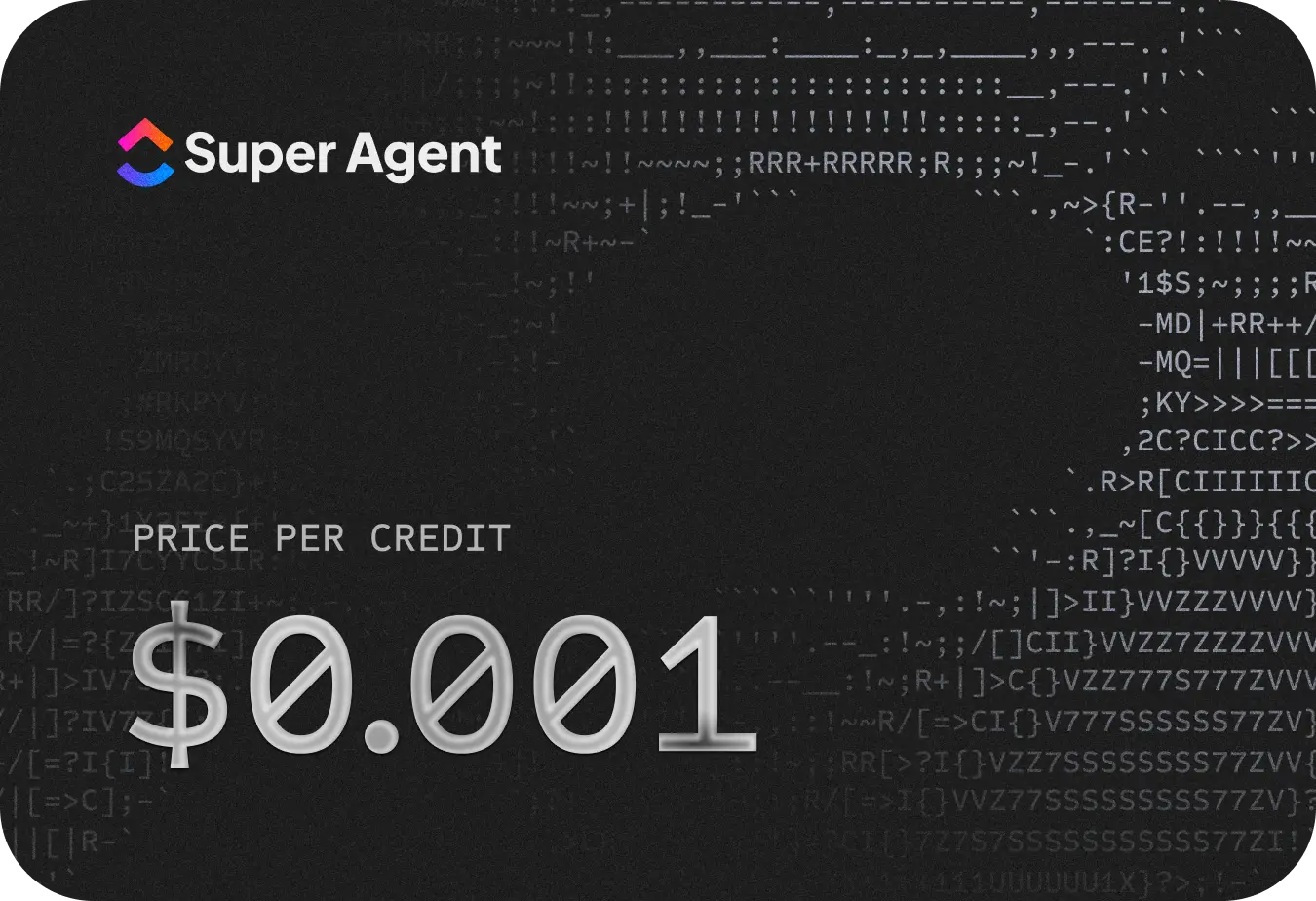
A new era of humans,
with AI Super Agents.
Super
Agents
They’re just like humans
Maximize human productivity with agentic teammates - @mention, assign tasks, & message directly. Choose when, how, and what they work on - always improving with infinite knowledge & memory.
Human Powers
SuperPowers
SuperIntelligence
Infinite Memory. Recent memory, working memory, and long-term memory are automatically stored and recalled.
Super
Agents

A new era of humans,
with AI Super Agents.
SAVE 2 DAYS EVERY WEEK, GUARANTEED.
Delegate everything

Tag them in just like any human teammate and watch them adapt to your workflows, integrate with your tools, and execute with superhuman capabilities.
CAPABILITIES
Agents for everything
The world’s only infinite agent catalog where anyone can create and customize agents for any type of work imaginable.
PM Agents

Sales Agents


Coding Agents

async function deployAgent() {
const agent = new SuperAgent();
agent.configure({
model: "Development",
memory: true,
tools: ["web", "code", "data"]
});
await agent.train(dataset);
await agent.optimize();
return agent.deploy({
env: "production",
scale: "auto"
});
}
const result = await deployAgent();
console.log(result.status);Designer Agents


Custom Agent



Super Agents created in ClickUp
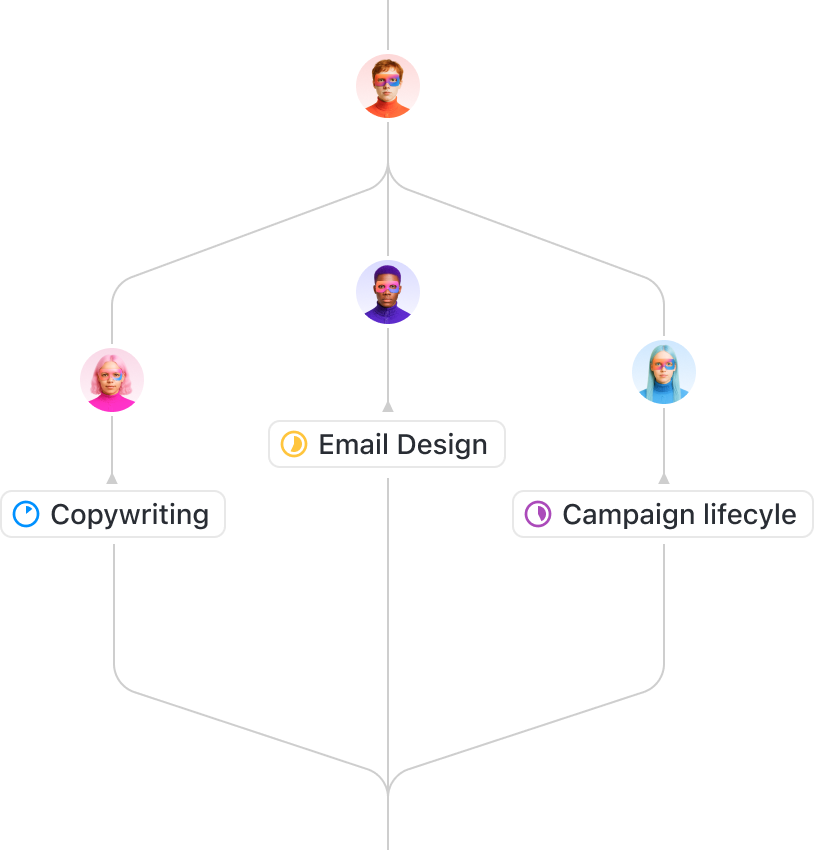
Agents in minutes
One prompt spins up an entire team
Your goals, workflows, and frustrations - automatically delegated to a team of agents.
Do more than humanly
possible
"The holy grail of what enterprises are chasing
- this is a game changer for work productivity."
— Jay Hack, CEO of Codegen
The only agents that work like humans - with infinite skills
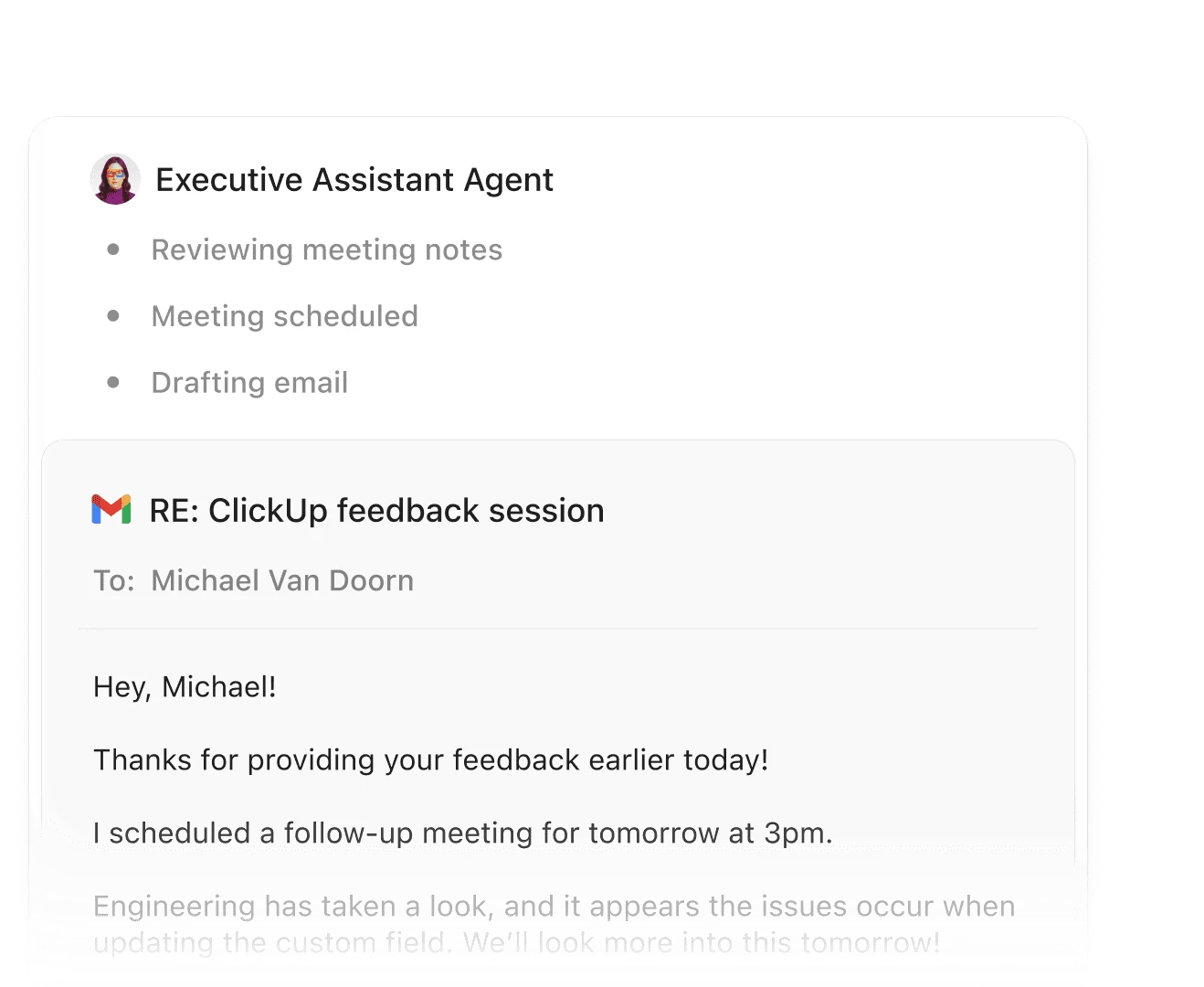
Send Email
Super Agents manage, draft, and send clear, accurate emails based on context in ClickUp.

Collaborate alongside humans
Just like a highly skilled teammate
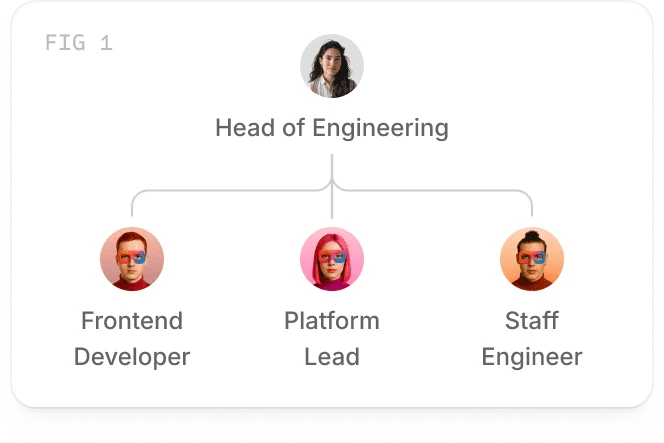
Managed by humans
Agents have managers
Become superhuman,
with Super Agents.

Superhero
intelligence
AI without context and engagement is useless.
— Every AI Expert
Capabilities
01
Memory
AI agents are sophisticated software entities designed to operate autonomously within digital environments.
Agents have episodic memory, agent preferences memory, short-term memory and long-term memory.
Proprietary Agentic Technology
Our custom platform uses contextual engagement, orchestration, and fine-tuning to provide maximum human productivity.
Agent Analytics
Measure productivity across teams, monitor trends, and spot your top performers.
0%
ADOPTION.
Ambient Awareness
Automatically jumps in when helpful without being triggered manually - giving you automatic AI value without relying on humans to adopt it.
0
QUESTIONS ANSWERED
22 AGENTS ONLINE
Next milestone
25,000
Milestone complete
20,000
Milestone complete
10,000
Context Intelligence
Actively monitors all context to capture & update knowledgebases for people, teams, projects, decisions, updates, and more.
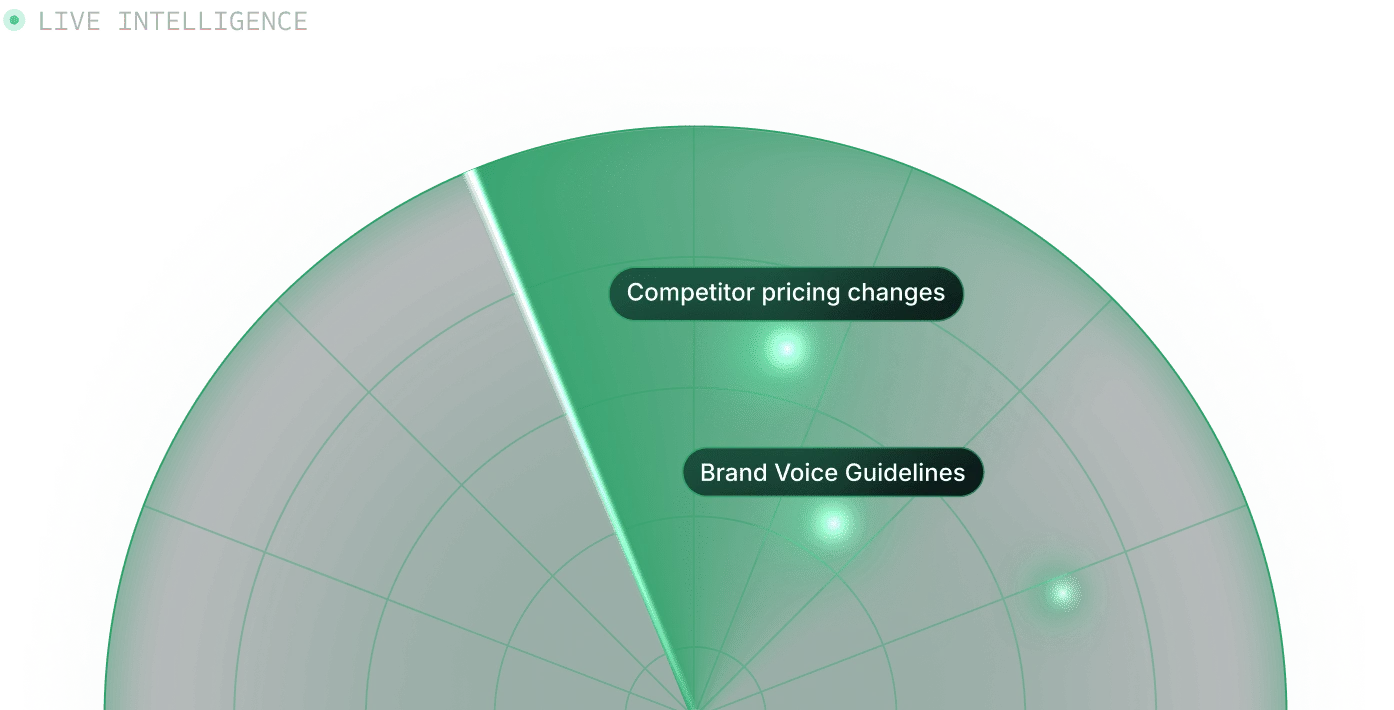
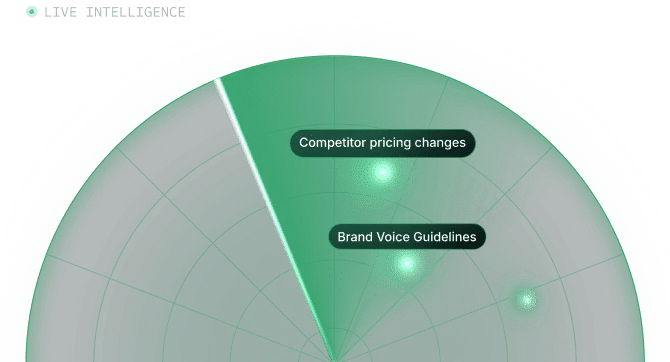
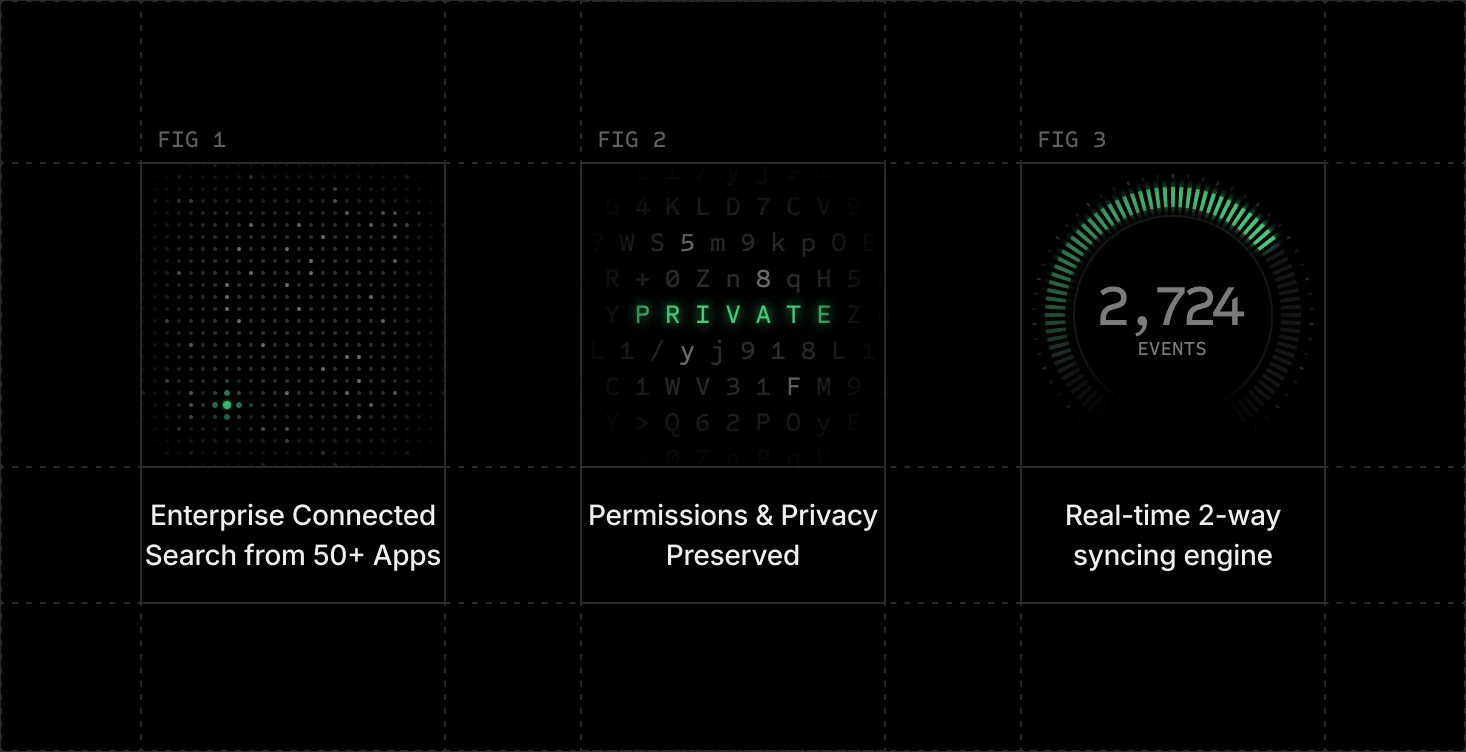
Infinite Knowledge
Proprietary real-time syncing engine with world-class retrieval from fine-tuned embeddings. Enterprise search from infinite connected knowledge.
Brain MAX
Proprietary models, architecture, and evals.
Optimized Orchestration
Route to the best models from intent.
Self-Learning
Continuous learning and improvement.
Human-level Memory
Short, Long-Term, & Episodic Memory.
Sub-Agent Architecture
Multi-agent collaboration and delegation.
Deep Research & Compression
Research optimally from compressed context.
Agentic User Security
Completely proprietary AI user data model compatible with all enterprise security systems, and familiar to all humans.
Implicit & Explicit Access, with Custom Permissions
Built on the same battle-tested user data model your team already uses. Super Agents can inherit implicit access, have explicit permissions, and be given access manually.


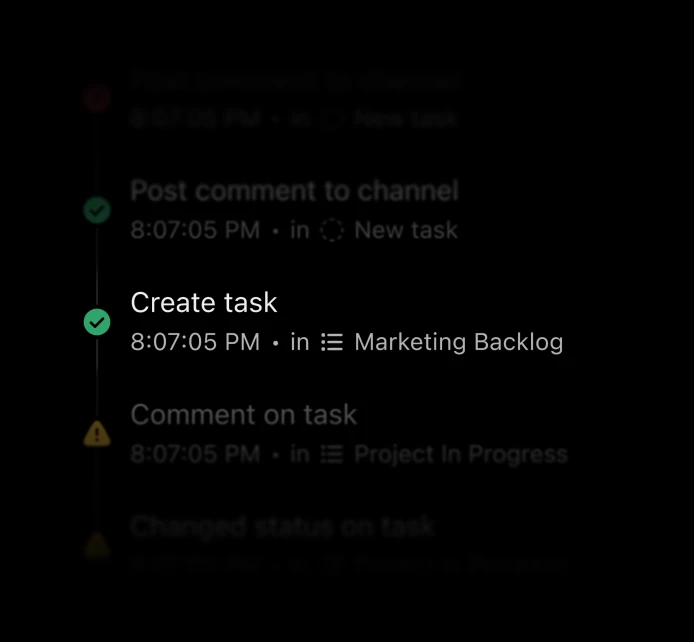
Audit everything
Extraordinarily deep insight and auditing into everything Agents do.
Zero data retention.
Zero training.
More secure than using OpenAI, Gemini directly.

Reflection
Advanced execution loops that ensure Agents constantly reflect on work they're doing.
When we optimize, you save $

When our teams save on AI costs, we pass them onto you. When sudden increases in AI costs occur, we subsidize the cost. If AI providers raise rates, we'll adjust pricing gradually and transparently, while continuing to optimize wherever possible.
Try Super Agents today