When it comes to cybersecurity, knowledge is power. That's why ClickUp's Vulnerability Assessment Executive Summary Template is a game-changer for organizations looking to protect their valuable data and assets.
With this template, you can:
- Gain a clear and concise overview of your system's security weaknesses
- Quantify and prioritize vulnerabilities based on their potential impact
- Access expert recommendations to address vulnerabilities effectively
Don't leave your organization at risk. Get the insights you need to fortify your defenses and stay one step ahead of potential threats. Try ClickUp's Vulnerability Assessment Executive Summary Template today and take control of your cybersecurity strategy.
Benefits of Vulnerability Assessment Executive Summary Template
When it comes to protecting your organization's digital assets, knowledge is power. The Vulnerability Assessment Executive Summary Template empowers you to take control of your security by:
- Providing a clear and concise overview of the vulnerabilities identified in your systems
- Enabling decision-makers to prioritize and address vulnerabilities based on their severity and potential impact
- Offering actionable recommendations to mitigate risks and strengthen your security posture
- Saving time and effort by summarizing complex technical information into a digestible format
- Ensuring that your organization stays ahead of potential threats and maintains a proactive approach to cybersecurity.
Main Elements of Vulnerability Assessment Executive Summary Template
When it comes to assessing vulnerabilities and keeping your executive team informed, ClickUp's Vulnerability Assessment Executive Summary template has you covered.
This Doc template includes:
- Custom Statuses: Track the progress of vulnerability assessments with custom statuses such as In Progress, Pending Review, and Completed.
- Custom Fields: Use custom fields to capture important information about vulnerabilities, including Severity Level, Risk Score, and Remediation Status.
- Different Views: Access the Vulnerability Assessment Executive Summary in various views, such as Document View, Table View, and Kanban View, to analyze and present vulnerability data in different formats.
With this template, you can easily create and share executive summaries that provide a comprehensive overview of your organization's vulnerabilities and their impact, ensuring your team stays informed and can take immediate action.
How to Use Executive Summary for Vulnerability Assessment
If you're looking to conduct a comprehensive vulnerability assessment and create an executive summary, follow these steps to ensure you cover all the necessary information:
1. Define the scope of the assessment
Before you begin your vulnerability assessment, it's important to clearly define the scope of the assessment. Determine the assets, systems, and networks that will be included in the assessment. This will help you focus your efforts and ensure that you cover all the necessary areas.
Use custom fields in ClickUp to create tags or labels to categorize and track the assets included in the assessment.
2. Identify potential vulnerabilities
Next, conduct a thorough analysis of your systems, networks, and processes to identify potential vulnerabilities. This can include software vulnerabilities, misconfigurations, weak passwords, or any other weaknesses that could be exploited by attackers.
Create tasks in ClickUp to document and track each potential vulnerability that you identify.
3. Assess the impact and likelihood of exploitation
Once you've identified potential vulnerabilities, assess the impact and likelihood of exploitation for each one. Consider the potential consequences of a successful attack, as well as how likely it is for the vulnerability to be exploited.
Use custom fields in ClickUp to assign a risk level to each vulnerability and document the potential impact and likelihood of exploitation.
4. Prioritize vulnerabilities
Based on the impact and likelihood of exploitation, prioritize the vulnerabilities that need to be addressed first. Focus on vulnerabilities that have a high impact and high likelihood of exploitation, as these pose the greatest risk to your organization.
Use the Gantt chart in ClickUp to create a timeline for addressing each vulnerability and prioritize tasks accordingly.
5. Develop a remediation plan
Once you've prioritized the vulnerabilities, develop a remediation plan to address each one. This plan should outline the steps that need to be taken to mitigate or eliminate each vulnerability. Include specific actions, timelines, and responsible parties for each step.
Create tasks in ClickUp to outline the steps in your remediation plan and assign them to the appropriate team members.
6. Create the executive summary
Finally, compile all the information gathered throughout the vulnerability assessment into an executive summary. This summary should provide an overview of the assessment, including the scope, identified vulnerabilities, risk levels, and prioritized remediation plan.
Use Docs in ClickUp to create a professional and comprehensive executive summary that can be easily shared with stakeholders.
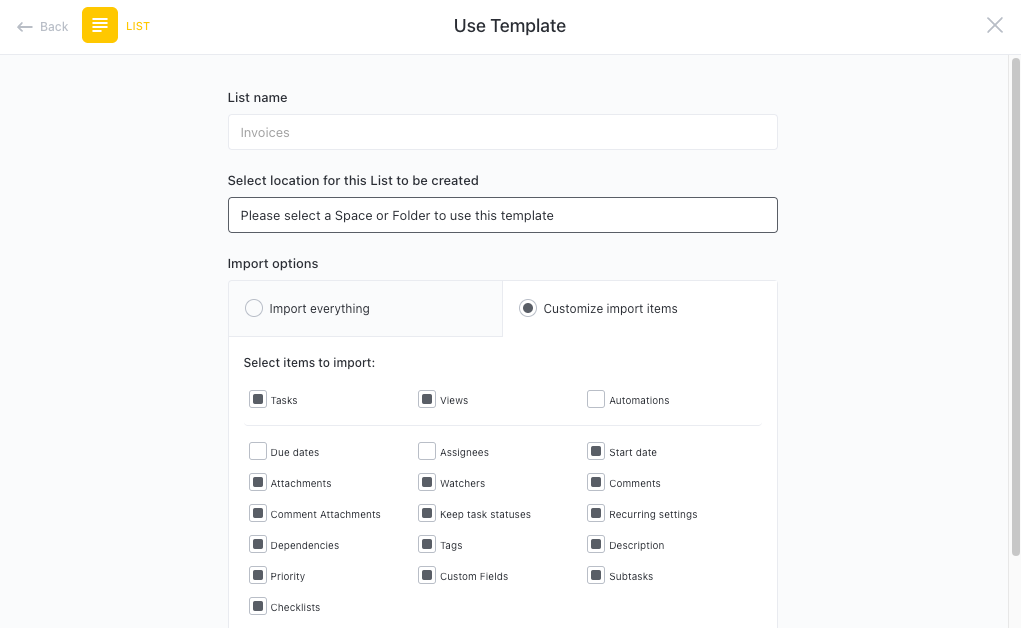
Get Started with ClickUp’s Vulnerability Assessment Executive Summary Template
Security teams can use this Vulnerability Assessment Executive Summary Template to provide decision-makers with a concise overview of the key findings and recommendations from a vulnerability assessment, enabling them to prioritize and address vulnerabilities effectively.
First, hit “Add Template” to sign up for ClickUp and add the template to your Workspace. Make sure you designate which Space or location in your Workspace you’d like this template applied.
Next, invite relevant members or guests to your Workspace to start collaborating.
Now you can take advantage of the full potential of this template to create an executive summary:
- Use the Summary View to provide a high-level overview of the vulnerability assessment, including the scope, methodology, and key findings.
- The Recommendations View will help you outline actionable steps to address the identified vulnerabilities.
- Utilize the Risk Matrix View to visually represent the severity and impact of each vulnerability.
- The Timeline View will allow you to track the progress of vulnerability remediation efforts.
- Organize vulnerabilities into different statuses, such as High Risk, Medium Risk, Low Risk, to prioritize and address them accordingly.
- Update the status of vulnerabilities as they are remediated or mitigated to track progress.
- Monitor and analyze vulnerabilities to ensure maximum security posture.