Master How to Use the AI Threat Model Generator
Demystifying the AI Threat Model Generator
An AI Threat Model Generator automates the complex process of identifying potential security threats in software architecture. Traditionally, threat modeling required manual input, cross-team collaboration, and was prone to outdated assessments that left systems vulnerable.
AI revolutionizes this by analyzing architecture diagrams, data flows, and system components dynamically. Simply prompt the AI with your system details, and it unveils potential attack vectors and mitigation strategies.
Integrated with platforms like ClickUp Brain, it transforms static threat models into living documents that adapt as your architecture evolves, ensuring your security posture stays proactive and resilient.
Why ClickUp Brain Excels as an AI Threat Model Generator
Conventional Threat Modeling Tools
- Isolated workflows: Often separate from development or project management systems, causing delays.
- Static reports: Generates fixed models that quickly become outdated.
- Manual updates: Requiring security experts to revise models after every change.
- Limited collaboration: Sharing models across teams can be cumbersome and insecure.
- Narrow analysis: Focused on predefined templates, missing evolving threat patterns.
ClickUp Brain
- Embedded in your workspace: Generates models linked to projects, tasks, and documentation.
- Real-time collaboration: Teams can co-author and update threat models instantly.
- Dynamic updating: Models evolve as architecture or code changes.
- Robust security controls: Ensures sensitive data stays protected with granular permissions.
- Brain Max capabilities: Leverages advanced logic to combine data sources for comprehensive threat analysis.
How to Generate an AI-Driven Threat Model
1. Gather Your System Architecture Data
Traditional approach: Manually collect diagrams, data flows, and component details from various teams.
With ClickUp Brain:
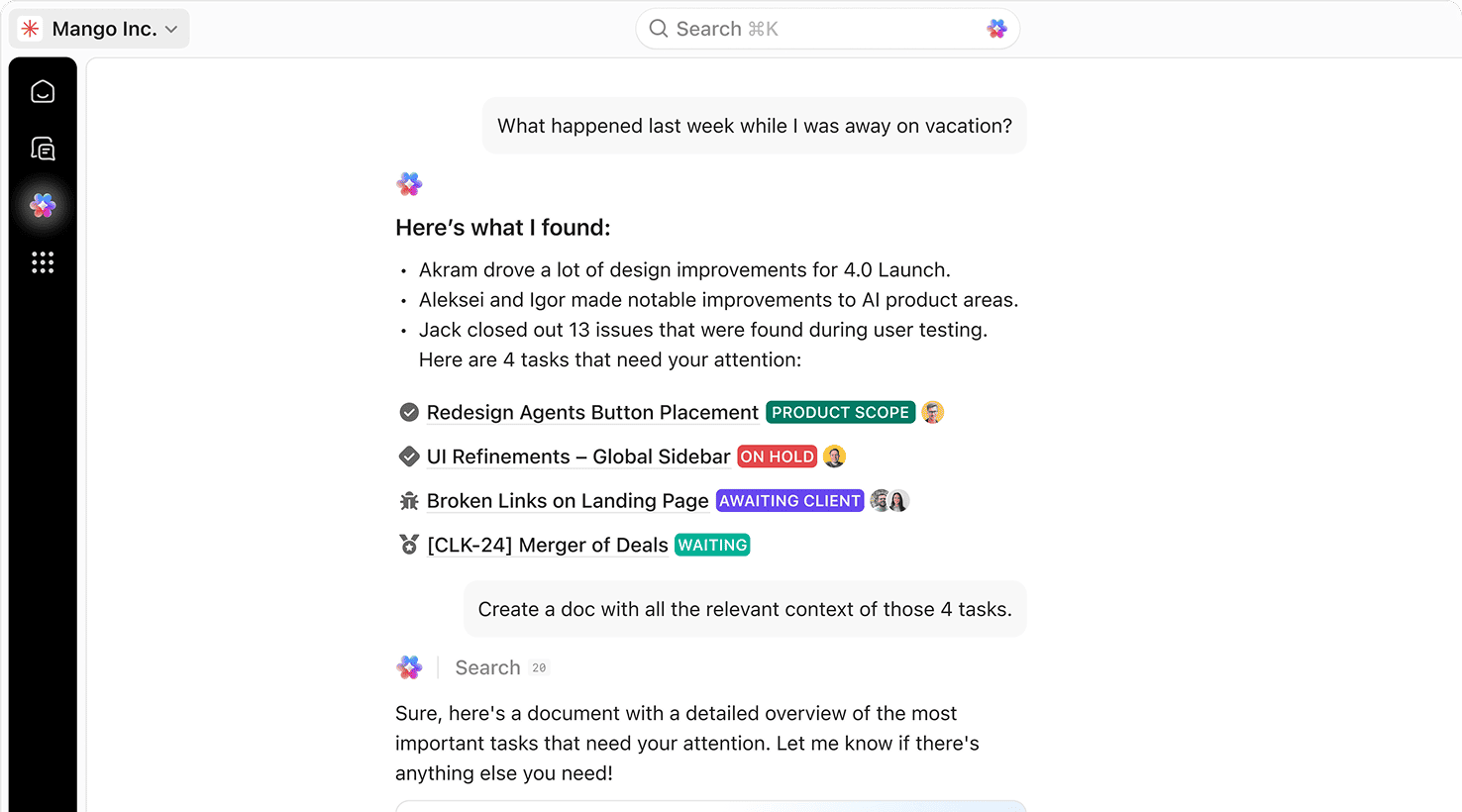
ClickUp aggregates your project documentation, code repositories, and architecture diagrams to build a foundational model automatically. Just instruct: “Generate a threat model for our payment processing system.”
2. Let AI Identify Potential Threats
Traditional approach: Security analysts manually assess each component, which is time-consuming and subjective.
With ClickUp Brain:
AI analyzes your system’s data flows, identifies attack surfaces, and maps threat agents using cybersecurity frameworks, delivering a prioritized list of risks based on real-time data.
3. Customize Your Security Controls
Traditional approach: Applying generic controls without adapting to your unique environment.
With ClickUp Brain:
Use interactive mind maps or whiteboards to tailor mitigation strategies, aligning them with your organization's policies and compliance requirements.
4. Maintain a Living Threat Model
Traditional approach: Static documents that become obsolete as systems evolve.
With ClickUp Brain:
Threat models automatically update with system changes, ensuring continuous protection and enabling quick responses to emerging threats.
Three Impactful Use Cases for the AI Threat Model Generator
Accelerated Security Reviews in Agile Development
Security teams integrate AI-driven threat models within sprint cycles to identify risks early, enabling developers to fix vulnerabilities before deployment.
This integration reduces bottlenecks and fosters a security-first mindset across teams.
Proactive Risk Management for Cloud Architectures
Architects use AI to continuously assess complex cloud environments, detecting misconfigurations and potential attack surfaces.
This proactive approach minimizes exposure and supports compliance with industry standards.
Streamlined Compliance and Audit Preparedness
Compliance officers employ AI-generated threat models to document security controls and risk mitigation strategies.
This accelerates audit cycles and simplifies reporting by maintaining up-to-date, verifiable models.