As a network security analyst, staying one step ahead of potential threats is crucial. That's why ClickUp's Network Security Analysts SWOT Analysis Template is a game-changer for your team.
This template allows you to conduct a comprehensive SWOT analysis of your organization's network security systems and processes, helping you:
- Identify strengths that can be leveraged to enhance security measures
- Uncover weaknesses and vulnerabilities that need immediate attention
- Discover opportunities to further enhance network security
- Pinpoint potential threats and create strategies to mitigate them
With ClickUp's SWOT Analysis Template, you can strengthen your network security and protect your organization from any potential threats. Don't wait, get started today!
Benefits of Network Security Analysts SWOT Analysis Template
Assessing the strengths, weaknesses, opportunities, and threats of your network security systems is crucial for effective protection against cyber threats. The Network Security Analysts SWOT Analysis Template provides numerous benefits, including:
- Identifying vulnerabilities and weaknesses in your network security infrastructure
- Leveraging strengths to enhance your current security measures
- Identifying opportunities to improve your network security and stay ahead of emerging threats
- Evaluating potential threats and developing proactive strategies to mitigate risks
- Enhancing your overall network security posture and ensuring the confidentiality and integrity of your data.
Main Elements of Network Security Analysts SWOT Analysis Template
ClickUp's Network Security Analysts SWOT Analysis template provides a comprehensive framework for analyzing your network's strengths, weaknesses, opportunities, and threats. Here are the main elements of this task template:
- Custom Statuses: Track the progress of your SWOT analysis using statuses like In Progress, Completed, and Review to keep your team aligned and on track.
- Custom Fields: Utilize custom fields such as Worksheet Link, Completion Rate, Objective, and Timeline to capture specific information about each aspect of your analysis and ensure all relevant data is readily available.
- Custom Views: Access different views like the SWOT Matrix, Action Plan, and Progress Tracker to visualize and manage your analysis from different perspectives, ensuring a holistic approach to network security.
- Task Management: Leverage ClickUp's task management features, including assigning tasks to team members, setting due dates, and adding attachments, to streamline collaboration and ensure timely completion of your SWOT analysis.
How to Use SWOT Analysis for Network Security Analysts
Analyzing the strengths, weaknesses, opportunities, and threats (SWOT) of your network security can help you identify areas for improvement and develop a stronger security strategy. Follow these steps to effectively use the Network Security Analysts SWOT Analysis Template:
1. Identify strengths
Start by identifying the strengths of your network security system. What are the areas where your security measures excel? This could include factors such as robust firewalls, regular software updates, or strong encryption protocols.
Use custom fields in ClickUp to list and categorize your network security strengths.
2. Identify weaknesses
Next, identify the weaknesses or vulnerabilities in your network security. Are there any areas where you are lacking in terms of protection or where potential threats could exploit? This could include factors such as outdated software, weak passwords, or lack of employee training.
Use tasks in ClickUp to create a list of weaknesses and assign team members to address each one.
3. Identify opportunities
Look for opportunities to improve your network security. Are there any emerging technologies or best practices that you can leverage? This could include factors such as implementing multi-factor authentication, conducting regular security audits, or utilizing AI-powered threat detection.
Use Automations in ClickUp to set up reminders and notifications for potential security opportunities.
4. Identify threats
Lastly, identify the potential threats or risks that your network security system faces. This could include factors such as malware attacks, phishing attempts, or insider threats. Understanding the specific threats you face will help you develop targeted strategies to mitigate them.
Use the Calendar view in ClickUp to schedule regular reviews and updates of your network security threats.
By following these steps and utilizing the Network Security Analysts SWOT Analysis Template in ClickUp, you can gain valuable insights into your network security and take proactive steps to enhance your defenses.
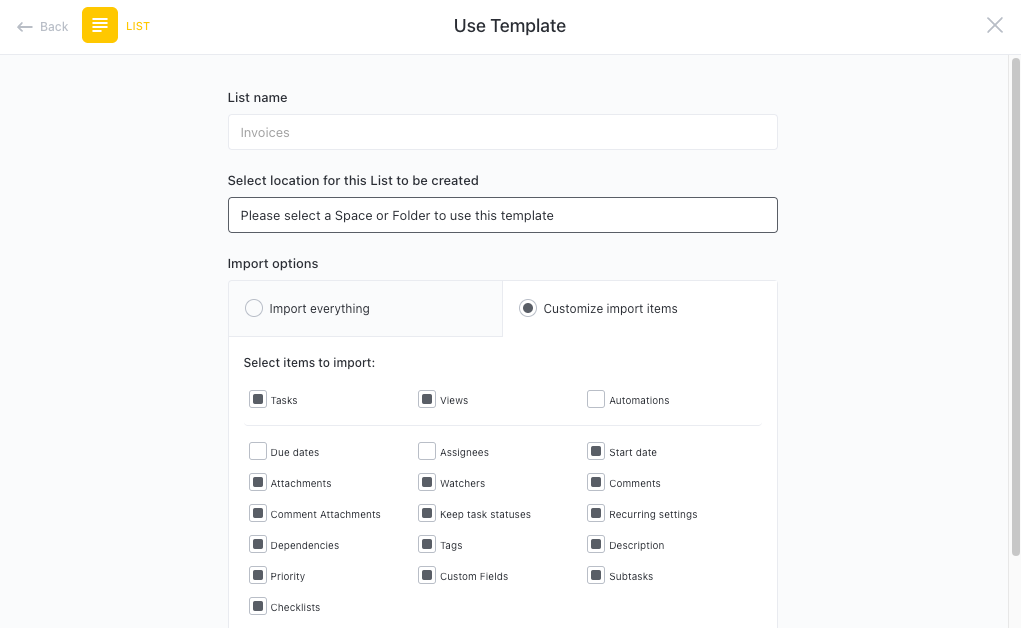
Get Started with ClickUp’s Network Security Analysts SWOT Analysis Template
Network security analysts can use the SWOT Analysis Template to assess and enhance their organization's network security systems.
To get started, hit “Add Template“ to sign up for ClickUp and add the template to your Workspace. Make sure to designate the appropriate Space or location in your Workspace for this template.
Next, invite relevant members or guests to your Workspace to collaborate on the SWOT analysis.
Here's how you can make the most of this template:
- Use the Strengths view to identify and list the current strengths of your network security systems and processes
- Utilize the Weaknesses view to pinpoint any vulnerabilities or areas for improvement in your network security
- Explore the Opportunities view to identify potential opportunities for enhancing network security and staying ahead of threats
- Assess the Threats view to understand and list potential risks and threats to your network security
- Organize your analysis into appropriate statuses to track progress and prioritize actions
- Update statuses as you address and mitigate each identified strength, weakness, opportunity, and threat
- Analyze the results of your SWOT analysis to develop an action plan for strengthening network security
By using this template, network security analysts can proactively evaluate and enhance their organization's network security systems for maximum protection against threats.