When it comes to IT security, prevention is key. That's why information technology departments rely on risk register templates to stay one step ahead of potential threats. ClickUp's Information Technology Risk Register Template is a game-changer for IT teams who want to identify, assess, and manage risks effectively. With this template, you can:
- Identify potential risks and vulnerabilities in your IT systems
- Assess the impact and likelihood of each risk to prioritize your efforts
- Create action plans to mitigate risks and enhance security measures
Don't leave your IT infrastructure vulnerable to attacks. Take control of your technology risks with ClickUp's IT Risk Register Template today!
Benefits of Information Technology Risk Register Template
When it comes to safeguarding your organization's IT systems, having a risk register template is a game-changer. Here are some benefits of using this template:
- Comprehensive risk identification and assessment, ensuring that no potential risks go unnoticed
- Proactive risk management, allowing you to implement preventive measures and minimize the impact of potential threats
- Enhanced security and data integrity, safeguarding your IT systems from unauthorized access or data breaches
- Improved compliance with industry regulations and standards, reducing the risk of penalties or legal issues
- Better decision-making, as you have a clear overview of your IT risks and can prioritize mitigation efforts accordingly
Main Elements of Information Technology Risk Register Template
ClickUp's Information Technology Risk Register Template is the ultimate tool to manage and mitigate risks in your IT projects. Here are the main elements of this template:
- Custom Statuses: Easily track the progress of each risk with 9 different statuses including Occurred, Mitigated, and Active. This helps you stay on top of the risk management process and ensure timely action.
- Custom Fields: Capture all relevant information about each risk with 7 custom fields such as Consequence, Description, and Risk Level. This allows you to assess the severity and impact of each risk and make informed decisions.
- Custom Views: Access 6 different views including Costs of Risks, List of Risks, and Risks by Status. These views provide different perspectives on your risk register and help you analyze data efficiently.
- Getting Started Guide: Use the built-in guide to quickly understand how to set up and make the most out of the template. It provides step-by-step instructions and best practices for effective risk management in IT projects.
How to Use Risk Register for Information Technology
Managing IT risks is crucial for any organization to ensure the security and reliability of their technology systems. By following these steps, you can effectively use the Information Technology Risk Register Template in ClickUp to identify and mitigate potential IT risks.
1. Identify potential risks
Start by brainstorming and identifying the potential IT risks that your organization may face. This can include risks related to cybersecurity, data breaches, system failures, and regulatory compliance.
Use custom fields in ClickUp to categorize and prioritize each identified risk.
2. Assess the impact and likelihood
Once you have identified the potential risks, assess the impact and likelihood of each risk occurring. Consider the potential consequences, such as financial loss, reputational damage, and operational disruptions.
Use custom fields in ClickUp to assign impact and likelihood scores to each risk.
3. Evaluate existing controls
Next, evaluate the existing controls and measures that are currently in place to mitigate each risk. This can include firewalls, antivirus software, access controls, backup systems, and employee training programs.
Use custom fields in ClickUp to document and assess the effectiveness of each control.
4. Develop risk mitigation strategies
Based on the assessment of risks and existing controls, develop specific risk mitigation strategies for each identified risk. These strategies can include implementing additional security measures, conducting regular vulnerability assessments, establishing incident response plans, and enhancing employee training programs.
Use tasks in ClickUp to create action plans for each risk mitigation strategy.
5. Monitor and review
Once the risk mitigation strategies are implemented, it is important to continuously monitor and review the effectiveness of these strategies. Regularly update the risk register in ClickUp with any new risks that may arise and track the progress of each risk mitigation strategy.
Use Automations in ClickUp to set up reminders and notifications for regular risk assessments and reviews.
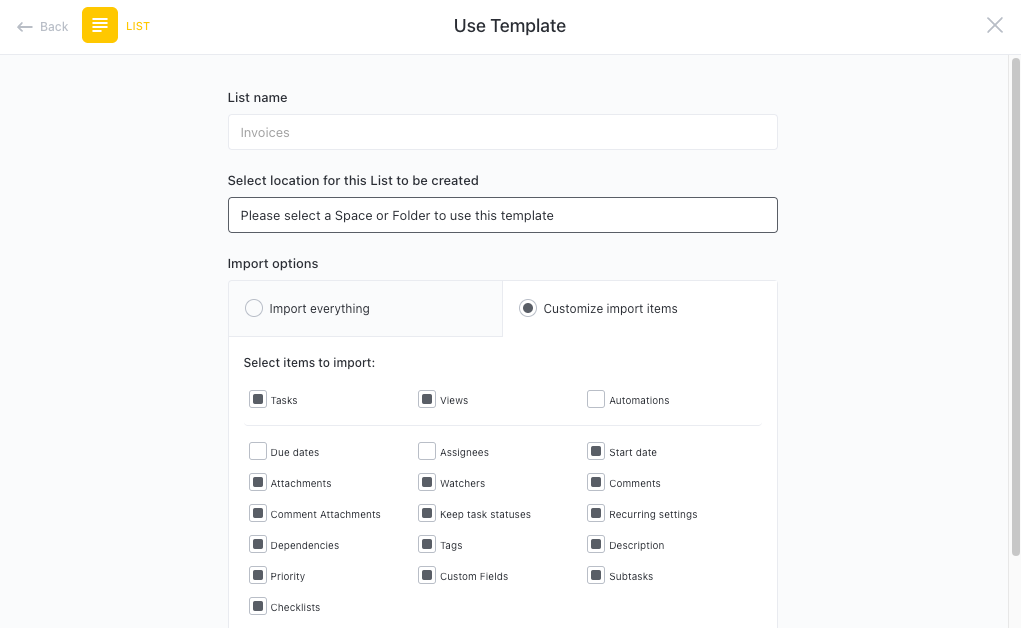
Get Started with ClickUp’s Information Technology Risk Register Template
IT departments can use the Information Technology Risk Register Template to effectively manage and mitigate potential risks associated with their technology systems and infrastructure.
To get started, hit “Add Template“ to sign up for ClickUp and add the template to your Workspace. Make sure you designate which Space or location in your Workspace you’d like this template applied.
Next, invite relevant members or guests to your Workspace to start collaborating.
Now you can leverage the power of this template to identify and manage IT risks:
- Use the Costs of Risks View to calculate the potential financial impact of each risk
- The List of Risks View provides a comprehensive overview of all identified risks for easy reference
- The Risks by Status View allows you to track risks based on their current status, such as Occurred, Mitigated, or Active
- Assess risks based on their response level using the Risks by Response View
- The Risks by Level View helps you prioritize risks based on their severity and impact
- Consult the Getting Started Guide View for step-by-step instructions on implementing the risk register template
- Organize risks into nine different statuses, including Occurred, Mitigated, and Active, to monitor progress and take appropriate action
- Update statuses as you address and mitigate risks to ensure stakeholders are informed of progress
- Monitor and analyze risks to proactively manage potential IT vulnerabilities and ensure maximum security and resilience