In today's digital age, cyber security is more important than ever. Protecting your organization from cyber threats requires a well-defined and comprehensive set of Standard Operating Procedures (SOPs). That's where ClickUp's Cyber Security SOP Template comes in!
With ClickUp's Cyber Security SOP Template, you can:
- Establish clear guidelines and protocols for handling cyber security incidents
- Document and communicate best practices for data protection and privacy
- Train your team on how to respond to potential threats and vulnerabilities
Whether you're a small business or a large enterprise, this template will help you fortify your cyber defenses and ensure the safety of your sensitive information. Get started with ClickUp's Cyber Security SOP Template today and safeguard your organization from cyber threats.
Benefits of Cyber Security SOP Template
When it comes to cyber security, having a standardized operating procedure (SOP) is crucial for protecting your organization from potential threats. Here are some of the benefits of using the Cyber Security SOP Template:
- Ensures consistent and thorough security protocols across your organization
- Helps identify and mitigate potential vulnerabilities and risks
- Provides a clear roadmap for responding to security incidents and breaches
- Streamlines communication and collaboration between IT teams and stakeholders
- Saves time and effort by providing a pre-built framework that can be customized to fit your specific needs
- Enhances compliance with industry regulations and best practices
Main Elements of Cyber Security SOP Template
ClickUp's Cyber Security SOP Template is designed to help you create and maintain standard operating procedures for your organization's cybersecurity practices.
This Doc template contains all the necessary sections and content to guide you in documenting your cybersecurity processes. It also includes ClickUp features such as:
- Custom Statuses: Break down your cybersecurity procedures into different stages or statuses to track progress and ensure completion
- Custom Fields: Add custom fields to categorize and provide additional information about each procedure, such as priority level, responsible team members, or due dates
- Custom Views: Utilize different views like List, Board, or Calendar to organize and visualize your cybersecurity SOPs in a way that suits your workflow
- Project Management: Enhance your cybersecurity processes with ClickApps like Automations, Dependencies, Tags, and Integrations with other security tools.
How to Use SOP for Cyber Security
Protecting your organization from cyber threats is crucial in today's digital age. By using the Cyber Security SOP Template in ClickUp and following the steps outlined below, you can establish a robust cyber security framework and ensure the safety of your sensitive data.
1. Assess your current security measures
Before implementing any new procedures, it's important to assess your organization's current cyber security measures. Identify any vulnerabilities or gaps in your existing system to determine where improvements are needed.
Use the Gantt chart in ClickUp to create a timeline for conducting a thorough assessment of your organization's cyber security practices.
2. Define your security policies and procedures
Once you have identified areas for improvement, it's time to establish clear and comprehensive security policies and procedures. This includes guidelines for password management, data encryption, network access, and incident response.
Create tasks in ClickUp to outline and document each security policy and procedure, ensuring that they are easily accessible to all employees.
3. Train your employees
Cyber security is a team effort, and every employee plays a vital role in protecting your organization's data. Conduct regular training sessions to educate your staff about best practices for identifying and mitigating cyber threats.
Use Automations in ClickUp to schedule and automate recurring training sessions and track employee participation.
4. Implement security controls
To strengthen your organization's cyber security, it's important to implement robust security controls. This can include multi-factor authentication, firewalls, antivirus software, and intrusion detection systems.
Use custom fields in ClickUp to track the implementation and maintenance of each security control, ensuring that they are regularly updated and monitored.
5. Regularly review and update your SOPs
Cyber threats are constantly evolving, so it's essential to regularly review and update your Standard Operating Procedures (SOPs) to stay ahead of potential risks. Conduct periodic audits to ensure that your cyber security measures are effective and up to date.
Set recurring tasks in ClickUp to review and update your SOPs on a regular basis, keeping your organization's cyber security framework current and robust.
By following these steps and utilizing the Cyber Security SOP Template in ClickUp, you can establish a strong cyber security foundation and protect your organization from potential threats.
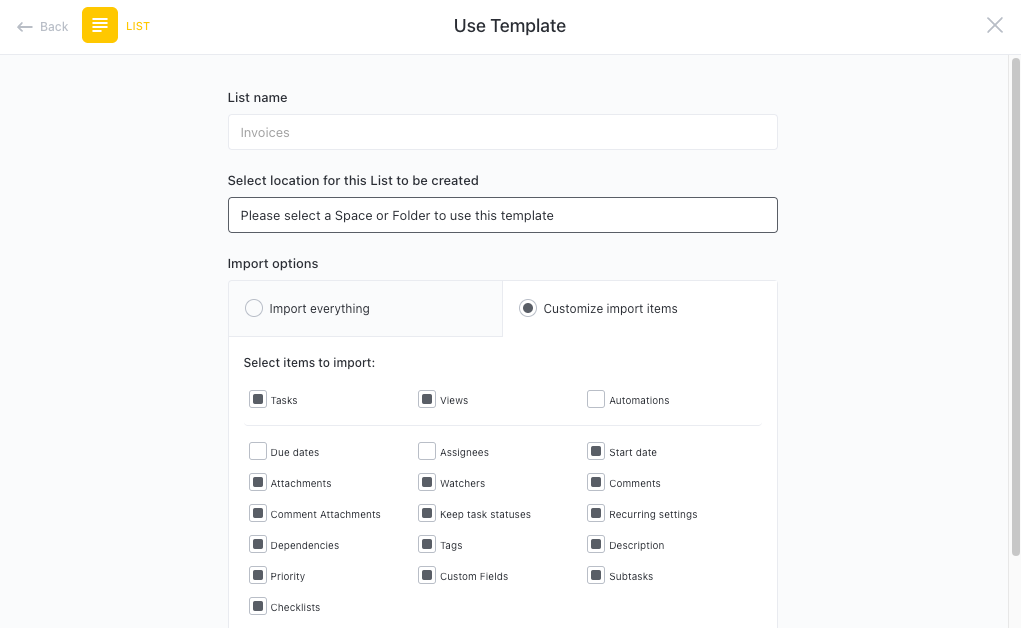
Get Started with ClickUp's Cyber Security SOP Template
IT teams can use this Cyber Security SOP (Standard Operating Procedures) Template to ensure consistent and effective security practices across the organization.
First, hit “Add Template” to sign up for ClickUp and add the template to your Workspace. Make sure you designate which Space or location in your Workspace you’d like this template applied.
Next, invite relevant members or guests to your Workspace to start collaborating.
Now you can take advantage of the full potential of this template to enhance cybersecurity:
- Create Docs to outline standard operating procedures for various cybersecurity practices such as password management, data backup, and incident response.
- Assign tasks to team members to ensure accountability and completion of SOPs.
- Use Checklists to break down each SOP into step-by-step actions.
- Attach relevant resources and documents to provide easy access to important information.
- Set up recurring tasks for regular review and update of SOPs to accommodate changes in technology and security threats.
- Utilize the Table view to track the progress of each SOP and identify any bottlenecks.
- Collaborate using Comments to discuss and provide feedback on the effectiveness of SOPs.
- Monitor and analyze tasks to ensure adherence to cybersecurity best practices and maximum protection against threats.