AI Security Policy Management
Top AI Prompts for Security Policy Implementation
Develop robust security policies, simplify compliance tasks, and enhance your organization's protection strategy with ClickUp AI.
Trusted by the world’s leading businesses
AI in Security Management
AI Prompts Revolutionizing Security Policy Deployment
Crafting robust security policies goes beyond writing rules—it's about orchestrating consistent, compliant actions across your organization.
From risk assessment to policy drafting, employee training, and audit tracking, security policy implementation involves numerous steps and stakeholders. AI prompts are now pivotal in streamlining these complex workflows.
Security teams leverage AI to:
- Quickly identify relevant compliance standards and best practices
- Generate clear, actionable policy drafts from minimal guidance
- Break down dense regulatory language into understandable summaries
- Transform scattered feedback into structured action plans and task lists
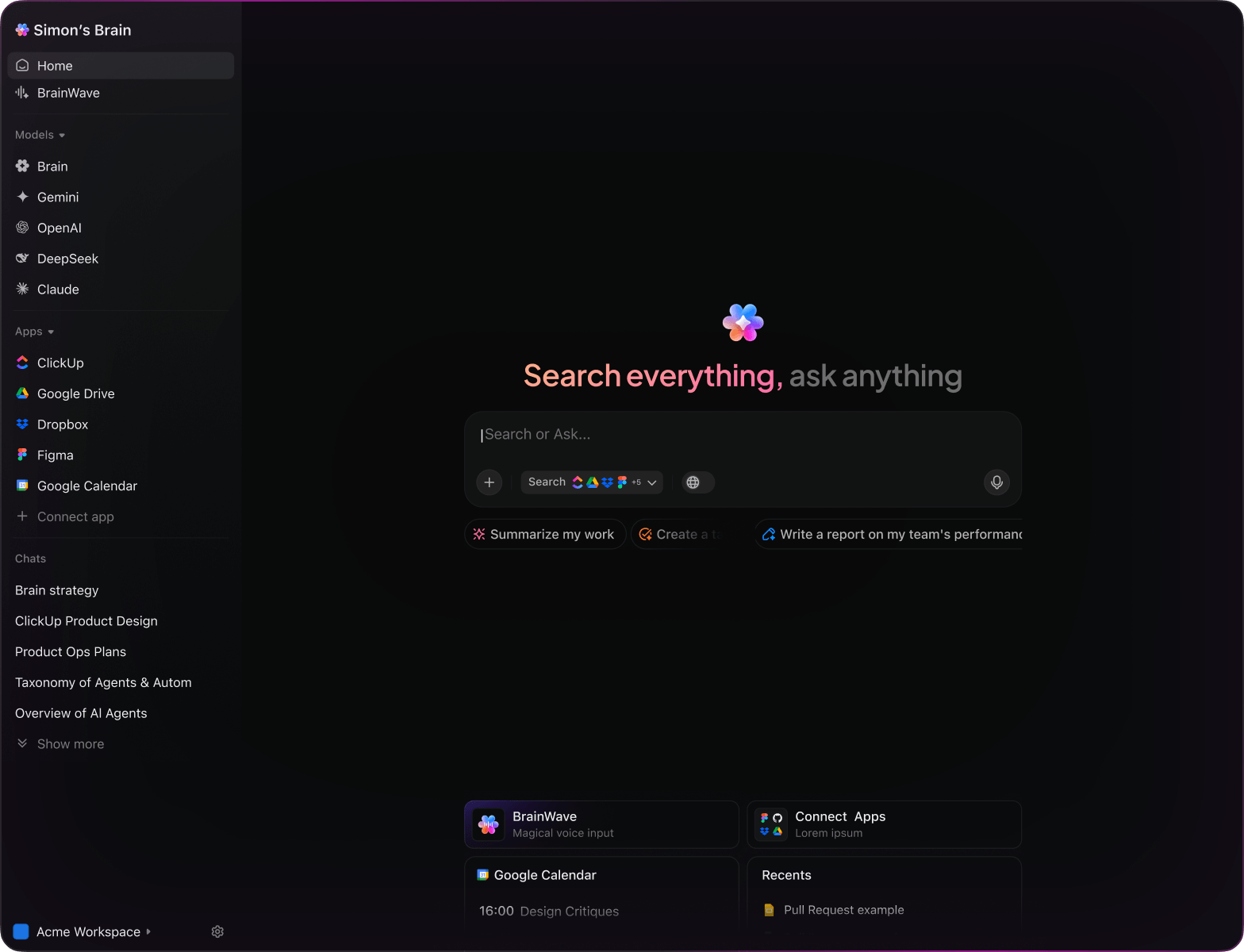
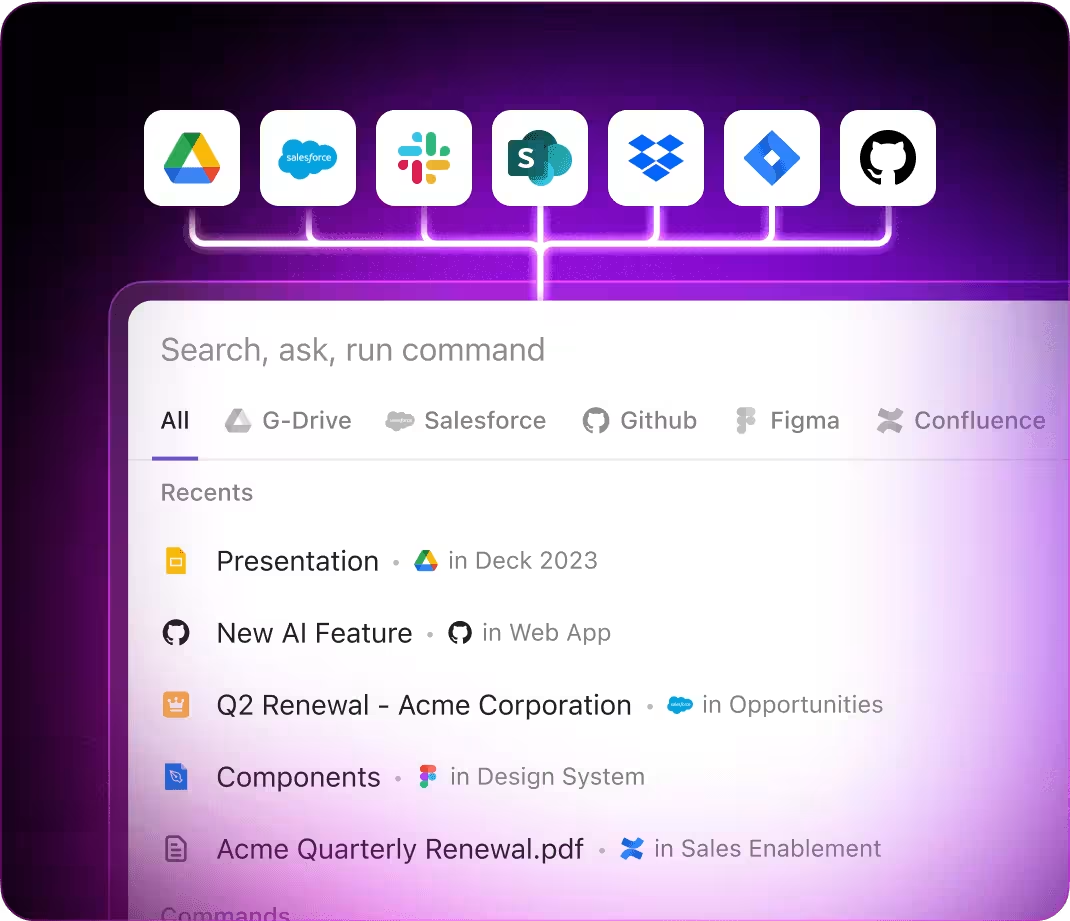
Integrated within familiar tools like documents, dashboards, and project boards, AI in ClickUp Brain acts as a proactive partner—translating security insights into coordinated, manageable tasks.
ClickUp Brain Compared to Other Platforms
Why ClickUp Brain Stands Out
ClickUp Brain integrates seamlessly with your workflow, understanding your context so you can focus on action, not explanation.
Conventional AI Solutions
- Constantly switching apps to collect information
- Repeating your objectives with every query
- Responses that lack relevance to your situation
- Hunting through multiple platforms to locate a document
- Interacting with AI that only processes input
- Manually toggling between different AI engines
- Merely an add-on in your browser
ClickUp Brain
- Deeply connected to your projects, documents, and team activity
- Retains your previous interactions and objectives
- Provides insightful, context-driven guidance
- Single search access across all your resources
- Supports voice commands with Talk to Text
- Automatically selects the optimal AI model: GPT, Claude, Gemini
- Dedicated Mac & Windows app designed for performance
Security Policy Implementation Prompts
15 Essential AI Prompts for Security Policy Execution
Simplify security policy rollout—planning, compliance checks, and team alignment made straightforward.

Identify 5 security policy frameworks suitable for a mid-sized technology company, referencing the ‘Security Standards 2024’ document.
ClickUp Brain Behavior: Analyzes the linked document to extract and recommend relevant security frameworks tailored to the company’s profile.

What are the latest access control and authentication trends in financial institutions under $100M revenue?
ClickUp Brain Behavior: Gathers insights from internal reports; Brain Max can supplement with external industry data when available.

Compose a security policy brief focused on remote work best practices, using notes from ‘Remote Security Guidelines’ and previous policy drafts.
ClickUp Brain Behavior: Extracts key points and structures them into a clear, actionable policy document.

Summarize encryption protocols used across recent security audits, referencing ‘Encryption Audit Q1’ report.
ClickUp Brain Behavior: Pulls data from audit reports and presents a concise comparison of encryption standards and their effectiveness.

Identify leading endpoint security solutions mentioned in R&D and vendor evaluation documents.
ClickUp Brain Behavior: Scans internal files to list frequently recommended tools along with performance notes.

From the ‘Phishing Test Procedures’ document, create a detailed checklist for conducting phishing simulations.
ClickUp Brain Behavior: Extracts test steps and criteria, formatting them into a task-ready checklist.

Outline three new developments in user authentication methods based on post-2023 research and technology reviews.
ClickUp Brain Behavior: Identifies patterns and innovations from linked research documents.

From the ‘Employee Security Survey Q2’ document, summarize key feedback themes regarding training effectiveness.
ClickUp Brain Behavior: Reviews survey data to highlight common opinions and suggestions.

Craft brief, engaging security reminder messages for login interfaces, following the tone in ‘SecurityToneGuide.pdf’.
ClickUp Brain Behavior: Uses tone guidelines to generate varied message options suitable for user prompts.

Outline major changes in data privacy laws effective in 2025 and their implications for policy updates.
ClickUp Brain Behavior: Condenses regulatory documents and highlights compliance requirements.

Develop placement and formatting rules for password policy notices, referencing compliance documents specific to the EU.
ClickUp Brain Behavior: Extracts regulatory standards and compiles them into clear guidelines.

Using US cybersecurity frameworks and internal incident logs, generate a comprehensive readiness checklist.
ClickUp Brain Behavior: Identifies critical response steps and organizes them by priority and category.

Analyze encryption techniques used by key competitors based on internal competitive intelligence reports.
ClickUp Brain Behavior: Summarizes comparative findings into an accessible format for strategic review.

Highlight emerging cloud security practices and challenges noted in recent internal studies and external reports.
ClickUp Brain Behavior: Synthesizes data from multiple sources to reveal current trends.

Extract and prioritize security concerns reported by users in the Asia-Pacific region from feedback and support tickets.
ClickUp Brain Behavior: Aggregates and ranks issues to inform policy adjustments and training focus.
Accelerate Security Policy Deployment with ClickUp Brain
Cut down on redundant tasks, unify your security team, and produce superior policy frameworks using AI-driven processes.


AI Prompts for Security Policy Implementation using ClickUp Brain
Discover How ClickUp Brain Enhances Security Policy Workflows Compared to Other AI Tools
Prompts for ChatGPT
- Outline a 5-point summary of the current security policy draft focusing on compliance and risk mitigation.
- Compose an internal memo highlighting key updates in data protection protocols.
- Propose 3 alternative access control models for sensitive data environments and explain their benefits.
- Develop a stepwise plan for rolling out multi-factor authentication across departments.
- Compare recent audit reports and extract the top compliance gaps to address in the next policy revision.
Prompts for Gemini
- Design 3 different incident response workflows tailored for phishing, malware, and insider threats.
- Suggest innovative employee training topics to improve awareness of cybersecurity best practices.
- Create a visual concept for a security dashboard emphasizing real-time threat monitoring.
- Recommend ergonomic layouts for secure workstation setups minimizing data exposure risks.
- Build a comparison chart of encryption standards focusing on strength, performance, and regulatory compliance.
Prompts for Perplexity
- List 5 emerging cybersecurity frameworks and evaluate their applicability for mid-sized enterprises.
- Provide a detailed comparison of VPN technologies, highlighting security features and user experience.
- Summarize global trends in data breach incidents and their impact on regulatory policies.
- Generate a list of 5 practical data retention strategies and rank them by compliance effectiveness.
- Analyze past security policy failures and extract 3 key lessons for future implementations.
Prompts for ClickUp Brain
- Transform this security audit feedback into prioritized remediation tasks with assigned owners.
- Summarize compliance meeting notes and create follow-up action items with deadlines.
- Review annotated network diagrams and generate a checklist of vulnerabilities needing immediate attention.
- Compile a task list from cross-department discussions on access control enhancements, including urgency levels.
- Summarize penetration test reports and produce actionable bug fixes and policy updates within ClickUp.
Why ClickUp Works
Transform Initial Thoughts into Clear Plans
- Convert scattered notes into polished security policies swiftly.
- Generate innovative strategies by analyzing previous compliance efforts.
- Build adaptable templates that accelerate policy rollouts.
Brain Max Boost: Quickly access historical audit reports, team feedback, and security documents to guide your policy development.
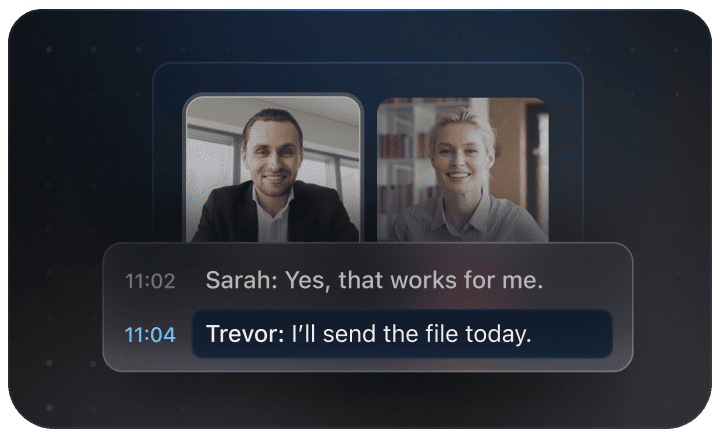
Why ClickUp Works
Accelerate Security Policy Deployment
- Break down intricate security talks into straightforward tasks.
- Transform policy drafts into actionable assignments.
- Automatically create compliance reports and rollout summaries—no extra effort.
Brain Max Boost: Instantly access historical policy versions, risk assessments, or audit outcomes across teams.
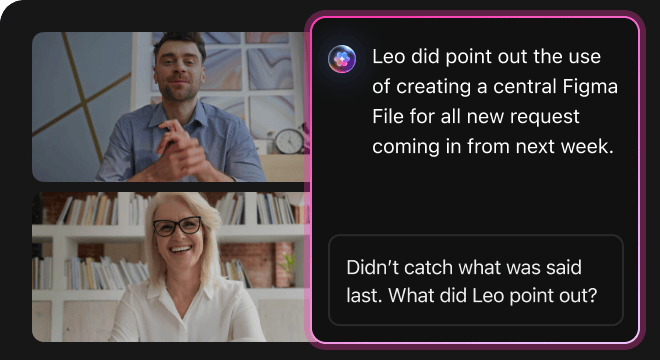
AI Advantages
How AI Prompts Elevate Every Phase of Security Policy Deployment
AI prompts accelerate planning and enable more effective, compliant security strategies.
Instantly Craft Effective Policy Drafts
Security teams develop clear policies quickly, make informed choices, and prevent delays in implementation.
Enhance Compliance and Risk Management
Strengthen adherence to regulations, reduce vulnerabilities, and build policies that satisfy auditors and stakeholders.
Identify Gaps Before They Become Issues
Detect potential oversights early, minimize costly revisions, and improve overall security posture.
Align Teams with Unified Security Goals
Facilitates communication, removes confusion, and accelerates consensus among compliance, IT, and leadership.
Drive Continuous Security Improvement
Encourages innovative controls, adapts to emerging threats, and keeps your policies future-ready.
Integrated AI Assistance Within ClickUp
Transforms AI insights into actionable tasks, ensuring policies move smoothly from concept to execution.
Speed Up Your Security Policy Setup
Cut down mistakes, simplify collaboration, and produce more effective policies using AI support.