Looking for the perfect vulnerability management tool to keep your organization's systems and networks secure? Look no further than ClickUp's Vulnerability Management Tool RFP Template! With this template, you can easily assess and manage potential security vulnerabilities by following a structured and efficient process.
Here's what you can achieve with ClickUp's Vulnerability Management Tool RFP Template:
- Streamline the vendor selection process by outlining your specific requirements and evaluating different options
- Ensure that the chosen tool meets your organization's unique needs and security standards
- Save time and effort by using a ready-made template that guides you through the entire RFP process
Don't compromise on your organization's security. Get started with ClickUp's Vulnerability Management Tool RFP Template today and find the perfect solution to protect your systems and networks!
Benefits of Vulnerability Management Tool RFP Template
Finding the right vulnerability management tool is crucial for organizations looking to protect their systems and networks. By using the Vulnerability Management Tool RFP Template, you can:
- Streamline the vendor selection process by clearly defining your requirements and evaluation criteria
- Ensure that all potential vendors provide the necessary information to make an informed decision
- Save time and effort by leveraging a pre-built template that covers all the essential aspects of a vulnerability management tool RFP
- Increase the likelihood of selecting the best tool for your organization's unique needs and security objectives
Main Elements of Vulnerability Management Tool RFP Template
ClickUp's Vulnerability Management Tool RFP template is designed to streamline the process of evaluating and selecting a vulnerability management solution. Here are the main elements of this template:
- Custom Statuses: Keep track of the progress of each vendor's response with custom statuses such as Submitted, In Review, and Approved.
- Custom Fields: Use custom fields to capture important information about each vendor, including their pricing, features, support options, and compliance certifications.
- Different Views: Utilize different views to analyze and compare vendor responses. For example, use the Table view to easily compare pricing and features side by side, or the Board view to visualize the progress of each vendor's evaluation process.
With this template, you can efficiently manage the entire RFP process, from initial vendor selection to final decision-making.
How to Use RFP for Vulnerability Management Tool
If you're in the market for a vulnerability management tool and need to create an RFP (Request for Proposal), follow these steps to ensure you find the right solution for your organization:
1. Define your requirements
Before creating your RFP, it's important to determine the specific requirements and features you need in a vulnerability management tool. Consider factors such as the size of your organization, the number of assets you need to protect, compliance requirements, and any specific functionality you require.
Use custom fields in ClickUp to create a checklist of your requirements and prioritize them based on importance.
2. Research potential vendors
Once you have a clear understanding of your requirements, start researching potential vendors who offer vulnerability management tools. Look for vendors that have a good reputation, offer the features you need, and have experience working with organizations similar to yours.
Use the Table view in ClickUp to create a table of potential vendors and add columns for key information such as vendor name, features, pricing, and customer reviews.
3. Create your RFP
Using the information gathered from your requirements and vendor research, create your RFP document. Be sure to include a detailed description of your organization, the specific requirements you're looking for, any necessary integrations, implementation timelines, and evaluation criteria.
Use a Doc in ClickUp to create your RFP document and easily collaborate with stakeholders by sharing a link to the document.
4. Evaluate and select a vendor
Once you've sent out your RFP to potential vendors, evaluate their responses based on their ability to meet your requirements, pricing, implementation timeline, customer support, and any other factors that are important to your organization. Consider scheduling demos or requesting references to further assess each vendor's suitability.
Use Dashboards in ClickUp to track and evaluate vendor responses, compare proposals side by side, and make an informed decision based on your evaluation criteria.
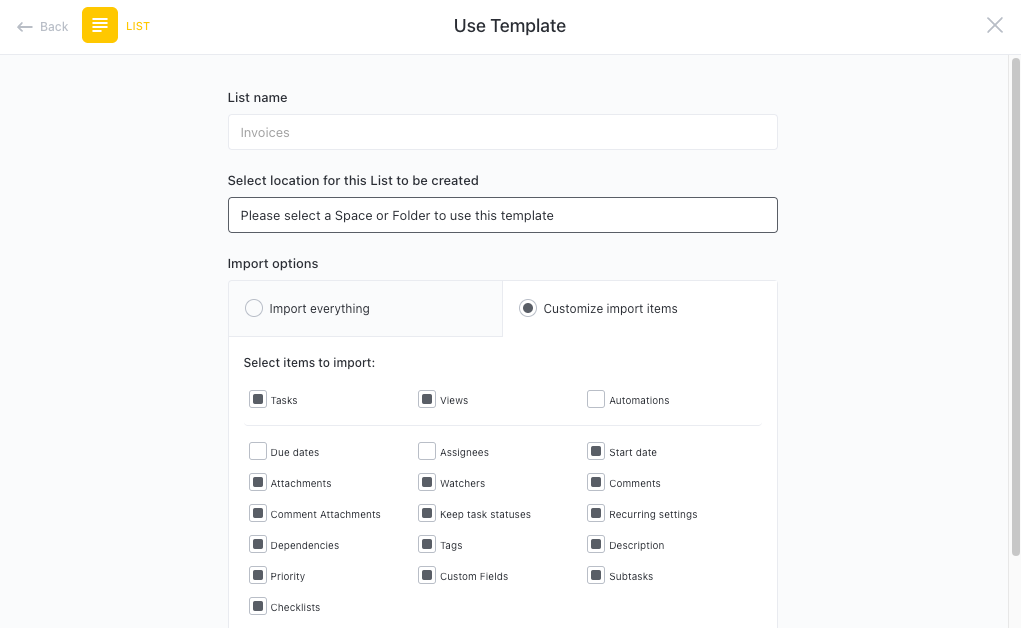
Get Started with ClickUp’s Vulnerability Management Tool RFP Template
Organizations looking to enhance their security measures can use the Vulnerability Management Tool RFP Template to streamline the vendor selection process and find the perfect solution.
First, hit “Add Template” to sign up for ClickUp and add the template to your Workspace. Make sure you designate which Space or location in your Workspace you’d like this template applied.
Next, invite relevant members or guests to your Workspace to start collaborating.
Now you can take advantage of the full potential of this template to manage your RFP process:
- Use the RFP Overview section to provide an introduction and background information about your organization
- Customize the RFP Requirements section to outline your specific security needs and expectations
- Create a checklist of evaluation criteria to help you assess vendors objectively
- Use the Vendor Evaluation section to score each vendor's proposal and compare them side by side
- Collaborate with team members to review and discuss proposals, making notes and providing feedback
- Schedule meetings with potential vendors to ask clarifying questions and gather additional information
- Finally, use the Decision Log section to document your final decision and reasons for choosing a specific vendor
By following these steps, you can confidently select a vulnerability management tool that fits your organization's security requirements.