In today's digital age, cyber threats are constantly evolving, making it crucial for organizations to stay one step ahead. That's where ClickUp's Cyber Security Risk Register Template comes in.
This template empowers businesses to proactively identify and manage potential risks, allowing them to:
- Document and evaluate cyber risks in a centralized location
- Implement effective risk mitigation strategies to protect digital assets
- Maintain the integrity of information systems and ensure data security
Whether you're a small startup or a large enterprise, ClickUp's Cyber Security Risk Register Template is your go-to solution for keeping your organization safe from cyber threats. Take control of your cybersecurity today!
Benefits of Cyber Security Risk Register Template
Protecting your organization from cyber threats is crucial in today's digital landscape. The Cyber Security Risk Register Template provides several benefits for organizations looking to safeguard their data and systems:
- Enables proactive identification of potential cyber risks
- Facilitates documentation and evaluation of identified risks
- Helps prioritize and allocate resources for risk mitigation
- Enhances communication and collaboration among stakeholders
- Provides a centralized repository for tracking and monitoring cyber risks
- Supports compliance with industry regulations and standards
- Assists in maintaining the integrity and confidentiality of sensitive information
- Ensures business continuity by minimizing the impact of cyber incidents.
Main Elements of Cyber Security Risk Register Template
ClickUp's Cyber Security Risk Register Template is designed to help you effectively manage and mitigate cyber risks. Here are the main elements of this Folder template:
- Custom Statuses: Keep track of the progress of each risk with 9 different statuses, including Occurred, Mitigated, and Active, to easily identify the current state of each risk in your cyber security risk register.
- Custom Fields: Capture essential information about each risk with 7 custom fields, such as Consequence, Description, Expected Cost of Risk, Mitigation Cost, Probability, Risk Level, and Risk Response, allowing you to assess and prioritize risks accurately.
- Custom Views: Access 6 different views, including Costs of Risks, List of Risks, Risks by Status, Risks by Response, Risks by Level, and the Getting Started Guide, to gain different perspectives on your cyber security risks and effectively manage them.
- Collaboration Tools: Collaborate with your team by assigning tasks, setting due dates, and adding comments directly within the template to ensure everyone is aligned on risk mitigation efforts.
How to Use Risk Register for Cyber Security
Protecting your organization from cyber threats is crucial in today's digital world. By using the Cyber Security Risk Register template in ClickUp and following the steps outlined below, you can proactively manage and mitigate potential risks to your business.
1. Identify potential risks
The first step in using the Cyber Security Risk Register template is to identify potential risks that your organization may face. This includes vulnerabilities in your systems, potential data breaches, and any other cyber threats that could impact your business.
Use custom fields in ClickUp to categorize and prioritize different types of risks, such as external threats, internal vulnerabilities, or third-party risks.
2. Assess the impact and likelihood
Once you've identified potential risks, it's important to assess the impact and likelihood of each risk occurring. This will help you prioritize your efforts and allocate resources effectively.
Use custom fields in ClickUp to assess the impact and likelihood of each risk, such as assigning a numerical value to each category and calculating an overall risk score.
3. Implement risk mitigation strategies
After assessing the impact and likelihood of each risk, it's time to develop and implement risk mitigation strategies. This may include implementing security measures, creating backup systems, or training employees on best practices.
Use tasks in ClickUp to assign specific actions to team members and track the progress of each risk mitigation strategy.
4. Regularly review and update
Cybersecurity risks are constantly evolving, so it's important to regularly review and update your Cyber Security Risk Register. This ensures that you are staying up-to-date with the latest threats and adjusting your risk mitigation strategies accordingly.
Set a recurring task in ClickUp to review and update your Cyber Security Risk Register on a regular basis, such as monthly or quarterly, to ensure that your organization is always prepared for potential cyber threats.
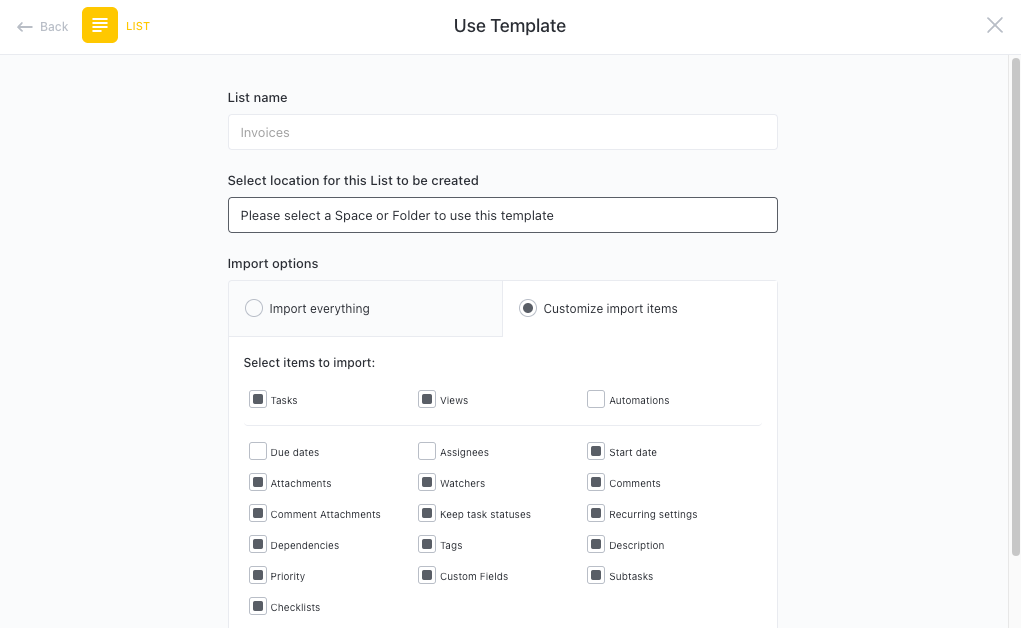
Get Started with ClickUp’s Cyber Security Risk Register Template
Organizations that prioritize cybersecurity and want to proactively identify and manage potential risks related to cyber threats can use the Cyber Security Risk Register Template to maintain the integrity of their information systems.
First, hit “Add Template” to sign up for ClickUp and add the template to your Workspace. Make sure you designate which Space or location in your Workspace you’d like this template applied.
Next, invite relevant members or guests to your Workspace to start collaborating.
Now you can take advantage of the full potential of this template to manage cybersecurity risks:
- Use the Costs of Risks View to track the financial impact of each risk
- The List of Risks View will provide a comprehensive list of all identified risks
- The Risks by Status View will help you monitor the progress of each risk by their current status
- Use the Risks by Response View to categorize risks based on the mitigation strategy applied
- The Risks by Level View will prioritize risks based on their severity and potential impact
- Refer to the Getting Started Guide View to get acquainted with the template and its features
- Organize risks into nine different statuses: Occurred, Mitigated, Active, to keep track of their current state
- Update statuses as risks occur, are mitigated, or become active to maintain an accurate overview
- Monitor and analyze risks to ensure maximum cybersecurity protection.