
With the emergence of technology, cybersecurity risks are on the rise, posing a real threat to businesses of all sizes. As a result, organizations have started taking more preventative measures in their approach to cybersecurity to prevent cyber-attacks.
You need to implement a cybersecurity risk management framework to protect your organization. Such a framework will provide a structured approach to identifying, assessing, and managing risks in a systematic process.
Don’t wait until it’s too late. Take proactive steps today to safeguard your business.
This article will illustrate how to assess your cybersecurity posture, create appropriate goals and objectives, select a framework for your risk management process, implement mitigation strategies, and learn how to review the risk process you are following. 🔐
- What is Cybersecurity Risk Management?
- What is a Cybersecurity Risk Management Framework
- What is the Cybersecurity Risk Management Process defintion:
- The Importance of Implementing a Cybersecurity Risk Management Framework
- Examples of Cybersecurity Threats
- How to Implement a Cybersecurity Risk Management Framework (6 Steps with Templates)
- Upgrade Your Cybersecurity with a Risk Management Framework
What is Cybersecurity Risk Management?
Cybersecurity risk management is a process that helps organizations identify, assess, and prioritize potential risks to their digital assets. This includes data, hardware, software, networks, and other digital components.
It involves implementing policies and procedures to mitigate those risks and protect the organization from cyber-attacks. By proactively managing cybersecurity risks, businesses can prevent or minimize the impact of potential threats.
What is a Cybersecurity Risk Management Framework
A cybersecurity risk management framework is a systematic approach that can protect organizations against cyber threats.
It involves recognizing potential risks, evaluating the probability of impact and possible consequences of risks, coming up with security measures to minimize impact, and ongoing monitoring to adjust to emerging risks.
The procedure is thorough and empowers organizations as they take extra measures to secure their information and assets from cyber criminals.
What is the Cybersecurity Risk Management Process defintion:
The cybersecurity risk management process is a structured approach to identifying, assessing, and managing risks in an organization . This process helps organizations to make informed decisions about the level of risk that is acceptable for their business operations and create a plan to mitigate those risks.
The Importance of Implementing a Cybersecurity Risk Management Framework
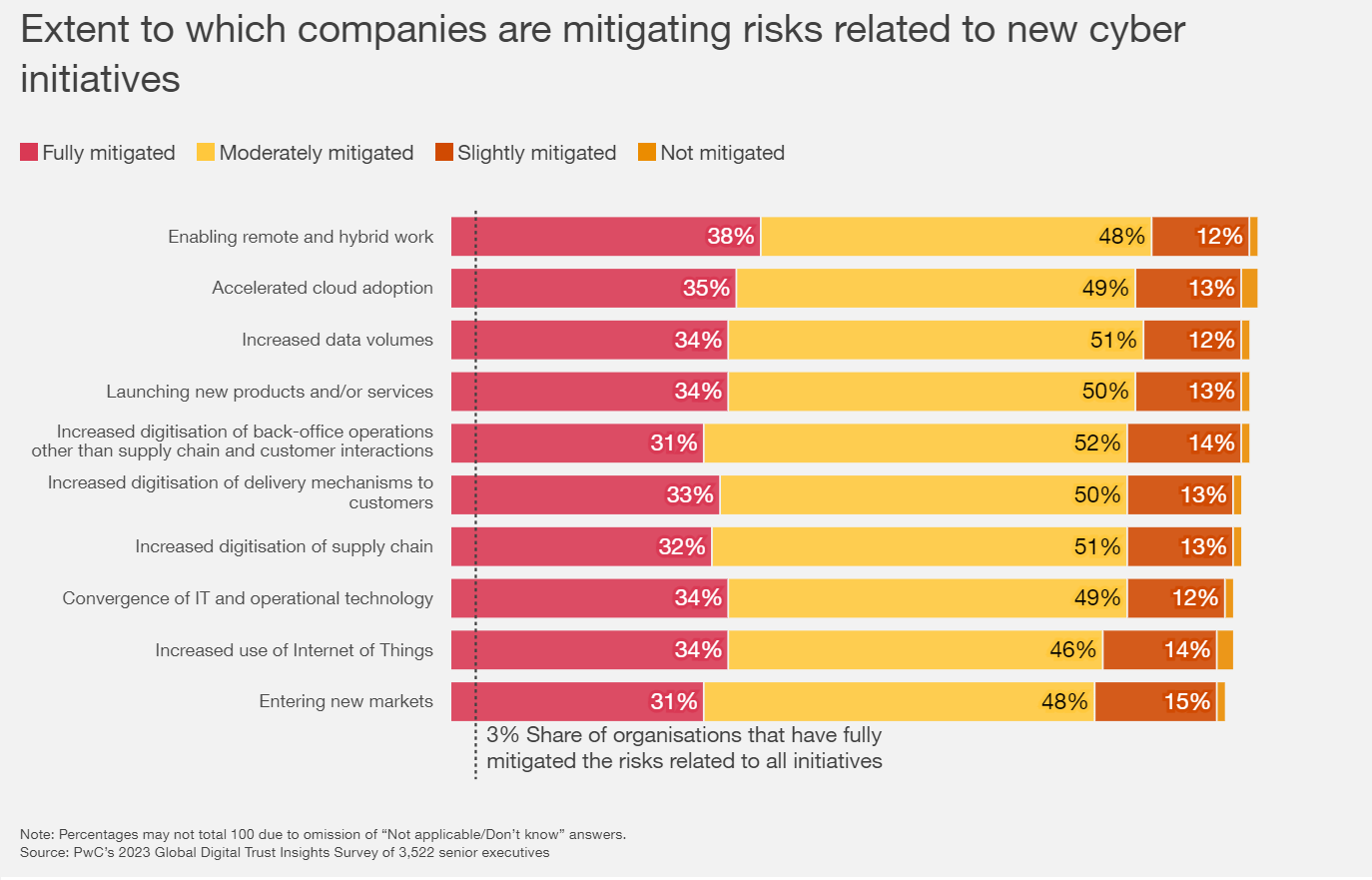
In the PwC Global Digital Trust Insights Survey, data shows some companies improved cybersecurity in the past year, but only a few actually completely mitigated all cyber risks. Cybersecurity is not only the responsibility of the CISO but also everyone’s business, including the CEO, who has the important role of building and keeping trust through concrete actions.
A structured approach and framework can manage potential risks and enable organizations to do the following:
- Evaluate their security posture
- Identify any existing gaps in your security measures
- Perform a risk assessment and evaluate internal and external threats
- Prioritize risks and establish a management process
- Implement necessary controls to mitigate potential cybersecurity risks
Preventive measures will assure your customers and stakeholders that you are serious about cybersecurity. As a result, they will feel more secure and will be more likely to continue using your products and services.
Examples of Cybersecurity Threats
Before diving into how to implement a cybersecurity risk management framework, let’s first understand the potential risks that organizations face:
- Phishing attacks: Using fraudulent emails or messages to obtain sensitive information from users.
- Malware attacks: A type of malicious software designed to gain access or cause damage to a computer system.
- Insider threats: Employees or former employees who have access to sensitive information and use it for malicious purposes.
- Social engineering attacks: Manipulating individuals into divulging sensitive information through tactics such as impersonation or blackmail.
- Distributed Denial of Service (DDoS) attacks: A coordinated effort to flood a system with traffic, resulting in service interruptions and data breaches.
How to Implement a Cybersecurity Risk Management Framework (6 Steps with Templates)
Step 1: Assess your current cybersecurity posture
The assessment of your cybersecurity posture is critical in Cybersecurity Risk Management. Below are the steps that can follow:
Evaluate current security measures
- Identify and review current cybersecurity risk management process: Outline all the security measures and include the process needed for managing security-related incidents and how to respond to threats
- Assess your network security: Perform a cybersecurity risk assessment by inspecting your firewalls, antivirus software, and other tools for detecting and preventing unauthorized access. They must be updated and have the latest security patches configured. If one is outdated, your network is more likely to become vulnerable
- Revisit your cyber risk management strategy: Check how your organization manages sensitive data and systems (access privileges, a policy on passwords, and multi-factor authentication), then conduct an internal and external vulnerability assessment to point out weaknesses
- Review your incident response plan: Test your incident response plan to ensure it’s effective, and check if you are able to detect, respond and recover from security incidents
- Check-in with employees: Provide your employees with training programs on security awareness and cybersecurity best practices, as well as other assessments such as:
- Knowledge retention tests
- Employee behavior and compliance observations to ensure they’re implementing what they’ve learned from training
- Simulated phishing tests to evaluate their capacity to identify and report phishing attempts.
- Evaluate their response to security incidents
- Evaluate your third-party vendors: If you have third-party vendors, they will have access to your systems. You’ll need to evaluate their cybersecurity measures and check their history as well
Identify gaps in security measures
According to IBM’s Threat Intelligence Index 2023, 27% of cyber attack victims were extortion-related, putting pressure on victims. You’ll need to identify gaps in your risk management strategy to determine any areas that are susceptible to cybersecurity threats.
After evaluating your current security measures, look for gaps that can put your organization at risk for cyber threats. Do you have outdated security solutions, unpatched software, and weak passwords? Do you have untrained employees?
- Compare security measures and conduct a cybersecurity assessment: Perform a comparison of your security measures against the best practices and standards currently used by your industry. Then conduct a risk assessment to identify potential threats and vulnerabilities
- Simulate a cyber-attack: Use penetration testing and a vulnerability scanner to identify weaknesses in your network immediately. Observe how employees react during an attack
- Check your incident reports: Review your security incident reports and analyze them for patterns or trends that may indicate areas of weakness
- Determine areas for improvement: Once the weak points in your security measures are identified, check what needs improvement. Prioritize what is more important. Then come up with a plan to fix it
- Assess internal and external threats and vulnerabilities: Perform security audits and risk assessments to determine where your vulnerabilities lie
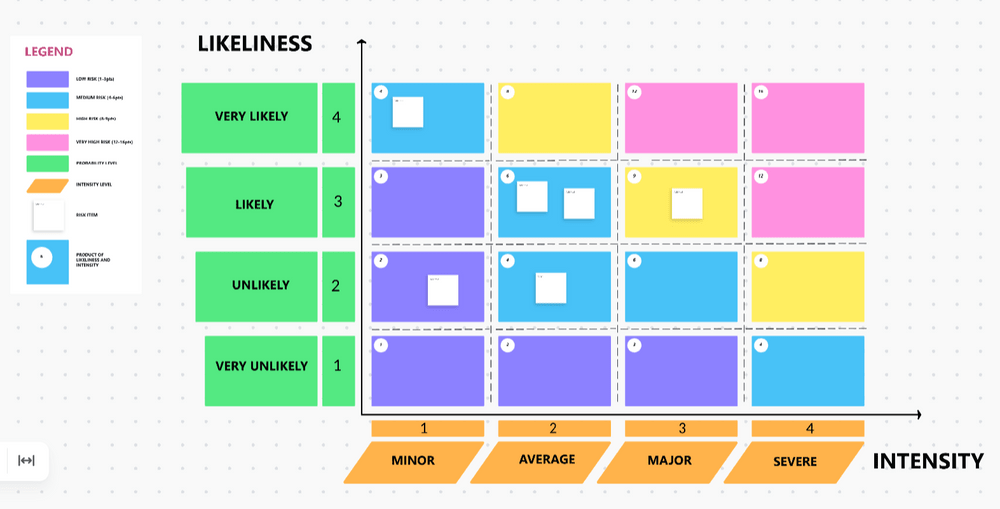
PRO TIP
Use the Risk Assessment Whiteboard Template by ClickUp to help document potential threats on a digital whiteboard and easily collaborate and share it with your team. This template offers a systematic process for identifying, assessing, and controlling hazards and risks to improve the chance of successful project completion.
Step 2: Define your goals and objectives
Clearly defined goals and objectives will allow you to focus on your key priorities and properly allocate your resources.
Determine what you want to achieve
- Check the integrity and availability requirements: What areas in your organization need protection? What does it need to accomplish in terms of cybersecurity risk management? Be specific with your goals and objectives. Check on the integrity and availability requirements for your information assets. Ensure they are compliant and meet all regulatory requirements
- Develop a cybersecurity risk management program: Examine the possible effects of cyber threats and attacks on your organization, and create goals to target lowering the impact of such incidents Develop your own strategies for prevention, detection and response
Set your goals and objectives
- A structured approach is required to establish attainable and clear goals and objectives that align with your cybersecurity risk management strategy. Adhering to the SMART goals framework can help ensure that goals are well-defined and achievable
- Specific: When defining the objectives for cybersecurity risk management, the organization will be more specific and concise
- Example: Decrease the number of successful phishing attacks by 80% within the next three months
- Measurable: Having a measurable target will let you determine and track your progress
- Example: Reduce the number of successful phishing attacks by 80%” and measure it by the number of reported incidents
- Attainable: Verify if the objective is something that will be attained by your organization using the existing resources and capabilities.
- Example: Enforce two-factor authentication for all staff within the next three months
- Relevant: Ensure your objective aligns with the organization’s mission and goals.
- Example: Enhance the security posture of your organization and mitigate the risk of data breaches by deploying a vulnerability management program within the next 12 months”
- Time-bound: Set a specific timeline for accomplishing the objective.
- Example: Set a goal in establishing a disaster recovery plan within the next six months that enables the restoration of critical systems within 4 hours of any disruption
- Specific: When defining the objectives for cybersecurity risk management, the organization will be more specific and concise
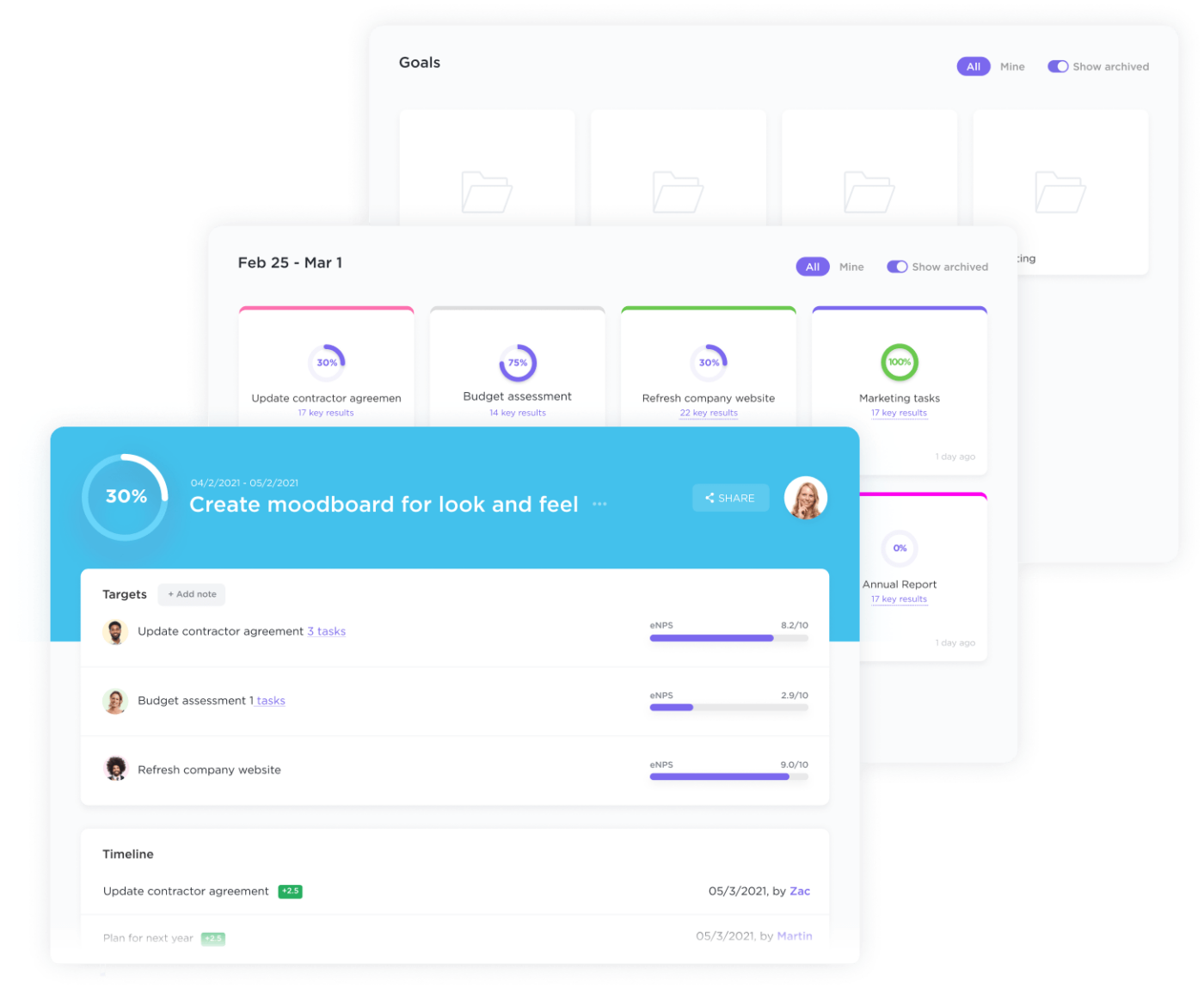
PRO TIP
Keep your goals organized and track your progress with Goals in ClickUp. Easily create trackable goals, and stay on track to hit your goals with clear timelines, measurable targets, and automatic progress tracking. You can also take advantage of goal-setting templates to help you outline your goals faster.
Step 3: Select a risk management framework
Choosing your cybersecurity risk management framework is essential for creating a cybersecurity plan. You can select from the four of the most widely recognized framework: NIST, ISO, CIS, and FAIR. Each framework has its advantages and disadvantages; study and compare these risk management frameworks to find the one that fits your requirements.
National Institute of Standards and Technology (NIST) Cybersecurity Framework
The NIST Cybersecurity Framework is a voluntary tool provided by the U.S. Department of Commerce to assist businesses of all sizes in managing cybersecurity. Businesses can utilize the framework to address five key areas: identification, protection, detection, response, and recovery.
International Organization for Standardization (ISO) 27001
ISO 27001 is a globally recognized framework for information security management that systematically safeguards and controls confidential data using a risk management approach. This framework includes a set of requirements and guidelines for implementing an information security management system (ISMS) to help organizations keep their information assets secure. The topics covered include risk assessment and management, access control, cryptography, business continuity and compliance.
Organizations often need ISO 27001 certification to show their dedication to information security to customers and partners.
Center for Internet Security (CIS) Controls
The CIS Controls are guidelines that offer a prioritized approach to managing cybersecurity risks. It includes 20 critical security protocols you can adopt to improve your cybersecurity posture. These controls are designed based on actual cyber threats and offer a comprehensive framework to manage and mitigate cyber risks.
Factor Analysis of Information Risk (FAIR)
FAIR is a quantitative risk management framework that helps organizations assess and analyze information security risks in financial terms. It provides a systematic approach to risk analysis and helps organizations understand the potential impact and likelihood of different threats. FAIR also helps organizations prioritize their risk management efforts and allocate resources effectively.
You will be more confident in selecting the right framework to customize for your organization when you perform much-needed research and analysis, one that is capable of managing your cybersecurity risks efficiently.
Step 4: Establish a risk management process
Have your own risk management process to help identify possible risks and predict the likelihood of them taking place. It will also give you a forecast of how much damage it would cause.
Devise your implementing strategies to reduce and control risks, and continuously monitor for effectiveness. Through this, organizations can proactively minimize cyber-attacks.
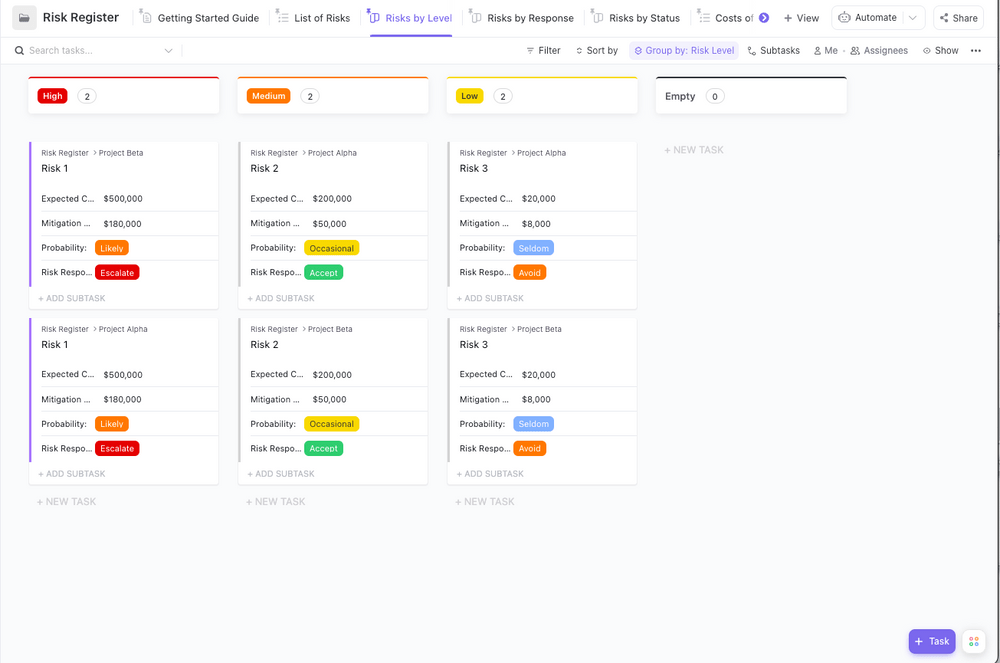
PRO TIP
Manage your projects and avoid risks using this Risk Register Template by ClickUp. This template comes with pre-built ClickUp views, Custom Fields, and custom statuses to help easily track any potential risks and employ effective preventive measures.
Step 5: Implement mitigation strategies
Start managing the cybersecurity risk in your organization, and begin by implementing mitigation strategies. You can start doing this once you have identified and assessed all potential risks.
Implement new security measures
As you implement new security measures, you will include software installation, network segmentation, access controls, intrusion detection systems, and other controls to help mitigate cyber-attacks.
Update existing security measures
Keep yourself up-to-date with our ever-changing digital landscape. Periodically check your existing security measures and set aside some budget for them. Allocate a budget for implementing software updates and patches and upgrading hardware to address vulnerabilities, improve access control, and strengthen passwords and encryption protocols.
Develop an incident response plan
Lay out your procedures for detecting, assessing the severity, and reporting incidents. Every organization needs to have specific people assigned to the response plan. Each member should have a specific role assigned to communicate with your customers and stakeholders in the event of an incident taking place.
PRO TIP
Data is typically the most valuable asset for most organizations. It’s key to generating revenue, making data protection crucial to their success as a whole. This is why creating a viable cybersecurity implementation plan is important. Use the Cybersecurity Action Plan Template by ClickUp to give your team an organized and detailed outline for your action plans.

Step 6: Monitor and review
Monitoring the effectiveness of cybersecurity measures is crucial to ensure they offer sufficient protection against emerging threats, and reviewing the cybersecurity strategy and incident response plan can help identify what areas require updates.
Regularly assess the risk management process
Activities such as vulnerability assessments, penetration testing, security logs monitoring, incident response report analysis, and training for employee advocacy on security awareness are ways to achieve this.
Evaluate mitigation strategies
Evaluating mitigation strategies will be an ongoing process, as it is inevitable for new threats and vulnerabilities to take place. Hence, organizations must remain proactive and always prepared to respond to potential incidents.
Update framework as needed
Once an evaluation is conducted and any security gaps are identified, updating the security framework is critical. The organization may need to modify or replace the current framework with a more suitable one. Any modifications made to the infrastructure, applications, or business processes should be assessed for potential cybersecurity risks and integrated into the existing framework. When the cybersecurity framework is consistently updated and improved, organizations can guarantee they are adequately prepared against cyber threats.
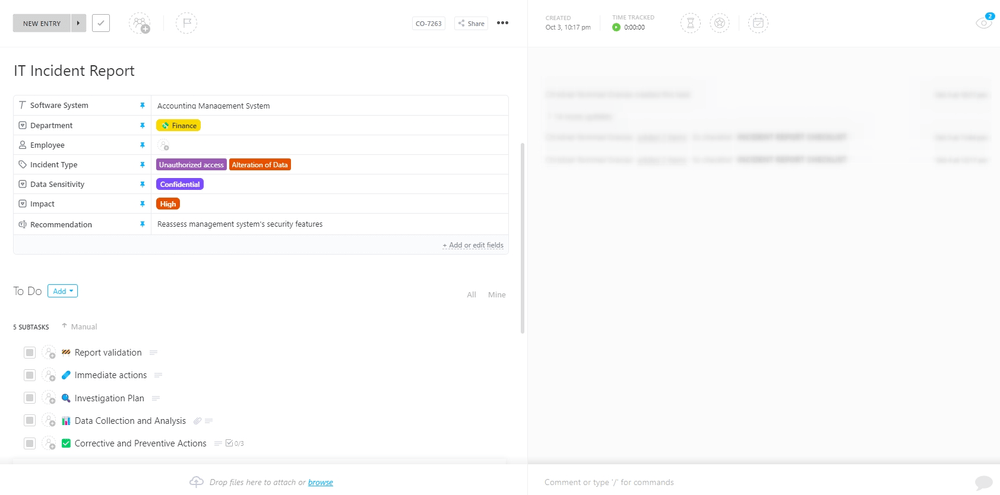
PRO TIP
Stay on top of your risk management process and plan, manage, and track your cybersecurity process in one place with ClickUp, an all-in-one and secure project management tool. You’ll also get access to a library of templates, including the IT Incident Report Template by ClickUp. Use this template to help you record incident reports and save reliable records of all past incidents associated with their environment, which can be used to assess current security posture and plan for future threats accordingly.
Upgrade Your Cybersecurity with a Risk Management Framework
By implementing a risk management framework, all sensitive data and information of your business remain secure from cyber threats. You can also easily identify potential security risks, prioritize your actions based on their impact, and, most importantly, take measures to mitigate them.
Tools like ClickUp, a very powerful and secure project management tool, can help manage your organization’s protocols and projects more efficiently. ClickUp offers a wide range of security features like data encryption, two-factor authentication, and role-based permissions. It secures your work and makes your team members accountable. And to prove that customer security and privacy are ClickUp’s top priority, ClickUp has successfully passed the highest standards of security and achieved ISO 27001, ISO 27017, and ISO 27018 certifications.
In addition to ClickUp, partnering with UpGuard, a cybersecurity company will provide you with an extra layer of security. UpGuard’s platform provides a range of cybersecurity solutions, like vendor risk management, data leak detection, and security ratings. It lets you manage your security risks and ensure you are compliant with industry regulations.
Overall, if you want to protect your business from online attacks, tools like ClickUp and UpGuard will be useful. By taking measures to protect your organization, you can ensure its longevity and growth.

Marites Hervas is an experienced professional in the SEO industry with over a decade of experience. She began her career as a content writer before transitioning to a full-time administrative assistant. In recent years, she has focused on developing her skills in outreach marketing and staying current with the latest SEO trends. In 2021, she joined UpGuard as a Growth Marketing Specialist, bringing her extensive knowledge and expertise to the team.