AI Cybersecurity Policy Crafting
Top AI Prompts for Cybersecurity Policies
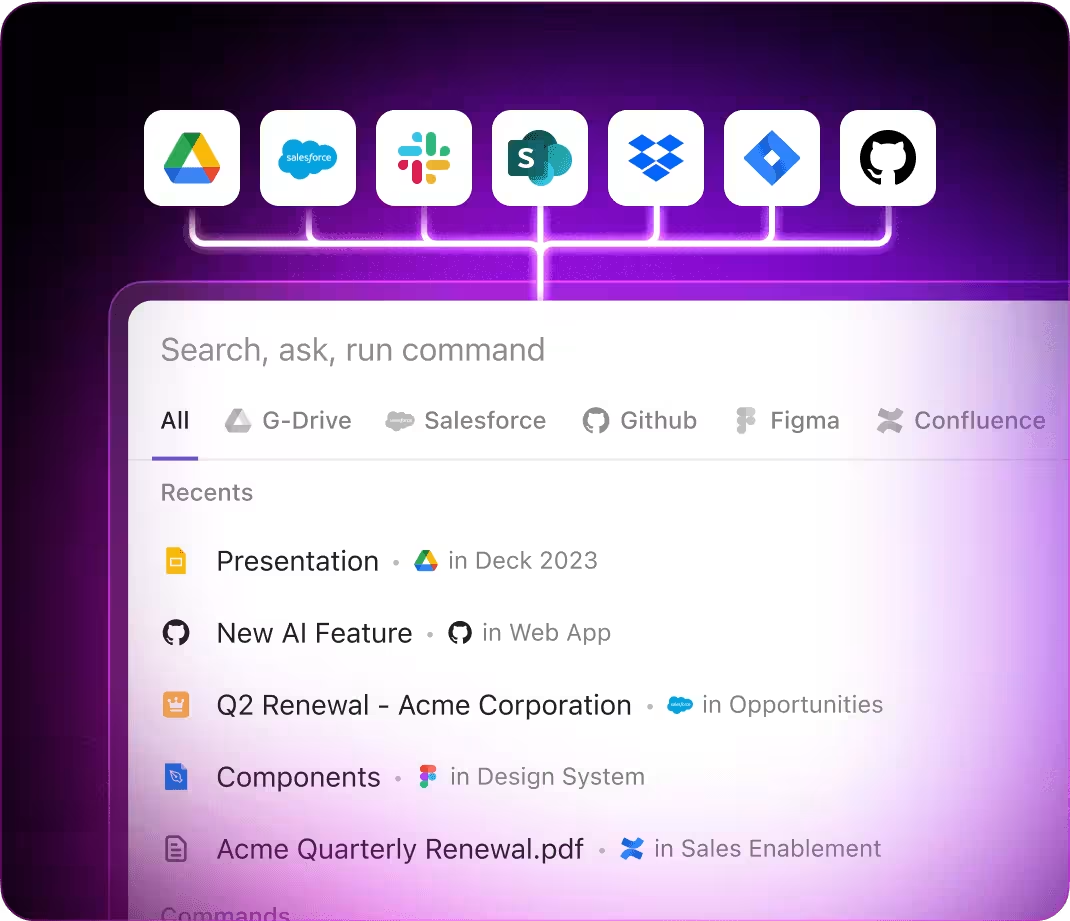
Develop robust security protocols, simplify policy management, and safeguard your organization efficiently with ClickUp Brain.
Trusted by the world’s leading businesses
AI in Cybersecurity Policy
AI Prompts Revolutionizing Cybersecurity Policy Creation
Crafting robust cybersecurity policies goes beyond setting rules—it's about safeguarding your entire digital environment.
From risk assessment and compliance audits to incident response planning and employee training, cybersecurity teams juggle numerous tasks, documents, and protocols. AI prompts are now indispensable in managing this complexity.
Security teams leverage AI to:
- Quickly identify emerging threats and regulatory updates
- Generate policy drafts and response procedures with minimal effort
- Distill lengthy compliance documents into clear summaries
- Transform scattered notes into structured guidelines, checklists, or action items
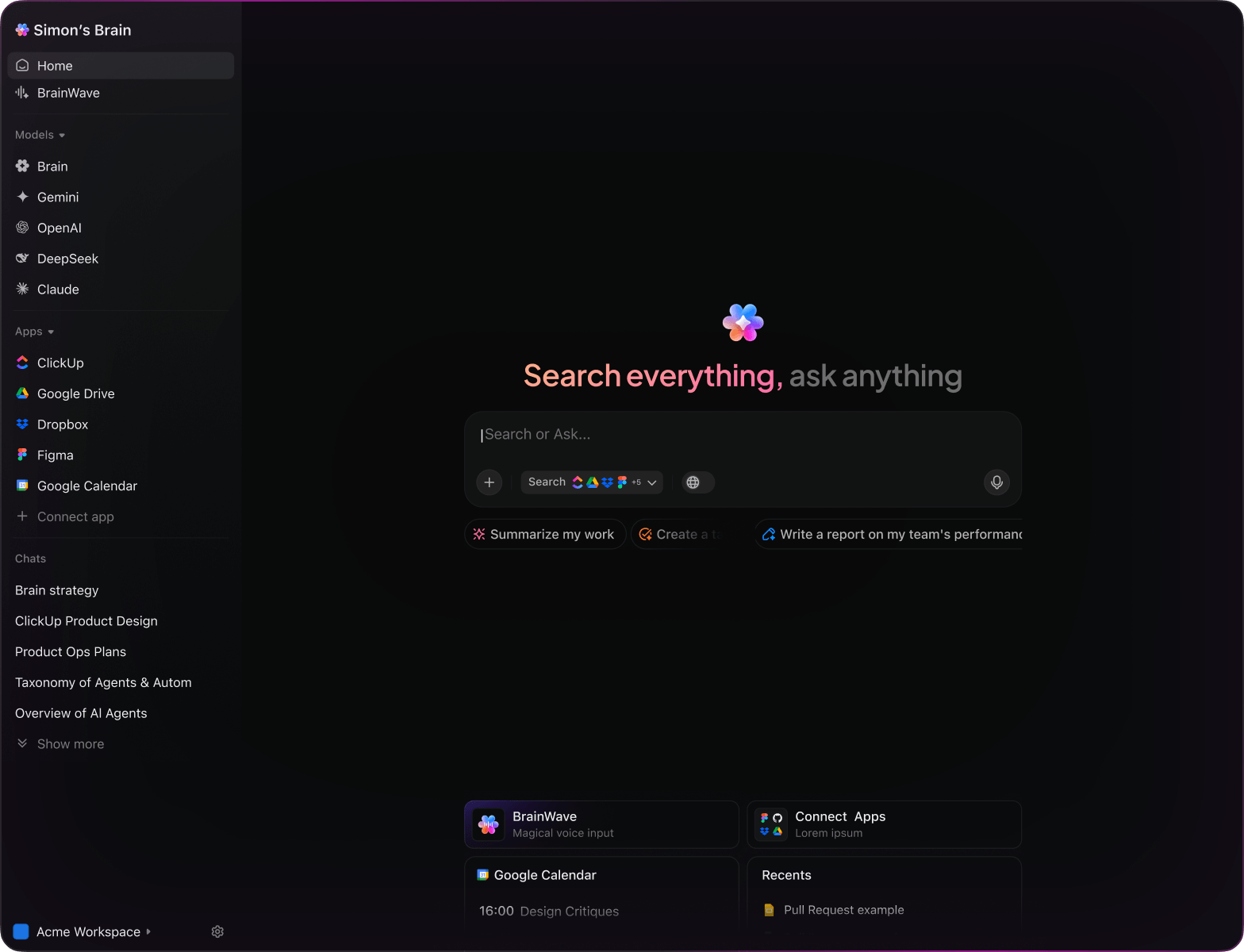
Integrated within familiar tools—such as documents, whiteboards, and task trackers—AI in platforms like ClickUp Brain acts as a proactive partner, converting your security insights into clear, executable plans.
ClickUp Brain vs Conventional Solutions
Why ClickUp Brain Stands Out
ClickUp Brain integrates seamlessly, understands your context deeply, and acts swiftly—letting you focus on securing your systems, not explaining them.
Standard AI Platforms
- Constantly toggling between apps to collect info
- Repeating your cybersecurity objectives with every query
- Receiving generic, irrelevant suggestions
- Hunting through multiple platforms to locate a single policy
- Engaging with AI that only processes input without insight
- Manually switching among GPT variants and other services
- Merely a browser add-on without integration
ClickUp Brain
- Instantly accesses your security tasks, documents, and team communications
- Retains your project history and compliance goals
- Provides precise, context-driven recommendations
- Searches all your cybersecurity resources in one place
- Supports voice commands with Talk to Text
- Automatically selects the optimal AI model: GPT, Claude, Gemini
- Dedicated Mac & Windows app optimized for performance
Cybersecurity Policy Prompts
15 Essential AI Prompts for Cybersecurity Policies
Enhance your security protocols—policy drafting, compliance checks, and risk assessment simplified.

Identify 5 key policy approaches for securing remote work environments based on the ‘Remote Access Guidelines 2024’ document.
ClickUp Brain Behaviour: Analyzes the linked document to extract strategic policy recommendations tailored for remote workforce security.

What are the latest compliance requirements for data privacy in healthcare organizations under HIPAA?
ClickUp Brain Behavior: Gathers and synthesizes relevant regulatory updates from internal compliance files; Brain Max can incorporate external authoritative sources if accessible.

Draft a cybersecurity incident response plan outline inspired by the ‘Incident Response Framework’ and recent breach case studies.
ClickUp Brain Behavior: Pulls critical elements and best practices from linked documents to construct a structured response plan template.

Summarize vulnerability management strategies comparing OWASP Top 10 and NIST guidelines using our ‘Vulnerability Assessment Q1’ report.
ClickUp Brain Behavior: Extracts and contrasts key points from internal reports to deliver a concise comparative summary.

List top encryption standards recommended for cloud data protection, referencing R&D notes and vendor specifications.
ClickUp Brain Behavior: Reviews internal documents to highlight prevalent encryption protocols and their performance characteristics.

From the ‘Access Control Policy Review’ doc, generate a checklist for user privilege audits.
ClickUp Brain Behavior: Identifies audit criteria and transforms them into an actionable checklist within a task or document.

Summarize 3 emerging trends in threat detection technologies from recent cybersecurity research and whitepapers.
ClickUp Brain Behavior: Extracts recurring themes and innovations from linked research materials and reports.

From the ‘Employee Security Awareness Survey 2024’ doc, summarize key training needs and common vulnerabilities.
ClickUp Brain Behavior: Analyzes survey data to identify prevalent knowledge gaps and risk areas among staff.

Write clear and engaging user guidelines for multi-factor authentication setup using the tone outlined in ‘SecurityTone.pdf’.
ClickUp Brain Behavior: Adapts style references from the document to create approachable and concise instructional copy.

Summarize upcoming changes in GDPR enforcement for 2025 and their implications for data handling policies.
ClickUp Brain Behavior: Reviews linked compliance updates and forecasts to provide a digestible overview of regulatory shifts.

Generate placement and formatting standards for security notices on internal portals, referencing company branding and compliance guidelines.
ClickUp Brain Behavior: Extracts layout rules and compliance requirements from internal documents to form a standards checklist.

Create a checklist for penetration testing phases using the latest industry standards and our recent test reports.
ClickUp Brain Behavior: Identifies key testing stages and criteria from readable documents and organizes them into grouped tasks.

Compare data retention policies across financial institutions using our competitive analysis files.
ClickUp Brain Behavior: Summarizes documented policy differences into a clear, comparative format (table or brief).

What cybersecurity policy trends are emerging for IoT devices since 2023?
ClickUp Brain Behavior: Synthesizes insights from internal research notes, industry reports, and regulatory updates.

Summarize key policy gaps identified from recent internal audits focusing on access controls and incident reporting.
ClickUp Brain Behavior: Extracts and prioritizes findings from audit reports, feedback logs, and tagged compliance tickets.
Accelerate Cybersecurity Policy Creation with ClickUp Brain
Cut down revisions, unify your security team, and produce superior policies using AI-driven workflows.


AI Prompts Tailored for Cybersecurity Policies with ClickUp Brain
Discover How ChatGPT, Gemini, Perplexity, and ClickUp Brain Enhance Cybersecurity Policy Development
ChatGPT Cybersecurity Prompts
- Outline a 5-point summary of cybersecurity policy drafts focusing on data protection and compliance.
- Compose an internal memo promoting new access control measures emphasizing user accountability and security.
- Generate 3 alternative incident response strategies highlighting rapid containment and recovery.
- Draft a detailed workflow for implementing multi-factor authentication across departments.
- Compare recent audit reports and summarize key vulnerabilities to address in upcoming policy revisions.
Gemini Security Policy Prompts
- Propose 3 variations of network security protocols based on recent threat assessments.
- List innovative encryption techniques suitable for cloud data protection emphasizing usability.
- Create a descriptive overview of a zero-trust architecture framework highlighting components and benefits.
- Suggest user training program layouts focusing on phishing awareness and rank by effectiveness.
- Develop a comparison chart of endpoint security solutions prioritizing scalability and ease of management.
Perplexity Cybersecurity Insights
- Identify 5 emerging cybersecurity threats and evaluate their potential impact on enterprise systems.
- Compare authentication technologies for remote access, emphasizing security and user convenience.
- Summarize global regulations affecting data privacy and their implications for policy updates.
- List 5 best practices for secure software development and rank them by adoption difficulty.
- Analyze past breach case studies and extract 3 critical lessons for strengthening defenses.
ClickUp Brain Cybersecurity Prompts
- Transform this security incident report into prioritized remediation tasks with assigned owners.
- Summarize compliance audit findings and generate follow-up actions with deadlines in ClickUp.
- Review annotated network diagrams and create a checklist of configuration changes needed.
- Compile tasks from cross-department discussions on policy updates, including urgency and responsible teams.
- Extract key points from penetration test results and generate actionable tasks for IT and security teams.
Why ClickUp Works
From Initial Thoughts to Clear Cybersecurity Plans
- Transform scattered notes into detailed policy drafts swiftly.
- Generate innovative strategies by analyzing previous security protocols.
- Build standardized templates that accelerate policy development.
Brain Max Boost: Quickly access historical policies, audit results, and compliance documents to guide your next cybersecurity framework.
Why Choose ClickUp
Accelerate Cybersecurity Policy Development
- Break down intricate security requirements into manageable tasks.
- Transform policy drafts into actionable assignments effortlessly.
- Automatically compile compliance reports and policy summaries without extra effort.
Brain Max Boost: Instantly access historical policy versions, risk assessments, or regulatory references across your security projects.
AI Advantages
How AI Prompts Elevate Every Phase of Cybersecurity Policy Creation
AI prompts accelerate strategy development and empower more resilient, compliant security policies.
Craft Robust Policies Quickly
Security teams draft comprehensive policies faster, enhance decision-making, and prevent analysis paralysis.
Enhance Compliance and Risk Management
Make informed choices that reduce vulnerabilities and satisfy regulatory standards effectively.
Identify Gaps Before They Become Issues
Minimize costly policy revisions, improve security posture, and speed up implementation timelines.
Align Teams Around Clear Security Goals
Fosters collaboration, removes misunderstandings, and accelerates consensus among IT, legal, and management.
Drive Forward-Thinking Security Strategies
Inspire innovative approaches, anticipate emerging threats, and maintain a competitive defense edge.
Integrated AI Assistance Within ClickUp
Transforms AI insights into actionable tasks that keep your cybersecurity initiatives progressing smoothly.
Speed Up Your Cybersecurity Policy Creation
Minimize mistakes, simplify collaboration, and generate precise policies with AI support.