AI Cybersecurity Strategies
Top AI Prompts for Cybersecurity Policies
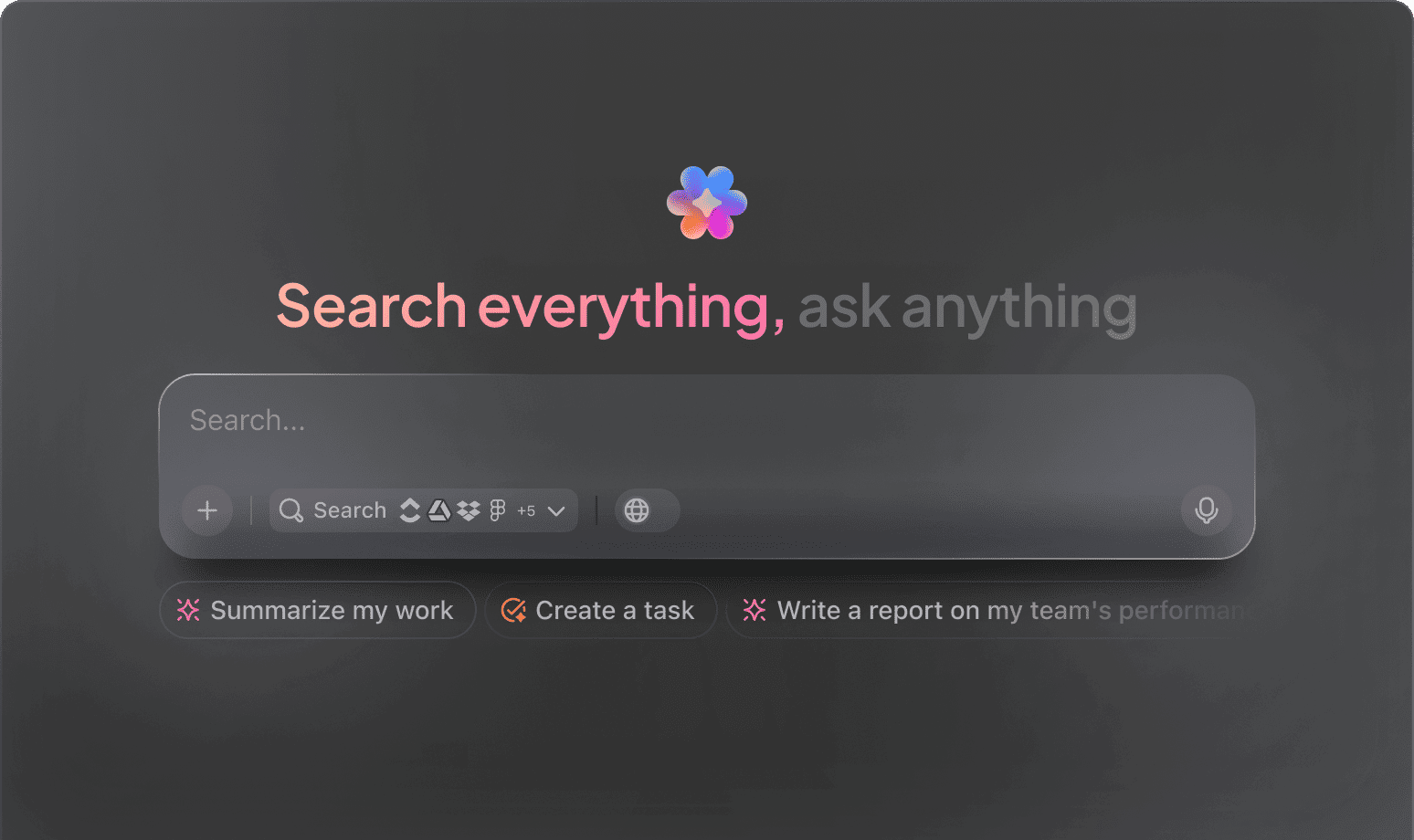
Develop robust security protocols, simplify policy management, and strengthen your organization's defenses with ClickUp AI.
Trusted by the world’s leading businesses
AI Empowering Cybersecurity Teams
Revolutionizing Cybersecurity Policy Development with AI Prompts
Crafting robust cybersecurity policies goes beyond setting rules—it’s about safeguarding your entire digital ecosystem.
From risk assessments to compliance audits and incident response planning, cybersecurity teams juggle numerous tasks alongside extensive documentation and tight deadlines. AI prompts are now pivotal in managing this complexity.
Security professionals leverage AI to:
- Quickly identify emerging threats and regulatory updates
- Generate policy drafts, risk matrices, and response protocols efficiently
- Digest lengthy compliance standards into clear summaries
- Transform scattered notes into structured action plans, checklists, or project tasks
Integrated within familiar tools—such as documents, whiteboards, and task managers—AI evolves from a simple helper to a strategic partner. In solutions like ClickUp Brain, it seamlessly converts your cybersecurity insights into organized, executable workflows.
Comparing ClickUp Brain with Conventional Solutions
Why ClickUp Brain Stands Out
ClickUp Brain integrates seamlessly, understands your context deeply, and empowers you to act swiftly—cutting down on needless explanations.
Conventional AI Platforms
- Constantly toggling between multiple apps to collect information
- Repeating your objectives with every new query
- Receiving generic, irrelevant suggestions
- Hunting through numerous platforms to locate a single document
- Interacting with AI that only processes input without insight
- Manually switching among different AI engines
- Merely an additional browser plugin
ClickUp Brain
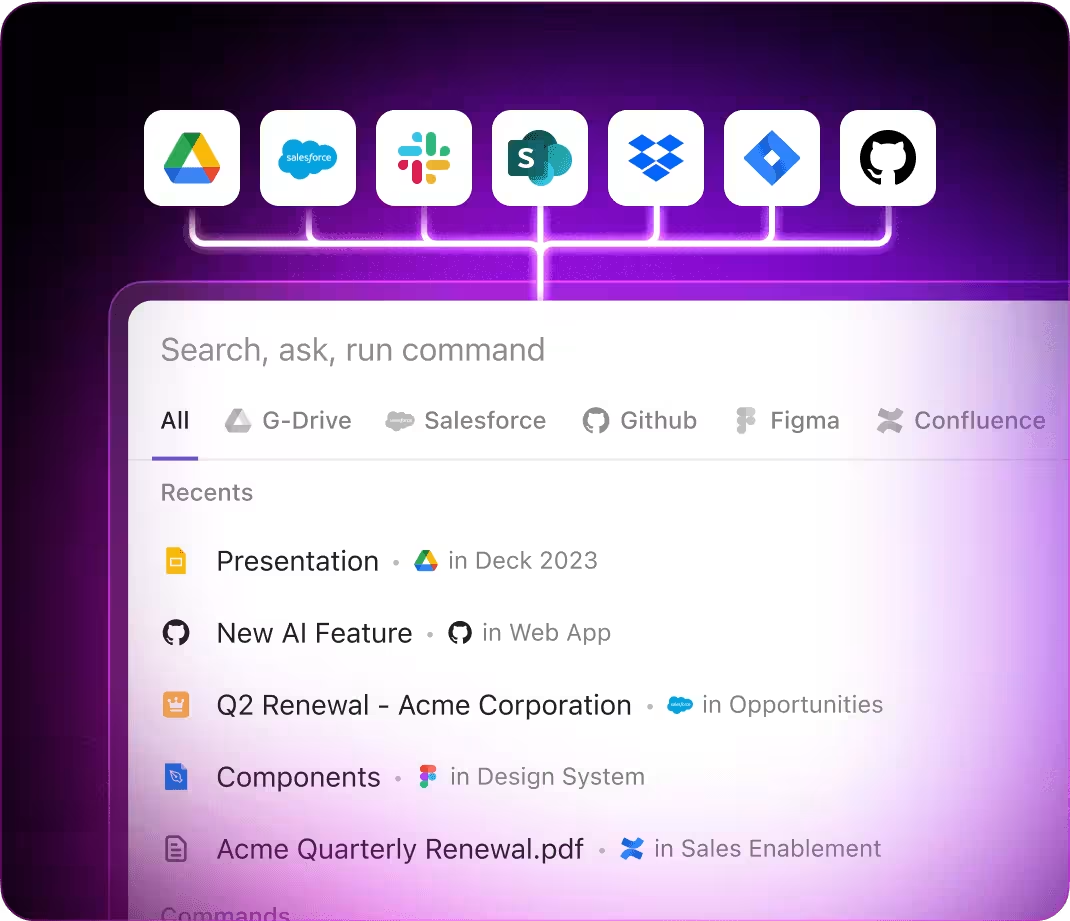
- Instantly accesses your cybersecurity tasks, policies, and team communications
- Retains your past interactions and strategic aims
- Provides detailed, context-aware recommendations
- Offers consolidated search across all your cybersecurity resources
- Supports hands-free operation with voice commands
- Automatically selects the optimal AI model: GPT, Claude, Gemini
- Available as a dedicated desktop app for Mac & Windows, optimized for performance
Cybersecurity Policy Prompts
15 Powerful AI Prompts for Cybersecurity Policies (Tested in ClickUp Brain)
Accelerate policy creation, compliance checks, and risk assessment with AI-driven insights.

Identify 5 emerging external cyber threats relevant to financial institutions, based on the ‘Threat Intelligence Q2’ report.
Use Case: Speeds up threat awareness by leveraging existing intelligence.
ClickUp Brain Behaviour: Extracts and summarizes key threat patterns from linked intelligence documents to inform policy focus.

What are the latest internal vulnerability patterns observed in healthcare IT systems under $1M budget?
Use Case: Supports risk prioritization with targeted vulnerability insights.
ClickUp Brain Behaviour: Aggregates findings from internal audit reports; Brain Max can supplement with public vulnerability databases if accessible.

Draft a policy brief for role-based access control inspired by NIST guidelines. Reference ‘Access Control Framework’ and prior compliance notes.
Use Case: Aligns security and compliance teams on access management standards.
ClickUp Brain Behaviour: Extracts relevant standards and notes from linked docs to generate a structured policy outline.

Summarize compliance gaps between HIPAA and GDPR using our ‘Compliance Audit 2024’ document.
Use Case: Facilitates comparative compliance analysis without manual review.
ClickUp Brain Behaviour: Extracts tabular and textual data from internal audits and produces a concise comparison.

List leading encryption protocols recommended for cloud data protection, referencing R&D and vendor specification documents.
Use Case: Guides selection of robust encryption methods.
ClickUp Brain Behavior: Scans internal documents to identify commonly cited encryption standards and their performance notes.

From the ‘Incident Response Plan’ doc, generate a detailed checklist for cyberattack mitigation steps.
Use Case: Streamlines incident handling with clear, actionable tasks.
ClickUp Brain Behavior: Extracts response criteria and formats them into a task checklist within a doc or project.

Summarize 3 emerging trends in multi-factor authentication from recent security research and technology reviews.
Use Case: Keeps authentication policies current and evidence-based.
ClickUp Brain Behavior: Identifies patterns and recurring themes from linked research materials.

From the ‘Employee Security Survey Q1’ doc, summarize key findings on phishing awareness and training effectiveness.
Use Case: Helps tailor training programs to address knowledge gaps.
ClickUp Brain Behavior: Analyzes survey data to highlight common feedback and training needs.

Write concise and approachable security alert copy for internal communications, using tone guidelines from ‘SecurityTone.pdf’.
Use Case: Accelerates creation of consistent, user-friendly alerts.
ClickUp Brain Behavior: Draws on tone references to suggest variations for alert messaging.

Summarize key changes in the 2025 cybersecurity regulations affecting financial services and their impact on policy updates.
Use Case: Ensures policies reflect the latest legal requirements.
ClickUp Brain Behavior: Extracts and condenses information from compliance documents; Brain Max can incorporate public updates if available.

Generate a checklist for data privacy compliance based on India’s Personal Data Protection Act, referencing internal legal documents.
Use Case: Supports regional compliance adherence.
ClickUp Brain Behavior: Extracts key provisions and compliance steps from internal references to form a task list.

Create a pre-audit checklist referencing US cybersecurity audit standards and our internal control documentation.
Use Case: Helps audit teams prepare efficiently and thoroughly.
ClickUp Brain Behavior: Identifies requirements from PDFs and internal docs, organizing tasks by audit area.

Compare sustainable cybersecurity practices like energy-efficient data centers across leading firms using competitive analysis documents.
Use Case: Supports innovation in eco-conscious security strategies.
ClickUp Brain Behavior: Summarizes comparative data into clear, actionable insights.

What new security challenges have arisen in IoT devices since 2023?
Use Case: Provides R&D teams with forward-looking threat intelligence.
ClickUp Brain Behavior: Synthesizes trends from internal research, threat reports, and uploaded studies.

Summarize key cybersecurity concerns from Southeast Asia client feedback (incident types, response times, policy gaps).
Use Case: Drives region-specific policy improvements.
ClickUp Brain Behavior: Extracts and prioritizes user-reported issues from surveys, support tickets, and feedback notes.
Craft Cybersecurity Policies Efficiently with ClickUp Brain
Avoid redundant efforts, unify your security team, and produce superior policy documents through AI-enhanced processes.


AI Applications
Leading AI Applications in Cybersecurity Policy Development
Enhance policy precision, reduce risks, and empower your security team with AI-driven insights
From Drafts to Cybersecurity Policies
Initial policy drafts can be fragmented and unclear. ClickUp Brain organizes these into clear, actionable cybersecurity documents— all within ClickUp Docs.
Leverage ClickUp Brain to:
- Convert preliminary notes into comprehensive policy templates
- Produce policy suggestions informed by previous security protocols (using context-sensitive AI writing)
- With Brain Max, instantly access historical security policies, audit feedback, and compliance records to inform your next update.
Cybersecurity Policy Development
Security teams manage extensive documentation and compliance requirements. ClickUp Brain empowers you to pinpoint critical action points, identify vulnerabilities, and create policy updates directly from your notes.
Leverage ClickUp Brain to:
- Condense lengthy security meeting transcripts into clear summaries
- Convert audit observations into prioritized remediation tasks
- Generate compliance reports or policy drafts effortlessly
- With Brain Max, instantly retrieve past incident analyses, regulation changes, or risk assessments throughout your workspace—eliminating tedious manual searches.
Cybersecurity Policy Development with ClickUp Brain
Crafting effective cybersecurity policies involves managing complex regulations, team inputs, and evolving threats. ClickUp Brain simplifies this process by extracting key points from discussions and drafting clear, compliant policy language.
Leverage ClickUp Brain to:
- Analyze meeting notes for critical security requirements
- Produce consistent policy documents tailored to your organization's tone
- Convert review comments into actionable revisions or compliance tasks
- Brain Max enhances this by referencing past policy versions and industry standards, supporting long-term governance and updates.
AI Advantages
How AI Prompts Revolutionize Cybersecurity Policy Management
Integrating AI prompt workflows reshapes how you handle cybersecurity policies:
- Accelerate policy drafting: Transform initial concepts into detailed guidelines and checklists swiftly
- Minimize errors: Detect gaps and conflicts by reviewing previous versions and audit notes
- Align your team: AI-crafted summaries and updates ensure everyone stays informed
- Make informed choices: Generate insights on compliance requirements and threat landscapes
- Strengthen defenses: Innovate policy frameworks that anticipate emerging risks.
Every output flows directly into ClickUp, turning AI-generated content into actionable documents, tasks, and dashboards that drive your security initiatives forward.
Prompting Strategies
How to Craft Effective Cybersecurity Policy Prompts
Clear prompts lead to precise policy guidance.

Specify the cybersecurity context
Broad prompts yield vague policies. Include details like industry sector (e.g., “financial services” or “healthcare”), compliance requirements (e.g., “HIPAA” or “GDPR”), or threat landscape (e.g., “phishing attacks” or “ransomware risks”).
Example: “Draft access control policies for a mid-sized healthcare provider handling patient data.”

Ask for side-by-side policy comparisons
AI excels at contrasting options. Use prompts like “compare X and Y” to assess different security measures, compliance frameworks, or incident response strategies.
Example: “Compare multi-factor authentication methods for remote workforce security.”

Focus on the task the policy must achieve
Think of your prompt as a clear security goal. Instead of vague requests, specify the desired outcome:
Example: “Create a data retention policy that balances regulatory compliance with minimal storage costs.”

Specify the format you need
Need a checklist, policy outline, risk matrix, or training plan? State it explicitly. AI delivers better when the output style is clear.
Example: “Provide a bullet-point list of key steps for incident response in a financial institution.”
Simplify Cybersecurity Policy Creation with ClickUp Brain
ClickUp Brain goes beyond basic task tracking—it’s your strategic partner in crafting robust cybersecurity policies efficiently.