10 Ways to Reduce Cyber Security Risks in Project Management

Sorry, there were no results found for “”
Sorry, there were no results found for “”
Sorry, there were no results found for “”
May 04, 2023
12min read
Project management comes with many responsibilities, deadlines, late-night shifts, and a lot of coffee.
Luckily, you can stay on top of your game with a bit of help from your buddy: project management software.
With that in mind, communication has never been simpler, easier, or quicker, leading to a more productive and successful team.
Remote project management helps the project managers connect hybrid teams and ensure everyone works together to accomplish the project’s goals. On that note, it is no different from managing any other project, except that the project is carried out remotely.
And managing and operating a remote team brings up a delicate issue: increased cybercrime risk.
With that being said, let’s take a look at the five biggest cybersecurity threats project managers face today and ten ways to tackle them!
Cybersecurity can make or break a business.
Companies function on data, and data is the company’s most valuable asset. However, in today’s digital world, data has become more vulnerable to cyberattacks, and with the hybrid and remote work arrangements, that vulnerability is even greater.
The rise in data breaches and hacks can be attributed to a lack of data protection, the consequences of a global pandemic, and an increase in the sophistication of exploits. Businesses are now more aware than ever of the problems that data breaches can create.
One of the data breaches that paved the way for the new EU legislation was the Wonga Loans case. This payday loan company experienced a significant data breach in 2017 that exposed the bank information of 250,000 customers.
Here are the most significant cyber threats you should be aware of and tips on how to prevent them.
Imagine this scenario: you and your colleague are talking via a secure platform, but someone is eavesdropping on your conversation and sending fake messages to your colleague from you. Yikes!
The idea behind this is that the hackers gain access to personal and sensitive data, and manipulate the messages.
It could happen if you use an unsecured public Wi-Fi network. When the hacker is inside the insecure location, they will get access and send malware to find sensitive data. They can also pretend to be a customer or a business partner, or anyone, really.
Recently, a threat actor got 500 certificates for websites such as Google, Skype, and other prominent sites thanks to a hack at the Dutch registrar site DigiNotar. By using these certificates, the attacker impersonated trustworthy websites in a MITM attack and stole users’ data by tricking them into providing their credentials on mirror websites. The breach ultimately led to an impact on about 300,000 Iranian Gmail accounts and to DigiNotar declaring bankruptcy.
Let’s say you’re preparing for your holiday and want to buy a Hawaiian dress. You open your web browser and type “Hawaiian dresses” in the search bar. If the search bar is infected by injecting malicious code, it will still give you a list of Hawaiian dresses, but it will use your question to find your personal info. ?
A hacker uses a piece of SQL code to alter a database and get access to potentially important information in a cyberattack known as SQL injection. Given that it may be used for any web application or site that makes use of a SQL-based database, it is one of the most common and dangerous types of attack.
Some victims of this type of cyberattack include Sony Pictures, Target, LinkedIn, and Epic Games. The Cisco case from 2018 is one of the most widely-known attacks. They found an SQL injection vulnerability in Cisco Prime License Manager.
Attackers were able to get shell access to the systems where the license management was deployed. But fear not. Since then, Cisco has managed to patch the issue.
Although this bug is old enough to drink now, we still can’t squash it for good. It’s considered one of the oldest cyber threats and yet, it still causes just as many problems.
It’s all fun and games until you download malware and help the hackers get all your personal data. Malware sums up all files or programs that cause harm, and it covers worms, trojans, viruses, and ransomware.
By 2021, 68.5% of companies experienced malware attacks. The reports show the increase was built on the rise of the COVID-19 outbreak.
Additionally, the criminals moved away from automated ransomware campaigns that focused on the scale to more targeted extortions against well-established businesses. Due to this change, ransomware became more profitable, eventually catching the attention of criminal gangs.
The increased use of this new extortion technique caused the ransomware outbreak to worsen.
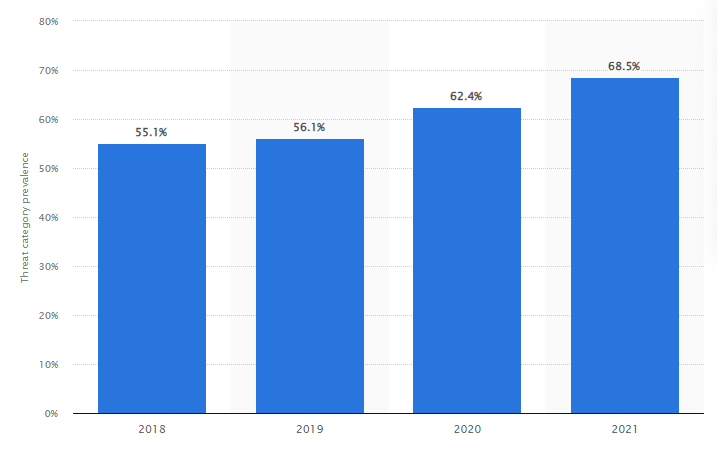
One of the most famous attacks was the WannaCry ransomware attack managed to infect more than 230,000 computers in a day and resulted in a loss of $4 billion.
Phishing is a form of social engineering in which an attacker sends a false message intended to trick the person into giving up personal information or installing harmful software on the victim’s infrastructure.
Ubiquiti Networks, unfortunately, suffered a phishing assault in 2015 that cost the business $46.7 million. The attacker authorized the company’s chief accounting officer to make a series of transfers to finalize a secret acquisition.
The hacker posed as the company’s CEO and attorney. The company made 14 wire payments over a period of 17 days to accounts in Poland, Hungary, China, and Russia.
Ubiquiti was first aware of the issue after it received a warning from the FBI that its Hong Kong bank account may have been the target of fraud. This made it possible for the business to halt all upcoming transfers and make every effort to recoup as much of the $46.7 million, roughly 10% of the company’s cash, that had been taken.
This type of cyber attack can cause a network shut down and will make it inaccessible to users. The hackers could have political or social goals, for example, launching a campaign against a company whose activities they don’t like.
Sometimes, hackers use DDoS attacks just for fun and to brag about the newest techniques they’ve developed to bring down a system.
In February 2020, Amazon Web Services was the target of a massive DDoS attack. This was the most severe DDoS attack in recent history and it used a method called Connectionless Lightweight Directory Access Protocol (CLDAP) reflection to target an unnamed AWS customer.
The amount of data delivered to the victim’s IP address is increased by 56 to 70 times using this technique, which is dependent on vulnerable third-party CLDAP servers. The attack peaked at an astonishing 2.3 gigabytes per second over the course of three days.
Hackers are becoming more and more creative and are making us sweat.
To help you combat these threats, here are ten ways to help defend and protect your business against potential cyber threats.
Project management tools are must-haves nowadays, especially for tracking the progress of your project and improving team communication. However, not every work tool available today is secure.
When we say secure, we mean a platform with the proper authorization measures to minimize information leaks.
ClickUp is one of the most secure collaboration tools available today. It provides a secure environment, while also being mindful of application performance and the overall user experience.
In fact, it has continuously achieved SOC 2 compliance, ISO 27001, ISO 27017, and ISO 27018 certifications. These ISO certifications prove ClickUp’s commitment to keeping their customer data protected and their preparedness to support customers of all sizes across the world.
Take a look at its security features:
You also need a cloud service where you will keep your vital data in a highly secure centralized location that your cybersecurity team can monitor.
Internxt is a decentralized cloud storage platform that integrates peer-to-peer filesharing, blockchain, and end-to-end encryption. Your files are stored in fragmented parts across server locations in different countries, making them even more private and secure.

These are its features:
When this type of cloud service meets a management app such as ClickUp the security of your project, but also the productivity and the team collaboration, are all in check.
Combined, Internxt, and ClickUp are your Area 51! ?
If you want to ensure that the project will succeed, you must make an effort to establish information security needs from the get-go, and then make sure that the appropriate processes are in place.
If security requirements aren’t addressed early enough in the project cycle, they can have a significant influence on milestones and project scope when they do appear. And trust us, they will!
Ensure that information security is treated as a continuous concern and managed as such throughout the project life cycle.
Improve your project processes by adding security roles to the project and assigning responsibility.
A knowledgeable and experienced security team is a great asset. They can advise you on how security requirements affect project planning and resources, as well as what type of monitoring you need.
Security Manager and Security Analyst are currently two of the most sought-after cybersecurity positions.
Security Analysts are in charge of stopping breaches and repairing any harm caused by earlier attacks. Security Managers, on the other hand, are responsible for developing security plans and implementing policies to protect sensitive information.
Use reliable virtual private networks (VPNs) to protect your computers and smartphones. They protect your identity from government agencies and hackers and hide your IP addresses and data. The VPN prevents hackers from spying on your online activities.
Antivirus software is also essential. This software is a set of programs that are designed to detect and prevent software viruses such as adware, trojans, worms, etc.
Data thieves will find you far less interesting with both of these safeguards.
Now, I’m not saying that this will protect you from any harm or danger, but it sure does help.
The VPN will give you some untraceable superpowers. ?
Third-party vendor risks fall into three categories: Operational, transactional, and compliance/regulatory.
Here are a few ways you can protect the company from third-party dangers and risks:
Sticking to known and trusted sources is one way to deal with cyber threats. This means connecting with reliable service and product providers and using only trustworthy payment methods and websites.
Remember that if anything seems too good to be true, it most likely is, and if something doesn’t feel quite right, it most likely isn’t. ?
There are a few ways in which you can check if a source is reliable or not.
There are also data security threats that migrate from computer to computer and not just online cyber-attacks. They can track a laptop and break in without you knowing about it. Those worms and Trojan horses have their fingerprints all over this.
Installing a firewall is crucial for data security. A firewall protects your network by controlling internet traffic. It protects your computer or network from hackers or needless network traffic and creates a perimeter of security around your computer or network to block potentially hazardous incoming data.
Additionally, this system can screen malicious outbound traffic. By doing this, firewalls lessen the possibility that the devices protected by the firewall will join a botnet – a large collection of internet-connected devices controlled by attackers.
There are five types of firewalls: packet filtering firewall, circuit-level gateway, application-level gateway, stateful inspection firewall, and next-generation firewall—the best one for cybersecurity is the application-level firewall. It can restrict access to dangerous websites and stop the leakage of sensitive data.
You should consider implementing cybersecurity testing and thoroughly checking every connection between IT systems and the internet. Without testing for weak points, anyone can access a database or network infrastructure and wreak havoc with enough time.
You should also test your employees’ behavior and the general procedures throughout the project management phase. Examine how permissions are granted to business assets and come up with rules to protect confidential data as safely as possible.
A compromised password allows hackers or cybercriminals to get into a system and steal data.
A password becomes more difficult to guess with at least ten characters; blend those with numbers, symbols, or upper and lower-case characters, and you got yourself a password.
Remember to always check your password’s difficulty before using them!
Also, enable multi-factor authentication. While multifactor authentication should be normal at all times, it’s especially important when your third-party partner works remotely and accesses the network using unknown devices.
To reduce credential theft, credentials should be unique to each individual user. Credentials should not be passed down to a substitute for a former associate. Instead of SMS or email, consider using a second or third factor that your company can manage, such as Radio Frequency Identification (RFID) cards or biometrics. When your business relationship ends, always close the account.
Updating software regularly will help protect against security vulnerabilities, improve performance, and provide access to the latest features and bug fixes.
Regularly scanning for potential threats is also essential in order to identify any malicious activity or suspicious behavior on your system. It’s important to keep your software up-to-date in order to reduce the risk of falling victim to any malicious attack.
Related: Risk management templates
To help combat cyber threats and online vulnerabilities, it’s crucial to choose a project management tool that is proven to be safe and secure. If you aren’t confident with your current work tool, then it’s time for a change. Incorporate strong cybersecurity and secure digital storage into every aspect of your next project—ClickUp, and Internxt can help with that ? ?
Guest Writer:

Mia Naumoska is a Chief Marketing Officer at Internxt, a zero-knowledge cloud storage service based on best-in-class privacy and security.
© 2026 ClickUp