As a network security analyst, staying on top of the ever-evolving world of cybersecurity is no easy task. That's why having a well-structured and organized meeting agenda is crucial to ensure your discussions are efficient and effective. Introducing ClickUp's Network Security Analysts Meeting Agenda Template!
With this template, you can:
- Structure and guide discussions on vulnerability assessments, threat intelligence, incident response, and more.
- Keep your team focused and productive by addressing critical security concerns.
- Evaluate security tools and implement risk mitigation strategies with ease.
Don't waste time fumbling through disorganized meetings. Get ClickUp's Network Security Analysts Meeting Agenda Template today and take control of your cybersecurity discussions!
Benefits of Network Security Analysts Meeting Agenda Template
When using the Network Security Analysts Meeting Agenda Template, you can expect the following benefits:
- Streamlined meetings that stay on track and cover all important security topics
- Clear and structured discussions on vulnerability assessments, threat intelligence, incident response, security tool evaluation, and risk mitigation strategies
- Increased productivity as meetings are focused and time is utilized efficiently
- Comprehensive documentation of meeting discussions and action items for easy reference and follow-up
- Consistent and standardized meeting format that ensures all critical security concerns are addressed
Main Elements of Network Security Analysts Meeting Agenda Template
To ensure productive and efficient network security analyst meetings, ClickUp's Network Security Analysts Meeting Agenda template offers the following key elements:
- Custom Statuses: Utilize statuses such as To Do, In Progress, and Completed to track the progress and completion of agenda items during the meeting.
- Custom Fields: Include custom fields like Topic, Presenter, Time Allocation, and Priority to provide essential details for each agenda item.
- Different Views: Switch between different views, such as Table view for a structured overview of the agenda, Board view for a visual representation of agenda items, and Calendar view for scheduling and tracking meeting dates.
With this template, network security analysts can effectively plan, discuss, and address important topics during their meetings, ensuring a smooth and productive workflow.
How to Use Meeting Agenda for Network Security Analysts
To ensure a productive and efficient network security analysts meeting, follow these four steps when using the Meeting Agenda Template:
1. Set the meeting objectives
Before the meeting, determine what specific goals you want to achieve during the session. Are you discussing recent security threats, reviewing network vulnerabilities, or planning future security measures? Clearly defining the meeting objectives will help keep the discussion focused and ensure that all necessary topics are covered.
Use Goals in ClickUp to outline the meeting objectives and track progress.
2. Identify discussion topics
Based on the meeting objectives, create a list of discussion topics that need to be addressed. This could include reviewing recent security incidents, analyzing network logs, discussing potential security solutions, or sharing best practices. Prioritize the topics to ensure that the most important ones are covered within the allocated meeting time.
Use the Board view in ClickUp to create cards for each discussion topic and easily move them around as priorities change.
3. Assign roles and responsibilities
To ensure a well-organized meeting, assign specific roles and responsibilities to each participant. This could include designating someone as the meeting facilitator, note-taker, or timekeeper. Clearly communicate these roles to everyone before the meeting so that each person knows their responsibilities and can contribute effectively.
Use Automations in ClickUp to automatically assign roles and responsibilities to team members based on predefined rules.
4. Share the agenda and relevant documents
Distribute the meeting agenda and any relevant documents to all participants well in advance of the meeting. This allows everyone to come prepared and familiarize themselves with the topics and materials. Encourage participants to review the agenda and documents beforehand to promote active engagement and productive discussions during the meeting.
Use the Calendar view in ClickUp to schedule the meeting and attach the agenda and documents directly to the event.
By following these steps and utilizing ClickUp's features, you can streamline your network security analysts meetings and ensure that important topics are discussed and decisions are made effectively.
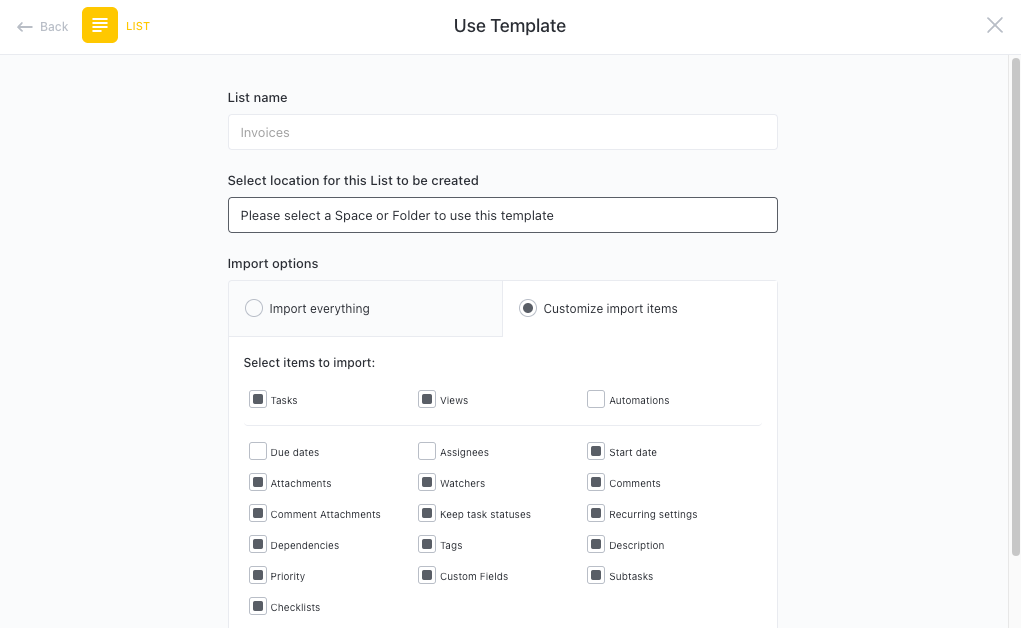
Get Started with ClickUp’s Network Security Analysts Meeting Agenda Template
Network security analysts and IT professionals can use this Meeting Agenda Template to structure and guide discussions on critical security concerns.
First, hit “Add Template” to sign up for ClickUp and add the template to your Workspace. Make sure you designate which Space or location in your Workspace you’d like this template applied.
Next, invite relevant members or guests to your Workspace to start collaborating.
Now you can take advantage of the full potential of this template to ensure productive meetings:
- Use the Vulnerability Assessments View to track and discuss vulnerabilities in the network
- The Threat Intelligence View will help you analyze and address potential security threats
- Utilize the Incident Response View to plan and strategize for handling security incidents effectively
- The Security Tool Evaluation View allows you to assess and discuss the performance of various security tools
- Organize agenda items into different statuses, such as Proposed, In Progress, Completed, to keep track of discussions
- Update statuses as you progress through agenda items to keep team members informed
- Monitor and analyze agenda items to ensure all critical security concerns are addressed