7 Best SOC 2 Compliance Software Tools in 2026

Sorry, there were no results found for “”
Sorry, there were no results found for “”
Sorry, there were no results found for “”
Compliance with security frameworks, such as System and Organization Controls 2 (SOC 2), acts as a protective shield for sensitive data. Cybersecurity threats get more sophisticated by the day, and proper security measures are the best way to guard against them.
This is not only an ethical obligation to customers but a critical business obligation. A data breach can lead to loss of confidential information and loss of trust among customers. In some areas, there are even legal requirements to secure data according to a specific framework’s standards.
Today’s tech stacks deal with large amounts of data from many disparate sources. Keeping track of everything, and doing so in a way that keeps you compliant, can be a Herculean task. Thankfully, there are software products on the market that can automate many of these tasks and make keeping on top of data compliance a much more achievable goal.
In this article, we’ll talk about the best products for securing your data to the SOC 2 standard. Some of these tools also support other data security standards you may need to follow as well!
SOC 2 is a framework that defines criteria for managing customer data according to five trust service principles. Those principles are security, availability, processing integrity, confidentiality, and privacy.
SOC 2 compliance is necessary for any businesses that store customer data in the cloud. It ensures the security and integrity of information. Achieving and maintaining SOC 2 compliance demonstrates to customers and stakeholders that an organization has robust security controls in place to protect their data.
As you look for SOC 2 compliance tools for your company, your priority will be simplifying the time-consuming audit process in a way that fits well with your existing workflow and culture. But there are other important features to look for, such as:
Choosing the right SOC 2 compliance software can give your business a head-start for developing a successful compliance program that follows evolving standards. To help you find the right security and compliance software for your company, we’ve assembled this list of the top options on the market.
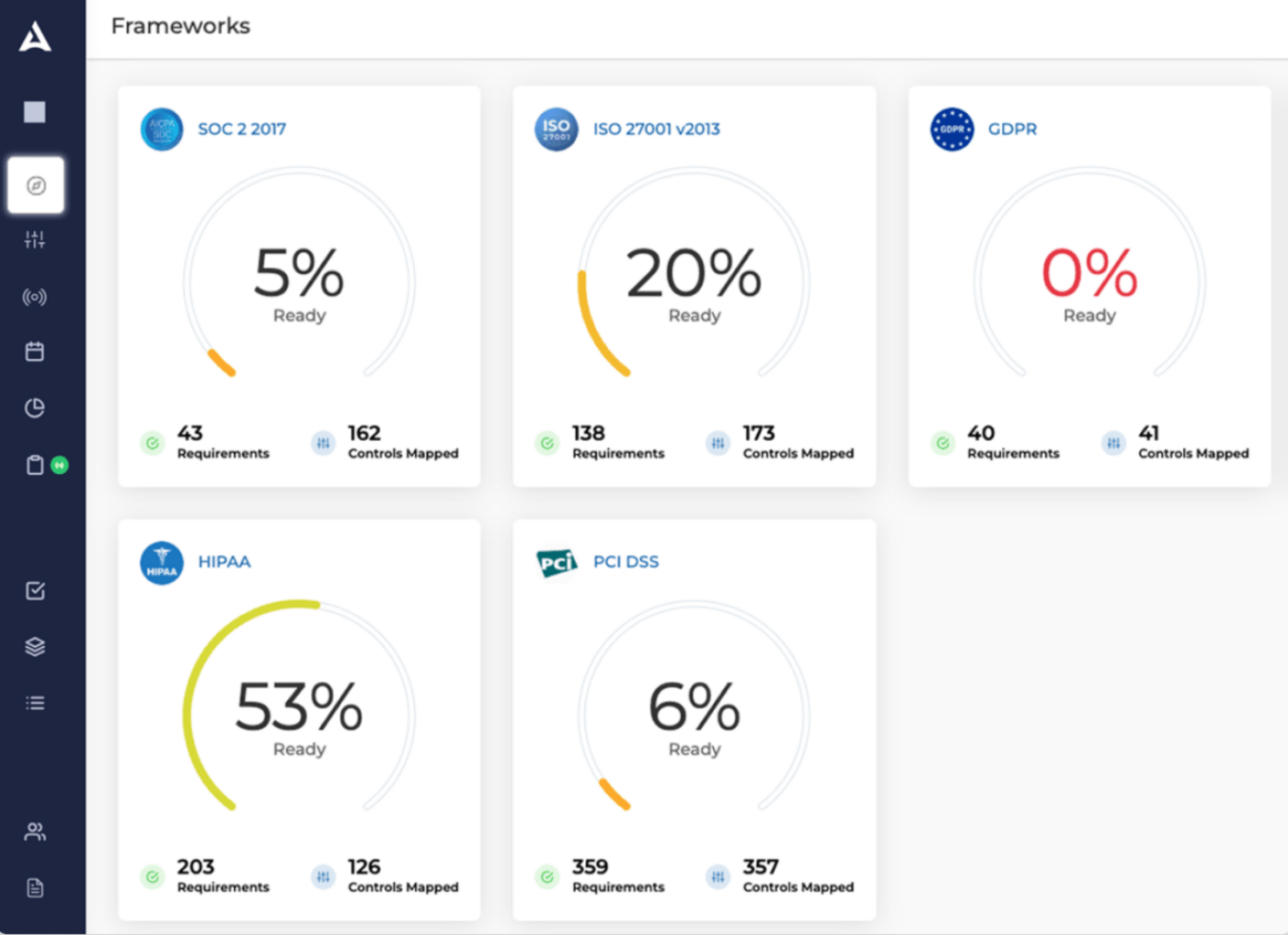
Drata automates compliance for businesses, making it easier for them to achieve and maintain SOC 2 compliance. This platform puts a strong focus on its ability to automatically collect evidence from a company’s tech stack.
This is a time-consuming process for many organizations. Automating it speeds up the compliance process while also ensuring that the collected evidence is accurate and up to date. For fast-growing companies, this is a must-have, as it allows them to demonstrate to their customers how seriously they take security and compliance without requiring a significant amount of manual effort.
Check out these Drata alternatives!
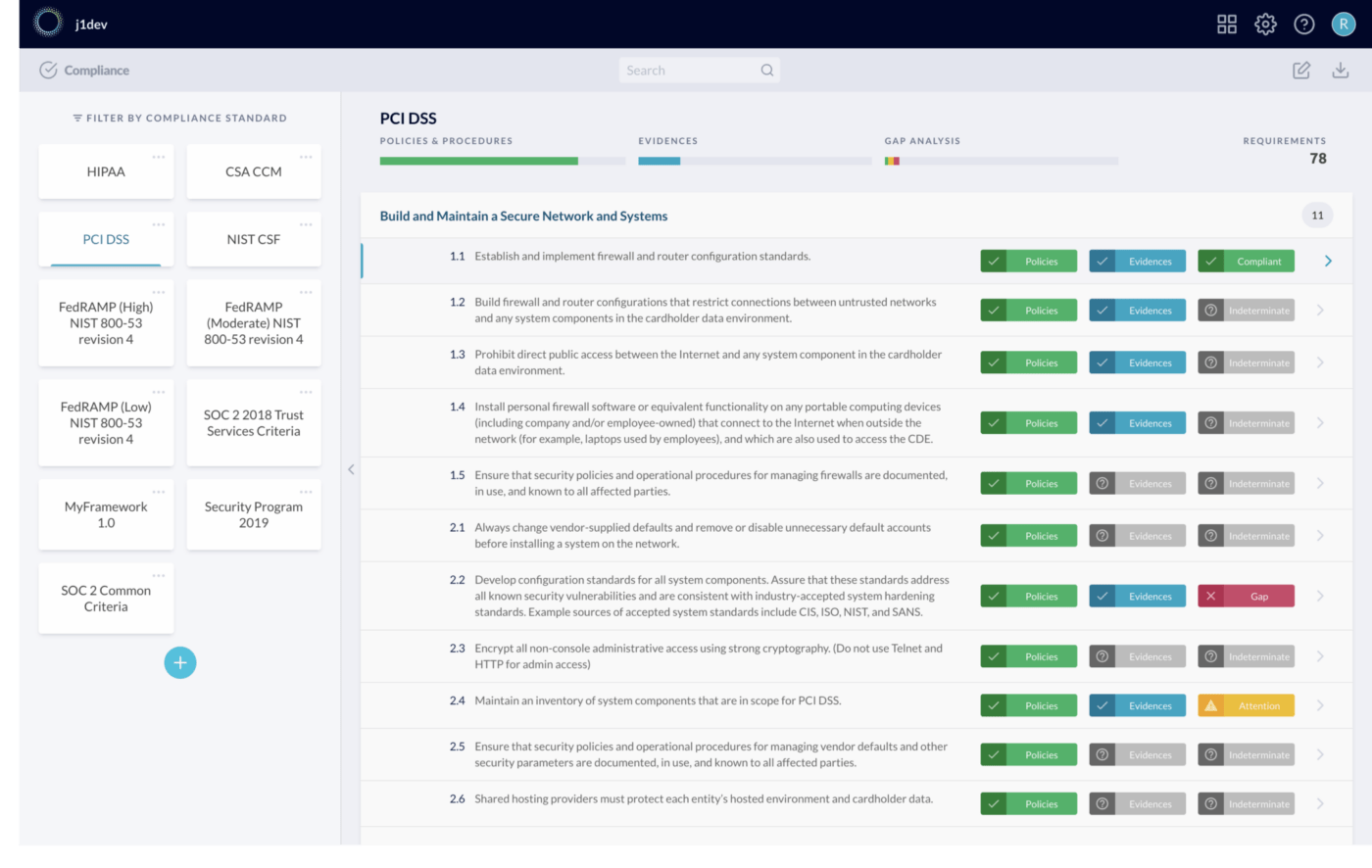
This software also takes a holistic approach to building a security program. By integrating with the entire tech stack of a business, JupiterOne offers better risk management.
These integrations allow the software to automatically collect evidence for compliance audits. This takes the hassle out of compliance management and provides peace of mind. The software also features vendor management tools to help mitigate the risks associated with bringing in third-party vendors.
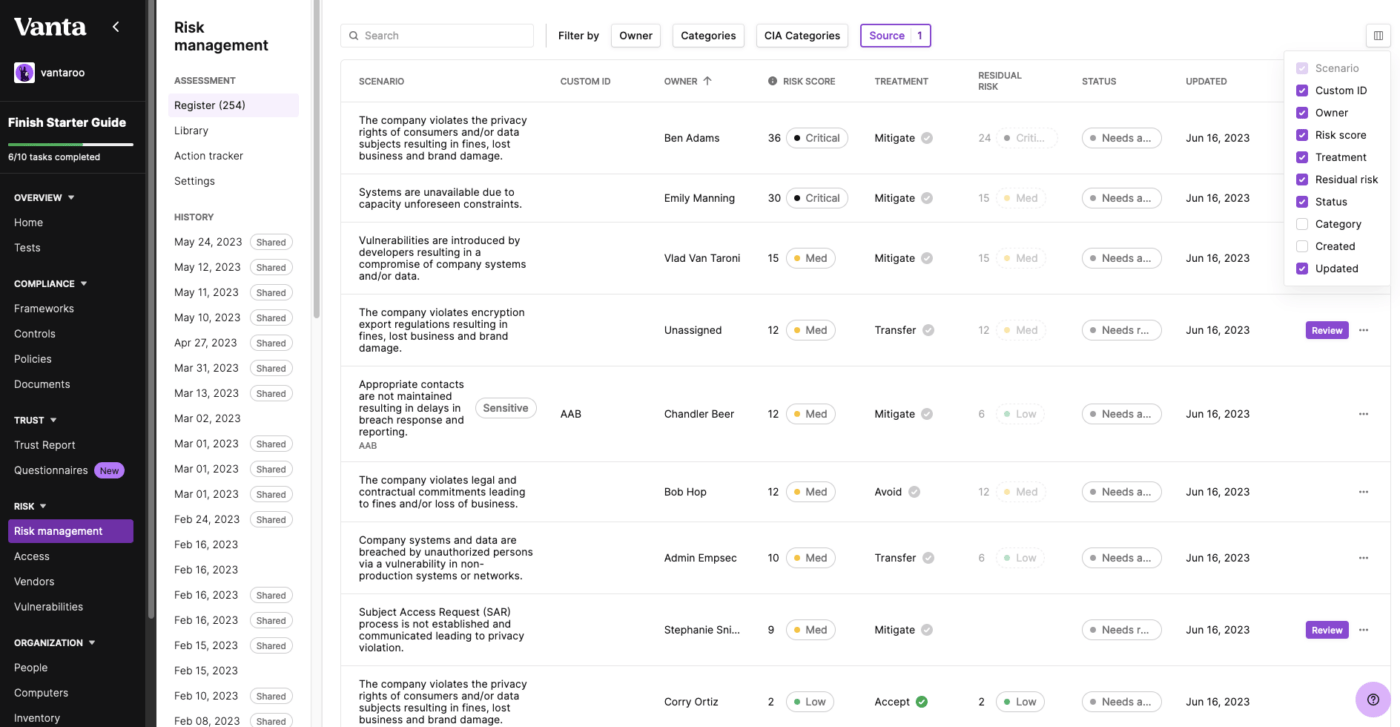
This product simplifies the compliance process for companies with automated compliance solutions. Vanta helps businesses prepare for compliance audits for SOC 2 compliance or one of the other popular security frameworks.
The software produces readiness assessments that allow companies to understand their current position and proactive ways to improve. Staying on top of the risk assessments allows businesses to better prepare for any potential audits.
Check out these Vanta alternatives!
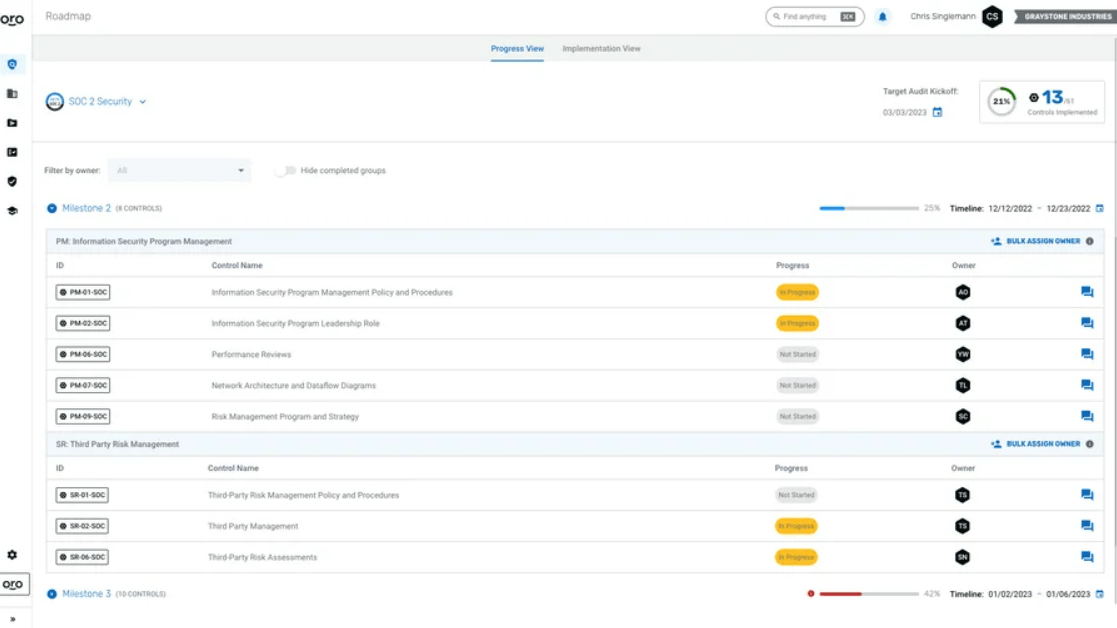
This SOC2 compliance software places a strong emphasis on access management. Thoropass ensures that only authorized individuals have access to sensitive systems and data. For example, you can monitor and revoke access for former employees, ensuring that business data remains secure after employees leave.
Of course, Thoropass provides a host of other features as well (enough to handle all of your compliance needs). The extensive set of integrations ensures a complete picture of your security posture.
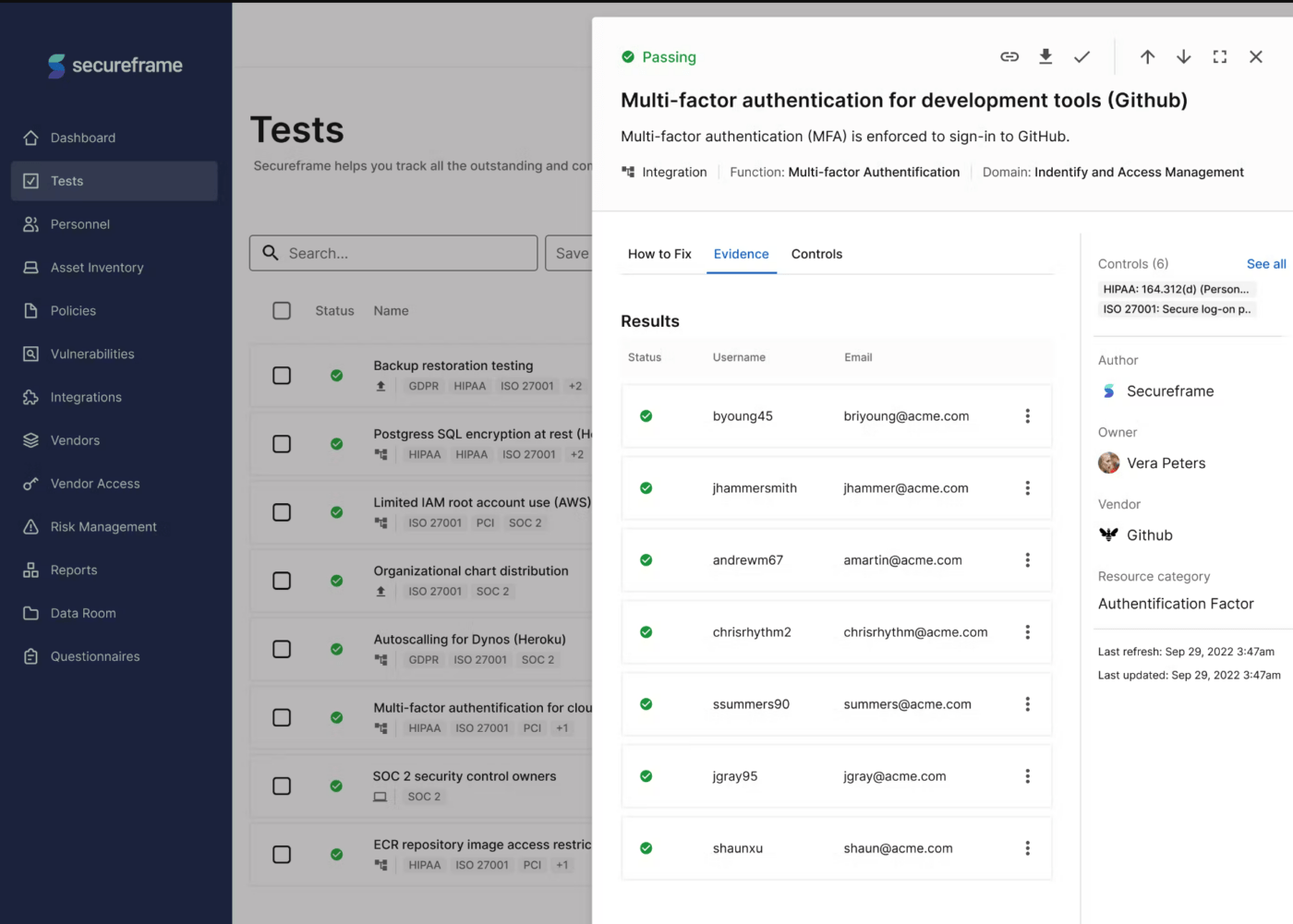
Secureframe aims to help businesses achieve compliance with some of the world’s most rigorous security standards. Its strength lies in its automated compliance capabilities, which reduce the time-consuming task of gathering evidence.
Powerful AI algorithms that aid users through all aspects of security augment this software’s capabilities. Additionally, tools for onboarding and offboarding keep employees in the know. Policy acceptance tracking ensures everyone is adhering to an organization’s security policies.
Scytale is another platform where AI plays a heavy role in the approach to risk management. The company’s AI tools can predict potential risks with great accuracy, allowing for a more proactive approach to addressing them.
Scytale also provides organizations with a risk register, allowing them to make tracking and managing potential threats a cornerstone of their security program. This approach is especially beneficial for fast-growing companies that may not have the resources to constantly monitor their tech stack.
Apptega is a complete solution for building a security program. It offers a suite of compliance tools that make it easier for businesses to stay compliant with over 30 industry-standard frameworks, including SOC 2.
A big goal of the product is reducing the complexities and costs of managing cybersecurity. To that end, the company’s intuitive platform eliminates the need for spreadsheets or Word documents by offering a complete governance, risk, and compliance (GRC) solution. Much of the compliance tracking is automatic and continuous, quickly identifying security gaps and providing a blueprint for remediation.
In the above reviews, you’ve seen several great tools for SOC 2 compliance. You’ve also seen how many of them emphasize vendor management. When you use third-party providers, you need to make sure that they’re following appropriate security standards.
Whichever SOC 2 compliance software you choose, get the most out of it by integrating it into the product and task management tools in ClickUp.
The ClickUp security policy takes compliance with security frameworks seriously, so you can trust that the data you store on the program stays safe.
While the powerful productivity tools in ClickUp’s free project management software will keep your teams collaborating effectively and working together smoothly, our security experts will be working in the background to give you the peace of mind you need. Try ClickUp for free today!
© 2026 ClickUp