When it comes to protecting your organization's sensitive data and assets, staying one step ahead of potential threats is crucial. That's where ClickUp's Security Gap Analysis Template comes in handy!
Designed for IT professionals and security teams, this template helps you identify any vulnerabilities or weaknesses in your current security measures, so you can take proactive steps to fortify your defenses. With ClickUp's Security Gap Analysis Template, you can:
- Conduct a comprehensive assessment of your organization's security posture
- Prioritize actions and investments to address the most critical gaps
- Track progress and ensure ongoing security improvements
Don't leave your organization's security to chance. Get started with ClickUp's Security Gap Analysis Template today and stay one step ahead of potential threats.
Benefits of Security Gap Analysis Template
Securing your organization's data and systems is crucial in today's digital landscape. The Security Gap Analysis Template can help you achieve this by:
- Identifying potential security vulnerabilities and weaknesses within your current infrastructure
- Prioritizing actions and investments to strengthen your organization's overall security posture
- Ensuring compliance with industry standards and regulations
- Enhancing risk management and reducing the likelihood of security breaches
- Improving incident response capabilities and minimizing downtime in the event of an attack
Main Elements of Security Gap Analysis Template
When it comes to performing a comprehensive security gap analysis, ClickUp's Security Gap Analysis Template has got you covered with its powerful features:
- Custom Statuses: Keep track of the progress of your security analysis with custom statuses tailored to your organization's needs.
- Custom Fields: Capture vital information about security vulnerabilities and risk assessments with custom fields like Severity Level, Impact, and Mitigation Plan.
- Different Views: Visualize your security gap analysis from different perspectives with views like Kanban, Gantt chart, and Calendar view, allowing you to plan, track, and manage your security tasks effectively.
- Whiteboard Collaboration: Collaborate in real-time with your team on the Security Gap Analysis Whiteboard, where you can brainstorm ideas, outline action plans, and discuss mitigation strategies.
How to Use Gap Analysis for Security
To conduct a comprehensive security gap analysis and strengthen your organization's security measures, follow these steps:
1. Identify your assets and threats
Start by identifying all the assets within your organization that need protection, such as sensitive data, equipment, or intellectual property. Then, identify potential threats that could compromise the security of these assets, such as cyberattacks, physical breaches, or internal vulnerabilities.
Use the Goals feature in ClickUp to create a list of assets and threats to analyze.
2. Assess current security measures
Evaluate the effectiveness of your current security measures by examining your existing policies, procedures, and controls. Determine if they are aligned with industry best practices and regulatory requirements. Identify any gaps or weaknesses in your security system that need to be addressed.
Use the Doc feature in ClickUp to create a checklist of your current security measures for easy reference.
3. Conduct a risk assessment
Analyze the potential impact and likelihood of each identified threat on your assets. This will help you prioritize your efforts and allocate resources effectively. Consider the potential consequences of a security breach, such as financial loss, reputational damage, or legal ramifications.
Utilize custom fields in ClickUp to assign risk levels and probabilities to each threat.
4. Develop an action plan
Based on the results of your risk assessment, develop a detailed action plan to address the identified security gaps. Define specific tasks, assign responsibilities, and set deadlines for each action item. Prioritize the most critical gaps and ensure that your plan includes both short-term and long-term solutions.
Create tasks in ClickUp and use the Gantt chart view to visualize your action plan timeline.
5. Implement security measures
Put your action plan into action by implementing the necessary security measures. This may involve implementing new policies and procedures, conducting employee training, enhancing physical security measures, or deploying advanced cybersecurity tools. Regularly monitor the progress of your implementation and make adjustments as needed.
Utilize the Automations feature in ClickUp to automate certain security measures and streamline the implementation process.
6. Regularly evaluate and update
Security is an ongoing process, so it's crucial to regularly evaluate the effectiveness of your security measures and update them as needed. Conduct periodic security audits, track key security metrics, and encourage feedback from employees to identify any emerging security gaps. Continuously improve your security posture to stay ahead of evolving threats.
Use the Dashboards feature in ClickUp to monitor and track the effectiveness of your security measures over time.
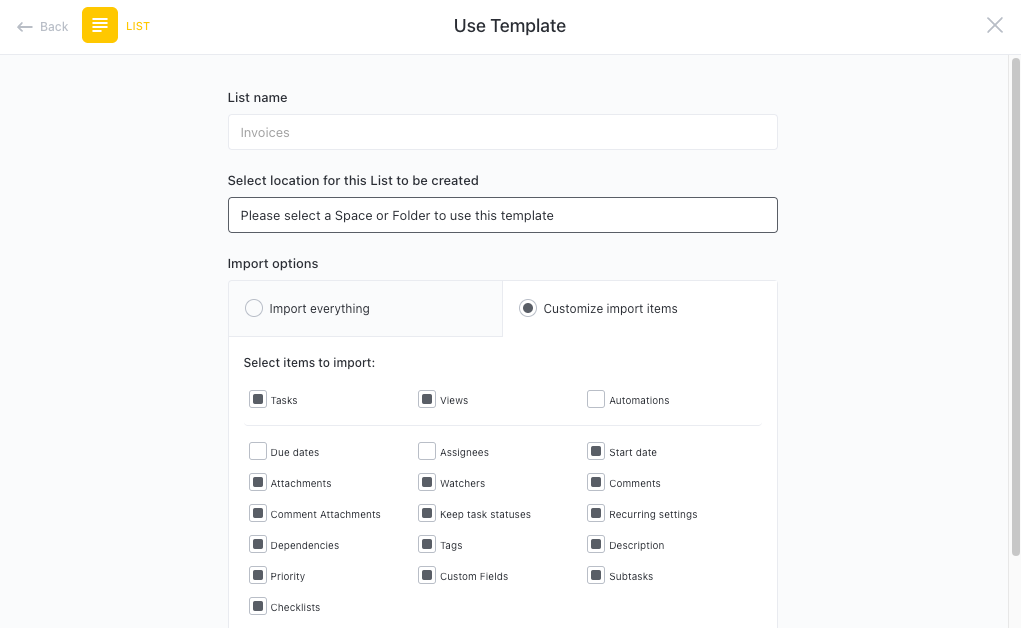
Get Started with ClickUp’s Security Gap Analysis Template
IT professionals or security teams can use this Security Gap Analysis Template to assess and improve their organization's security measures.
First, hit “Add Template” to sign up for ClickUp and add the template to your Workspace. Make sure you designate which Space or location in your Workspace you’d like this template applied.
Next, invite relevant members or guests to your Workspace to start collaborating.
Now you can take advantage of the full potential of this template to conduct a thorough security analysis:
- Use the Inventory view to list all the assets and systems that need to be evaluated
- The Risk Assessment view will help you identify potential vulnerabilities and prioritize mitigation efforts
- Use the Controls view to document existing security controls and identify any gaps
- The Remediation Plan view will help you create a step-by-step plan to address the identified gaps
- Organize tasks into different statuses (e.g., Identified, In Progress, Completed) to keep track of progress
- Update statuses as you address each security gap to ensure transparency and accountability
- Monitor and analyze the progress of each task to drive continuous improvement in security measures.