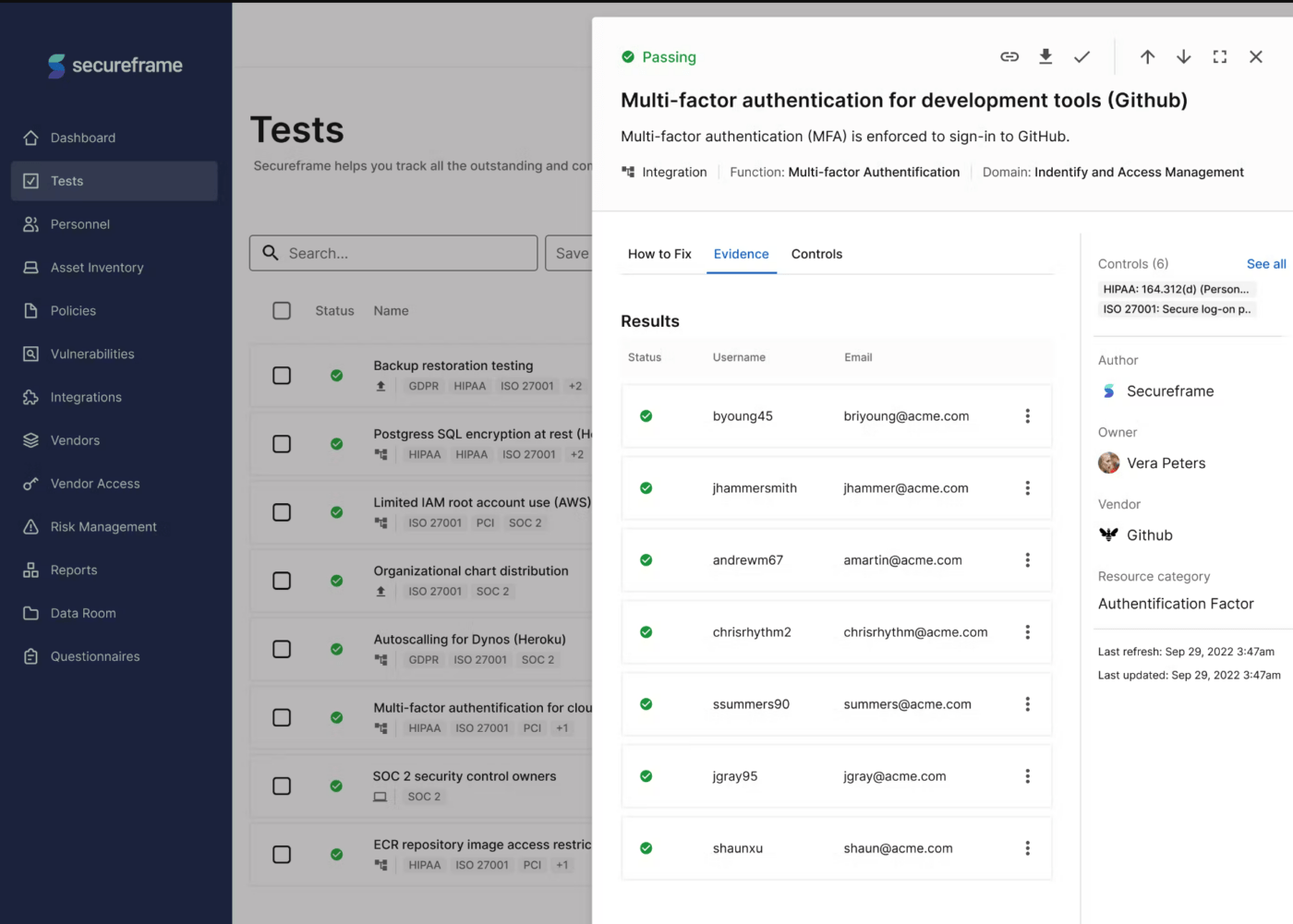
Secureframe aims to help businesses achieve compliance with some of the world’s most rigorous security standards. Its strength lies in its automated compliance capabilities, which reduce the time-consuming task of gathering evidence.
Powerful AI algorithms that aid users through all aspects of security augment this software’s capabilities. Additionally, tools for onboarding and offboarding keep employees in the know. Policy acceptance tracking ensures everyone is adhering to an organization’s security policies.
Secureframe best features
- Offers continuous tracking of assets and employees in one place, providing insight into who has access to sensitive data
- Enhances security with tools to manage failing controls, assess risk, and improve your security posture
- Uses artificial intelligence to automate manual tasks, streamlining the management of security, risk, and compliance
- Automates and streamlines the entire compliance process, allowing businesses to quickly become compliant
- Supports a range of security and privacy standards, including SOC 2, ISO 27001, HIPAA, PCI DSS, GDPR, and more
Secureframe limitations
- Some users want more customization options
- There are some integrations missing that customers want
Secureframe pricing
- Essentials: Contact sales for pricing
- Growth: Contact sales for pricing
- Premium: Contact sales for pricing
- Enterprise: Contact sales for pricing
Secureframe ratings and reviews
- Capterra: 5/5 (4 reviews)
6. Scytale
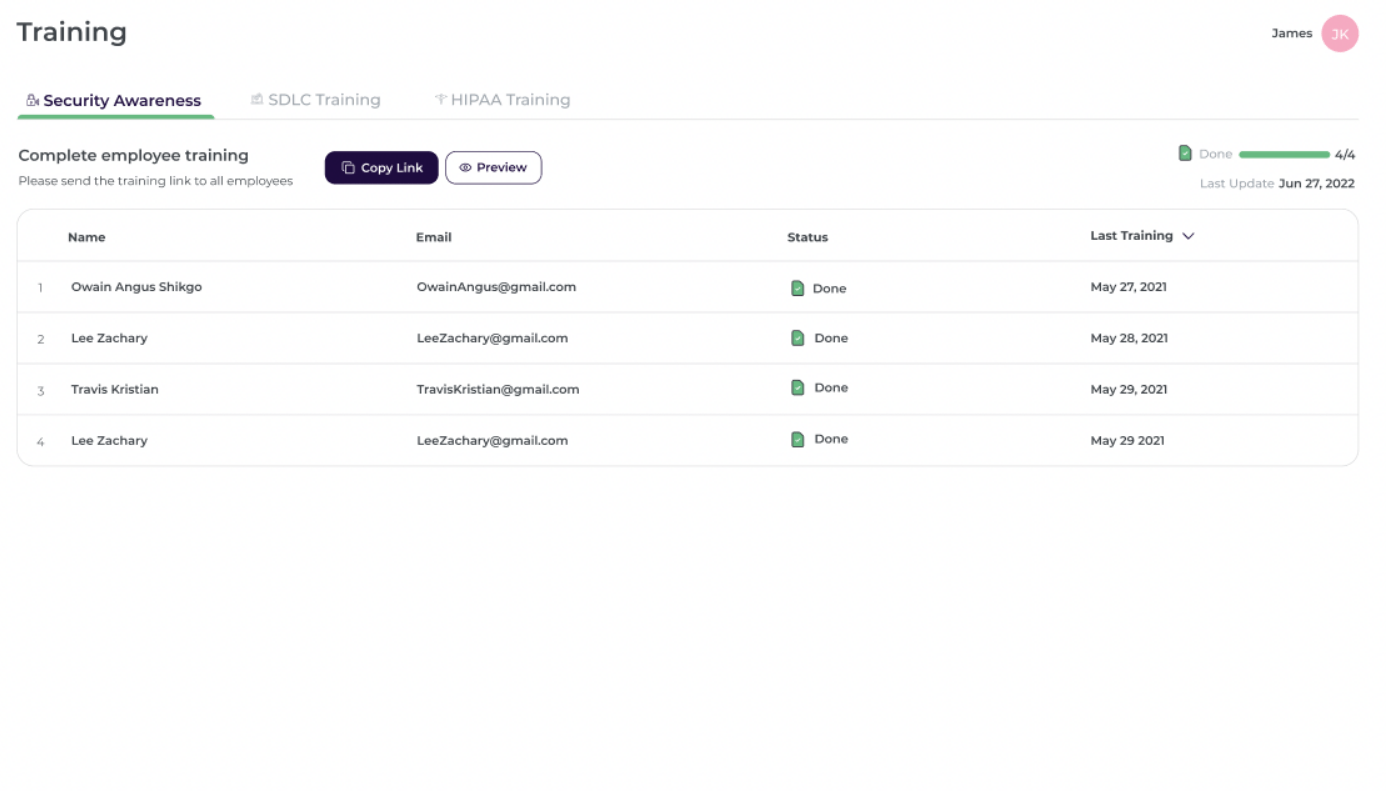
Scytale is another platform where AI plays a heavy role in the approach to risk management. The company’s AI tools can predict potential risks with great accuracy, allowing for a more proactive approach to addressing them.
Scytale also provides organizations with a risk register, allowing them to make tracking and managing potential threats a cornerstone of their security program. This approach is especially beneficial for fast-growing companies that may not have the resources to constantly monitor their tech stack.
Scytale best features
- Provides controls you can adapt for your organization, ensuring an exact fit for compliance needs
- Offers tools for security awareness training to improve readiness and minimize potential compliance issues
- Automates the evidence collection process, verifies it for key audit standards, and offers 24/7 monitoring of controls
- Provides auditor-approved policy templates for easier tuning and alignment of security policies and protocols
- Enables collaboration with security auditors to manage the entire process from within the software
- Provides automations that ensure there are no security gaps during the HR onboarding and offboarding processes
Scytale limitations
- Some users want more export options
- The navigation isn’t as intuitive as some customers would like
Scytale pricing
- Startup: Contact sales for pricing
- Growth: Contact sales for pricing
- Enterprise: Contact sales for pricing
Scytale ratings and reviews
- G2: 4.9/5 (100+ reviews)
- Capterra: 5/5 (5 reviews)
7. Apptega
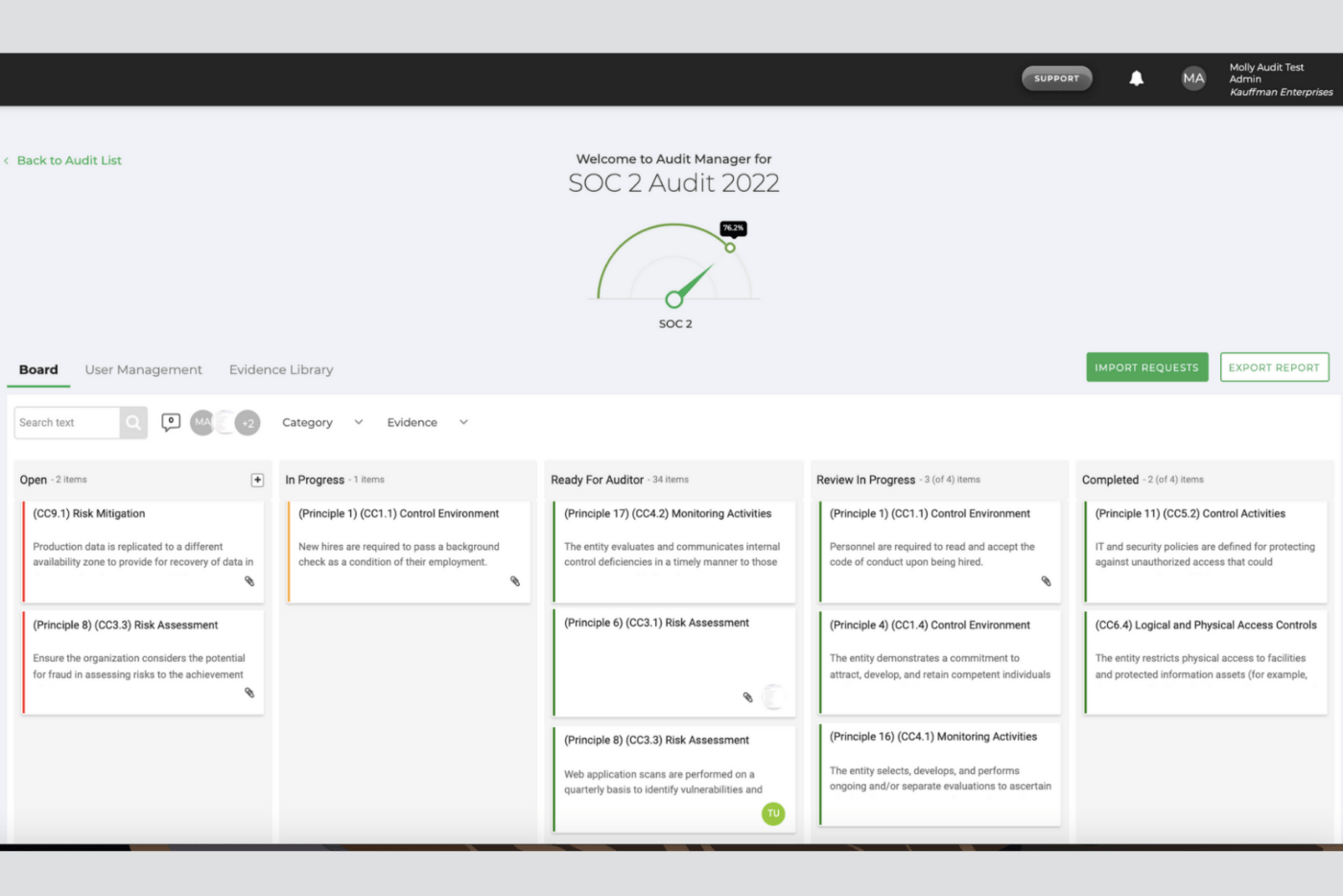
Apptega is a complete solution for building a security program. It offers a suite of compliance tools that make it easier for businesses to stay compliant with over 30 industry-standard frameworks, including SOC 2.
A big goal of the product is reducing the complexities and costs of managing cybersecurity. To that end, the company’s intuitive platform eliminates the need for spreadsheets or Word documents by offering a complete governance, risk, and compliance (GRC) solution. Much of the compliance tracking is automatic and continuous, quickly identifying security gaps and providing a blueprint for remediation.
Apptega best features
- Supports over 30 industry-standard frameworks, such as SOC 2, CMMC, PCI, and ISO27001
- Provides tools to quickly identify security gaps, and offers a roadmap to remediation
- Offers tools to get ahead of cybersecurity threats with out-of-the-box risk, vendor risk, and audit management features
- Provides an intuitive end-to-end GRC platform that eliminates the need for spreadsheets and Word docs
- Boosts efficiency by over 50% by cross walking all compliance frameworks in seconds
Apptega limitations
- Some users feel the UI isn’t as intuitive as it could be
- A few reviewers want a larger feature set
Apptega pricing
- Contact sales for pricing
Apptega ratings and reviews
- G2: 4.7/5 ( 54+ reviews)
- Capterra: 4.8/5 (21 reviews)
Protect Your Team with a Solid Compliance Process
In the above reviews, you’ve seen several great tools for SOC 2 compliance. You’ve also seen how many of them emphasize vendor management. When you use third-party providers, you need to make sure that they’re following appropriate security standards.
Whichever SOC 2 compliance software you choose, get the most out of it by integrating it into the product and task management tools in ClickUp.
The ClickUp security policy takes compliance with security frameworks seriously, so you can trust that the data you store on the program stays safe.
While the powerful productivity tools in ClickUp’s free project management software will keep your teams collaborating effectively and working together smoothly, our security experts will be working in the background to give you the peace of mind you need. Try ClickUp for free today!