تترافق إدارة المشاريع مع العديد من المسؤوليات، والمواعيد النهائية، والنوبات الليلية المتأخرة، والكثير من القهوة.
لحسن الحظ، يمكنك البقاء على رأس العمل مع القليل من المساعدة من صديقك: برنامج إدارة المشاريع .
مع وضع ذلك في الاعتبار، لم يكن التواصل أبسط أو أسهل أو أسرع من أي وقت مضى، مما يؤدي إلى فريق عمل أكثر إنتاجية ونجاحًا.
تساعد إدارة المشاريع عن بُعد مديري المشاريع على ربط الفرق المختلطة وضمان عمل الجميع معًا لتحقيق أهداف المشروع. وفي هذا الصدد، لا يختلف الأمر عن إدارة أي مشروع آخر، باستثناء أن المشروع يتم تنفيذه عن بُعد.
وتثير إدارة وتشغيل فريق العمل عن بُعد مشكلة حساسة: زيادة مخاطر الجرائم الإلكترونية
وبناءً على ما سبق، دعونا نلقي نظرة على أكبر خمسة تهديدات للأمن السيبراني يواجهها مديرو المشاريع اليوم وعشر طرق لمواجهتها!
أكبر 5 تهديدات للأمن السيبراني في عام 2024 الأمن السيبراني يمكن أن يؤدي إلى نجاح أو فشل الأعمال التجارية .
تعمل الشركات على البيانات، والبيانات هي أكثر أصول الشركة قيمة. ومع ذلك، في عالم اليوم الرقمي، أصبحت البيانات أكثر عرضة للهجمات الإلكترونية، ومع ترتيبات العمل الهجين والعمل عن بُعد، أصبح هذا الضعف أكبر.
إن ارتفاع حالات اختراق البيانات واختراقها إلى الافتقار إلى حماية البيانات، وعواقب الجائحة العالمية، وزيادة تعقيد عمليات الاستغلال. أصبحت الشركات الآن أكثر وعياً من أي وقت مضى بالمشاكل التي يمكن أن تتسبب فيها عمليات اختراق البيانات.
كانت إحدى حالات اختراق البيانات التي مهدت الطريق لتشريعات الاتحاد الأوروبي الجديدة هي قضية Wonga Loans. فقد تعرضت شركة قروض يوم الدفع هذه لخرق كبير للبيانات في عام 2017 أدى إلى كشف المعلومات المصرفية لـ 250,000 عميل.
فيما يلي أهم التهديدات الإلكترونية التي يجب أن تكون على دراية بها ونصائح حول كيفية الوقاية منها.
1. رجل في المنتصف
تخيل هذا السيناريو: أنت وزميلك تتحدثان عبر منصة آمنة، ولكن هناك شخص ما يتنصت على محادثتك ويرسل رسائل مزيفة إلى زميلك منك. يا للقرف!
الفكرة وراء ذلك هي أن المخترقين يتمكنون من الوصول إلى البيانات الشخصية والحساسة، ويتلاعبون بالرسائل.
قد يحدث ذلك إذا كنت تستخدم شبكة Wi-Fi عامة غير آمنة. عندما يكون المخترق داخل الموقع غير الآمن، سيتمكنون من الوصول وإرسال برمجيات خبيثة للعثور على البيانات الحساسة. يمكنهم أيضًا التظاهر بأنهم عميل أو شريك تجاري أو أي شخص آخر.
مثال على هجوم رجل في الوسط
في الآونة الأخيرة، حصلت إحدى الجهات التخريبية مؤخرًا على 500 شهادة لمواقع إلكترونية مثل Google و Skype ومواقع بارزة أخرى بفضل اختراق موقع المسجل الهولندي DigiNotar. وباستخدام هذه الشهادات، قام المهاجم بانتحال هوية مواقع ويب جديرة بالثقة في هجوم MITM وسرق بيانات المستخدمين عن طريق خداعهم لتقديم بيانات اعتمادهم على مواقع ويب متطابقة. وأدى الاختراق في النهاية إلى التأثير على حوالي 300,000 حساب بريد إلكتروني إيراني على Gmail وإعلان DigiNotar إفلاسها.
2. حقن SQL الكلاسيكية
لنفترض أنك تستعد لقضاء عطلتك وتريد شراء فستان هاواي. تفتح متصفح الويب الخاص بك وتكتب "فساتين هاواي" في شريط البحث. إذا كان شريط البحث مصابًا عن طريق حقن شيفرة خبيثة، فسيظل يعطيك قائمة بفساتين هاواي، ولكنه سيستخدم سؤالك للعثور على معلوماتك الشخصية. 😬
يستخدم أحد القراصنة جزءًا من شيفرة SQL لتغيير قاعدة البيانات والوصول إلى معلومات قد تكون مهمة في هجوم إلكتروني يُعرف باسم حقن SQL. نظرًا لأنه يمكن استخدامه في أي تطبيق أو موقع ويب يستخدم قاعدة بيانات تستند إلى SQL، فهو أحد أكثر أنواع الهجمات شيوعًا وخطورة.
مثال على هجوم SQL
من بين ضحايا هذا النوع من الهجمات الإلكترونية: سوني بيكتشرز، وتارغت، ولينكد إن، وإبيك جيمز. تعد حالة Cisco من عام 2018 واحدة من أكثر الهجمات شهرة على نطاق واسع. فقد وجدوا ثغرة في حقن SQL في برنامج Cisco Prime License Manager.
تمكن المهاجمون من الوصول إلى الأنظمة التي تم نشر إدارة التراخيص فيها. لكن لا تخف. منذ ذلك الحين، تمكنت Cisco من تصحيح المشكلة.
على الرغم من أن هذه الثغرة قديمة بما يكفي لشربها الآن، إلا أننا ما زلنا لا نستطيع سحقها إلى الأبد. إنه يعتبر أحد أقدم التهديدات الإلكترونية ومع ذلك، لا يزال يسبب العديد من المشاكل.
3. نمو البرمجيات الخبيثة
الأمر كله مرح ولعب إلى أن تقوم بتحميل البرمجيات الخبيثة وتساعد المخترقين في الحصول على جميع بياناتك الشخصية. تجمع البرمجيات الخبيثة جميع الملفات أو البرامج التي تسبب الضرر، وهي تشمل الديدان وأحصنة طروادة والفيروسات وفيروسات الفدية.
بحلول عام 2021, 68.5% من الشركات التي تعرضت لهجمات البرمجيات الخبيثة. تُظهر التقارير أن هذه الزيادة كانت مبنية على زيادة تفشي فيروس كورونا المستجد (COVID-19).
بالإضافة إلى ذلك، ابتعد المجرمون عن حملات برمجيات الفدية الخبيثة الآلية التي ركزت على نطاق واسع إلى عمليات ابتزاز أكثر استهدافًا ضد الشركات الراسخة. وبسبب هذا التغيير، أصبحت برمجيات الفدية الخبيثة أكثر ربحية، مما جذب انتباه العصابات الإجرامية في نهاية المطاف.
وقد أدى الاستخدام المتزايد لهذا الأسلوب الجديد للابتزاز إلى تفاقم انتشار برمجيات الفدية الخبيثة.
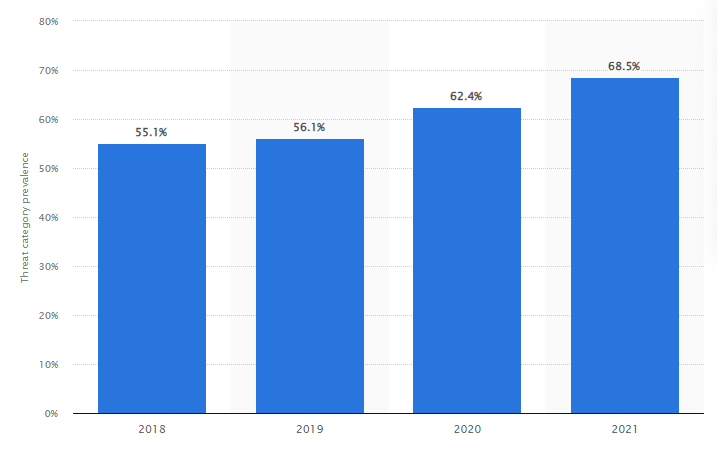
عبر موقع Statistica
مثال على هجوم البرمجيات الخبيثة
أحد أشهر الهجمات كان هجوم هجوم فيروس الفدية WannaCry أن يصيب أكثر من 230,000 جهاز كمبيوتر في يوم واحد وأدى إلى خسارة 4 مليارات دولار.
4. تقنيات التصيد الاحتيالي المتطورة
التصيد الاحتيالي هو شكل من أشكال الهندسة الاجتماعية التي يرسل فيها المهاجم رسالة كاذبة تهدف إلى خداع الشخص للإفصاح عن معلومات شخصية أو تثبيت برمجيات ضارة على البنية التحتية للضحية.
مثال على تقنية التصيد الاحتيالي
تعرضت شركة Ubiquiti Networks، للأسف، لهجوم تصيد احتيالي في عام 2015 كلف الشركة 46.7 مليون دولار. قام المهاجم بتفويض كبير مسؤولي المحاسبة في الشركة بإجراء سلسلة من التحويلات لإتمام عملية استحواذ سرية.
تظاهر المخترق بأنه الرئيس التنفيذي للشركة ومحامي الشركة. قامت الشركة بإجراء 14 عملية تحويل مالي على مدار 17 يوماً إلى حسابات في بولندا والمجر والصين وروسيا.
كانت شركة Ubiquiti على علم بالمشكلة لأول مرة بعد أن تلقت تحذيراً من مكتب التحقيقات الفيدرالي بأن حسابها المصرفي في هونغ كونغ ربما كان هدفاً للاحتيال. وقد مكّن ذلك الشركة من وقف جميع التحويلات القادمة وبذل كل جهد ممكن لاسترداد أكبر قدر ممكن من مبلغ 46.7 مليون دولار، أي ما يقرب من 10% من أموال الشركة التي تم الاستيلاء عليها.
5. هجمات الحرمان من الخدمة المتكررة
هذا النوع من الهجمات الإلكترونية يمكن أن يتسبب في إغلاق الشبكة ويجعل الوصول إليها غير متاح للمستخدمين. يمكن أن يكون للقراصنة أهداف سياسية أو اجتماعية، على سبيل المثال، شن حملة ضد شركة لا تعجبهم أنشطتها.
في بعض الأحيان، يستخدم القراصنة هجمات DDoS لمجرد التسلية والتفاخر بأحدث التقنيات التي طوروها لإسقاط النظام.
مثال على هجوم الحرمان من الخدمة
في فبراير 2020، كانت خدمات أمازون ويب سيرفيسز هدفاً لهجوم هائل من هجمات الحرمان من الخدمة. كان هذا الهجوم هو أشد هجمات الحرمان من الخدمة الموزعة في التاريخ الحديث واستخدم طريقة تسمى انعكاس بروتوكول الوصول إلى الدليل خفيف الوزن غير المتصل (CLDAP) لاستهداف عميل AWS لم يُذكر اسمه.
تم زيادة كمية البيانات التي يتم تسليمها إلى عنوان IP الخاص بالضحية بمقدار 56 إلى 70 مرة باستخدام هذه التقنية، والتي تعتمد على خوادم CLDAP الخارجية الضعيفة. بلغ الهجوم ذروته بمعدل مذهل بلغ 2.3 غيغابايت في الثانية على مدار ثلاثة أيام.
10 طرق للتصدي لتهديدات الأمن السيبراني
أصبح القراصنة أكثر إبداعاً وأكثر إبداعاً ويجعلوننا نتصبب عرقاً.
لمساعدتك في مواجهة هذه التهديدات، إليك عشر طرق لمساعدتك في دفاع وحماية أعمالك من التهديدات الإلكترونية المحتملة.
1. اختر أداة آمنة لإدارة المشاريع وخدمة التخزين السحابي
أدوات إدارة المشاريع ضرورية في الوقت الحاضر، خاصةً لتتبع التقدم المحرز في مشروعك وتحسين تواصل الفريق. ومع ذلك، ليست كل أدوات العمل المتاحة اليوم آمنة.
عندما نقول آمنة، فإننا نعني منصة مزودة بإجراءات التفويض المناسبة للحد من تسرب المعلومات.
قم بتنزيل ClickUp للوصول إليه على أي جهاز وفي أي وقت انقر فوق هو واحد من أكثر أدوات التعاون الآمنة المتاحة اليوم. فهي توفر بيئة آمنة، مع مراعاة أداء التطبيق وتجربة المستخدم بشكل عام.
في الواقع، لقد حصل باستمرار على شهادات امتثال SOC 2 وISO 27001 وISO 27017 وISO 27018. هذه شهادات الأيزو تثبت التزام ClickUp بالحفاظ على حماية بيانات عملائها واستعدادها لدعم العملاء من جميع الأحجام في جميع أنحاء العالم.
ألقِ نظرة على ميزات الأمان الخاصة بها: المصادقة الثنائية كبيرة مسؤولي التسويق في Internxt _، وهي خدمة تخزين سحابية خالية من المعرفة تستند إلى أفضل مستويات الخصوصية والأمان
