AI Cybersecurity Solutions
Top AI Prompts for Cybersecurity Teams
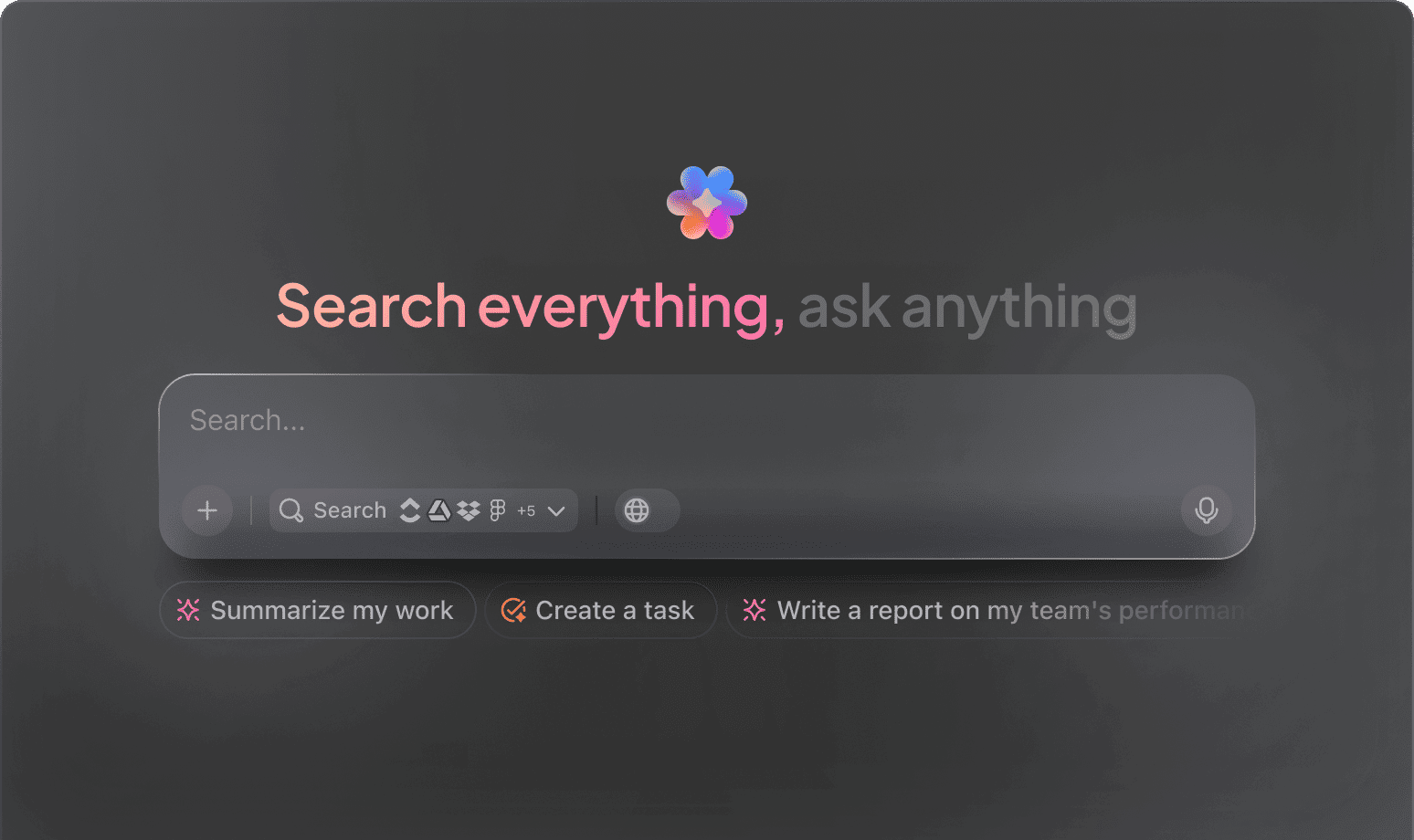
Detect threats faster, optimize your security operations, and strengthen defenses with ClickUp AI tailored for cybersecurity.
Trusted by the world’s leading businesses
AI Empowerment in Cybersecurity
Harnessing AI Prompts to Revolutionize Cybersecurity Operations
Protecting digital assets today demands more than reactive measures—it requires proactive, intelligent coordination.
From threat detection and vulnerability assessment to incident response and compliance management, cybersecurity teams juggle countless alerts, reports, and protocols. AI prompts are becoming indispensable in managing this complexity.
Security teams leverage AI to:
- Quickly identify emerging threat patterns and attack vectors
- Generate detailed incident reports and remediation plans with minimal effort
- Decode complex compliance requirements and audit documentation
- Transform fragmented logs and alerts into prioritized action items and workflows
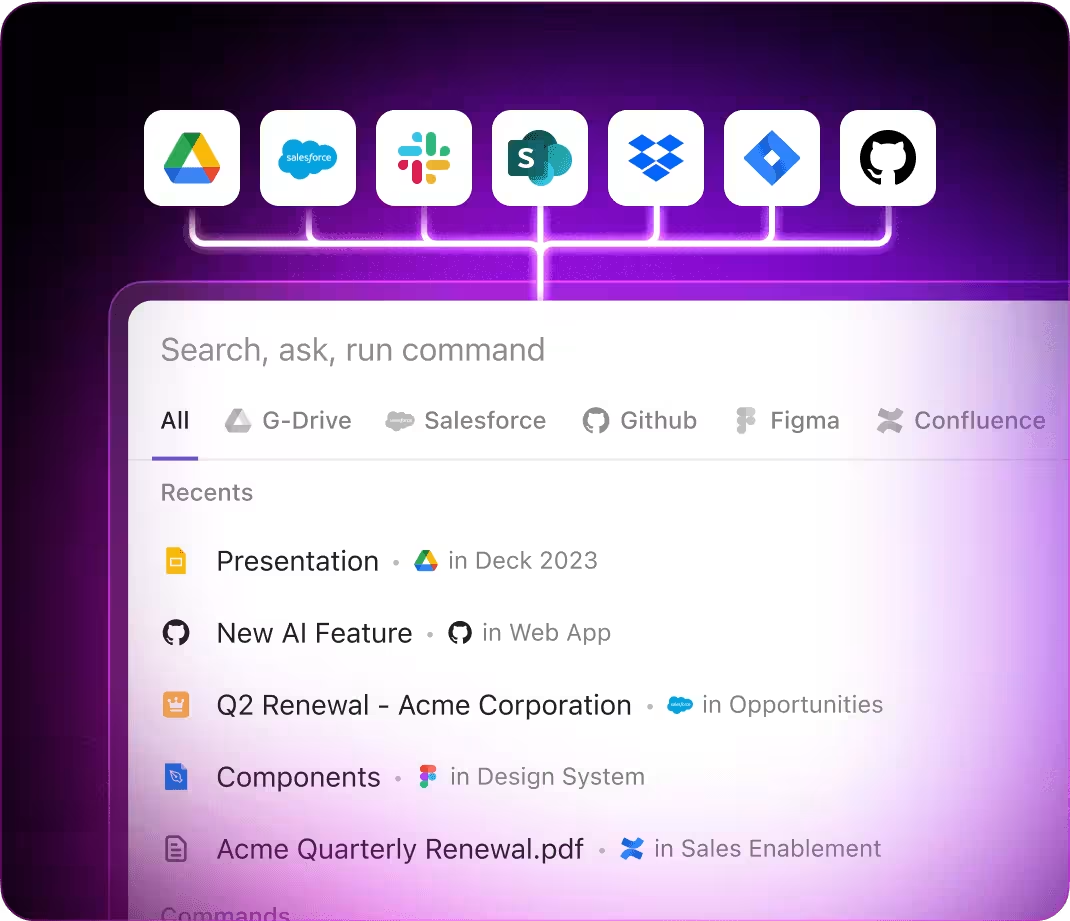
Integrated within familiar environments—such as documentation platforms, dashboards, and ticketing systems—AI evolves beyond a simple tool. In solutions like ClickUp Brain, it operates seamlessly to convert raw security data into structured, prioritized tasks that empower teams to respond faster and smarter.
ClickUp Brain Compared to Conventional Solutions
Discover How ClickUp Brain Elevates Cybersecurity Workflows
ClickUp Brain integrates seamlessly with your security operations, delivering insights without the usual hassle of setup or context sharing.
Conventional AI Platforms
- Constantly toggling between dashboards to collect data
- Reiterating security objectives with every query
- Receiving generic, irrelevant suggestions
- Hunting through multiple apps to locate incident reports
- Interacting with AI that lacks situational awareness
- Manually switching between different AI engines
- Merely an add-on extension in your browser
ClickUp Brain
- Deeply integrated with your security tasks, logs, and team communications
- Retains your investigation history and priorities
- Provides precise, context-driven recommendations
- Searches across all your cybersecurity tools in one place
- Supports voice commands with Talk to Text for hands-free operation
- Automatically selects the optimal AI model: GPT, Claude, Gemini
- Native applications for Mac & Windows designed for rapid response
Cybersecurity AI Prompts
15 Targeted AI Prompts for Cybersecurity Teams (Optimized with ClickUp Brain)
Enhance threat detection, incident response, and compliance management effortlessly.

Identify 5 emerging threat vectors targeting cloud infrastructure, based on the ‘Q2 Threat Analysis’ report.
Use Case: Accelerates threat landscape awareness using recent intelligence.
ClickUp Brain Behaviour: Analyzes linked reports to extract and summarize key attack patterns and vectors.

What are the latest compliance requirements for GDPR and CCPA impacting data handling in cybersecurity?
Use Case: Supports legal and security teams in maintaining up-to-date regulatory adherence.
ClickUp Brain Behaviour: Synthesizes compliance documents and regulatory updates; Brain Max can supplement with public legal sources if available.

Draft a security incident response plan outline referencing ‘Incident Response Guidelines’ and past breach reports.
Use Case: Ensures aligned and structured response protocols across teams.
ClickUp Brain Behaviour: Extracts critical steps and recommendations from linked documents to create a clear, actionable plan.

Summarize vulnerability assessment results comparing internal scans and third-party reports from the ‘Vuln Scan Q1’ folder.
Use Case: Facilitates quick understanding of risk exposure without manual data review.
ClickUp Brain Behaviour: Compiles tabular and textual data into a concise comparative summary.

List top encryption algorithms recommended for securing IoT devices, referencing R&D notes and industry standards.
Use Case: Guides selection of robust cryptographic methods for device security.
ClickUp Brain Behavior: Extracts and ranks algorithms from internal documents based on performance and adoption.

From the ‘Penetration Testing Checklist’ doc, generate a task list for upcoming security audits.
Use Case: Simplifies audit preparation with a ready-to-use checklist.
ClickUp Brain Behavior: Identifies key audit points and formats them into actionable tasks or checklist items.

Summarize 3 recent phishing attack trends targeting financial institutions from post-2023 threat intelligence reports.
Use Case: Keeps defense strategies current and evidence-based.
ClickUp Brain Behavior: Extracts recurring tactics and indicators from linked intelligence documents.

From the ‘User Access Survey Q1’ doc, summarize key preferences and pain points regarding multi-factor authentication.
Use Case: Helps security teams tailor authentication methods to user needs.
ClickUp Brain Behavior: Reads survey data to identify common themes and user feedback patterns.

Write clear and concise alert messages for ransomware detection systems using the tone guide in ‘SecurityTone.pdf’.
Use Case: Accelerates creation of user-friendly notifications with consistent voice.
ClickUp Brain Behavior: Draws on tone references to propose varied alert copy options.

Summarize key updates in the NIST 2024 cybersecurity framework and their implications for network security.
Use Case: Informs teams about compliance and best practice adjustments.
ClickUp Brain Behavior: Condenses linked framework documents; Brain Max can incorporate public updates if available.

Generate configuration guidelines for firewall rules based on regional compliance documents stored in our workspace.
Use Case: Ensures firewall settings meet local regulatory standards.
ClickUp Brain Behavior: Extracts rule sets and compliance notes to form a detailed configuration checklist.

Create a checklist for endpoint security validation using US Cybersecurity and Infrastructure Security Agency (CISA) recommendations and internal policy docs.
Use Case: Supports QA teams in verifying endpoint protection measures.
ClickUp Brain Behavior: Identifies requirements from documents and organizes tasks by security category.

Compare threat detection capabilities across leading SIEM platforms using our competitive analysis reports.
Use Case: Aids security architects in selecting optimal monitoring solutions.
ClickUp Brain Behavior: Summarizes documented feature comparisons into a clear, digestible format.

What are the emerging cybersecurity challenges in IoT device management since 2023?
Use Case: Provides R&D teams with insights to guide secure product development.
ClickUp Brain Behavior: Synthesizes trends from internal research notes, incident reports, and industry analyses.

Summarize key user-reported issues from the Asia-Pacific cybersecurity feedback folder (incident response times, threat detection accuracy).
Use Case: Drives targeted improvements based on regional user experiences.
ClickUp Brain Behavior: Extracts and prioritizes feedback from surveys, support tickets, and incident logs.
Elevate Cybersecurity Strategy with ClickUp Brain
Cut down on redundant tasks, unify your security team, and produce stronger defenses through AI-driven workflows.


AI Applications
Leading 3 Applications of AI Prompts in Cybersecurity Operations
Enhance threat detection, boost response precision, and uncover innovative defenses with AI-driven insights
From Incident Notes to Security Protocols
Initial security observations usually come as fragmented logs and unorganized alerts. ClickUp Brain organizes these into clear, actionable security protocols—right within ClickUp Docs.
Leverage ClickUp Brain to:
- Convert raw incident details into standardized response templates
- Develop fresh defense strategies informed by previous threat data (using context-aware AI assistance)
- With Brain Max, instantly explore historical breach reports, analyst feedback, and threat intelligence to enhance your next security plan.
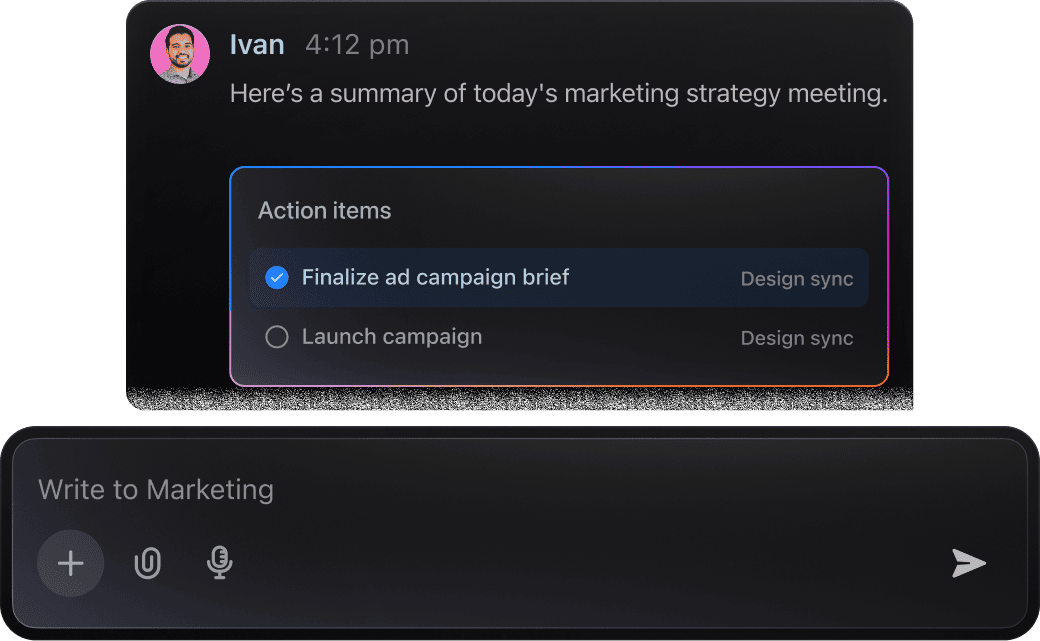
From Design to Development
Development teams handle complex project details and feedback constantly. ClickUp Brain empowers you to pinpoint key tasks, identify risks early, and create clear next steps from your project documentation.
Leverage ClickUp Brain to:
- Condense detailed technical conversations within tasks or Docs
- Convert annotated design feedback into actionable development tickets
- Automatically generate bug reports or transition summaries
- With Brain Max, instantly retrieve past design choices, component evaluations, or build discussions across your workspace—eliminating tedious searches through engineering files.
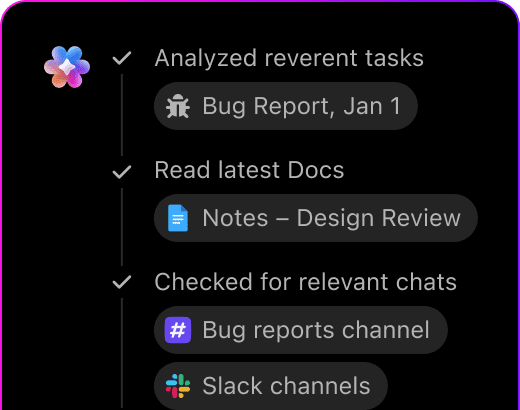
Cybersecurity AI Prompts Powered by ClickUp Brain
Managing cybersecurity projects involves coordinating threat analyses, incident reports, and compliance checks. ClickUp Brain simplifies this complexity—extracting key findings and crafting precise security communications that align with your protocols.
Leverage ClickUp Brain to:
- Analyze security logs and highlight critical vulnerabilities
- Produce clear, consistent alerts and policy updates across platforms
- Convert investigation notes into prioritized remediation tasks
- Brain Max enhances this by retrieving relevant past incident data or compliance records, supporting long-term security strategies.
AI Advantages
Why AI Prompts Are Revolutionizing Cybersecurity Operations
Integrating AI prompt workflows enhances every phase of your cybersecurity strategy:
- Accelerate threat detection: Quickly generate hypotheses and scenarios to identify vulnerabilities
- Reduce false alarms: Analyze historical incident data to filter noise and focus on real threats
- Unify your defense team: AI-crafted reports and summaries ensure everyone stays informed and aligned
- Make informed decisions: Use prompts to gather actionable intelligence and compliance updates
- Anticipate attacks: Develop proactive measures that go beyond standard security protocols.
All these capabilities integrate directly within ClickUp, turning your AI-generated insights into actionable tasks, detailed documents, and comprehensive dashboards that drive your security initiatives forward.
Prompt Guidance
How to Craft Effective Cybersecurity Prompts
Clear prompts lead to stronger security strategies.

Define the cybersecurity scenario clearly
Vague prompts produce generic advice. Specify details like threat type (e.g., “phishing attack” or “ransomware incident”), security objective (e.g., “incident response” or “vulnerability assessment”), or organizational context (e.g., “small business network” or “enterprise cloud environment”).
Example: “Outline detection methods for spear-phishing attempts targeting financial departments.”

Use comparative prompts to evaluate defenses
AI excels at contrasting different security measures. Use prompts like “compare X versus Y” to assess firewall technologies, encryption standards, or response strategies.
Example: “Compare endpoint protection capabilities of CrowdStrike and SentinelOne.”

Position prompts around security tasks
Frame your prompt as a specific cybersecurity action you want AI to assist with. Instead of “Suggest security policies,” focus on outcomes:
Example: “Develop a step-by-step plan for mitigating insider threat risks in a mid-sized enterprise.”

Specify desired output formats
Need a risk matrix, incident report template, checklist, or training outline? Be explicit. AI delivers better when output expectations are clear.
Example: “Provide a bullet-point list of top 5 network hardening techniques with brief explanations.”
Enhance Cybersecurity Strategies with ClickUp Brain
ClickUp Brain goes beyond simple task tracking—it's your strategic partner in fortifying every layer of your cybersecurity operations.